Mastering Scapy: A Comprehensive Guide to Network Analysis
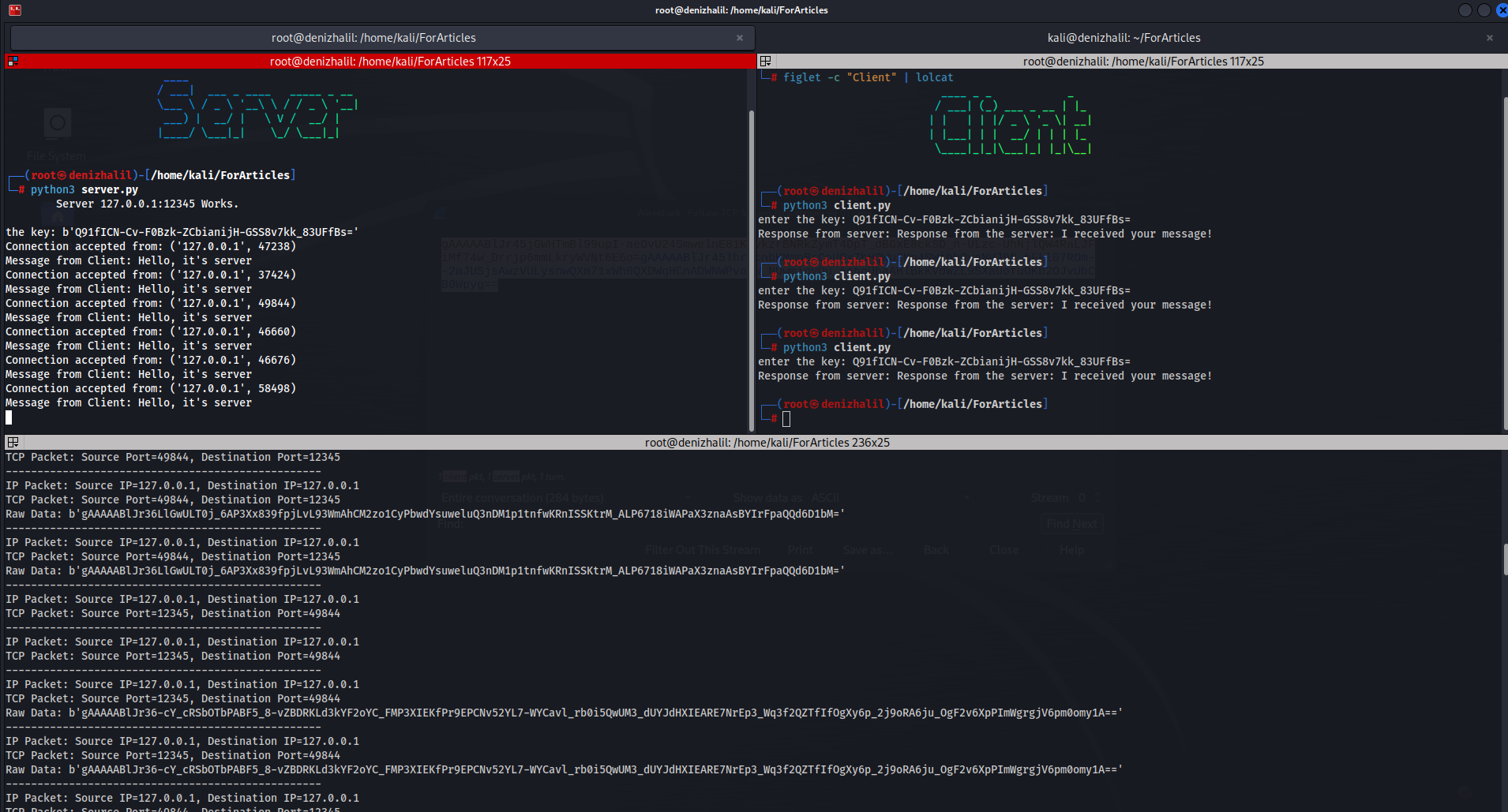
Introduction Welcome to the fascinating world of network analysis, where every packet tells a story, and understanding the intricate dance of digital communication is both an art and a science. This journey you are about to embark upon with “Mastering Network Analysis with Scapy” is not just about learning a tool; it’s about unlocking a deeper understanding of the digital world … Read more