Building Your Own IP Address Information Tool with Python
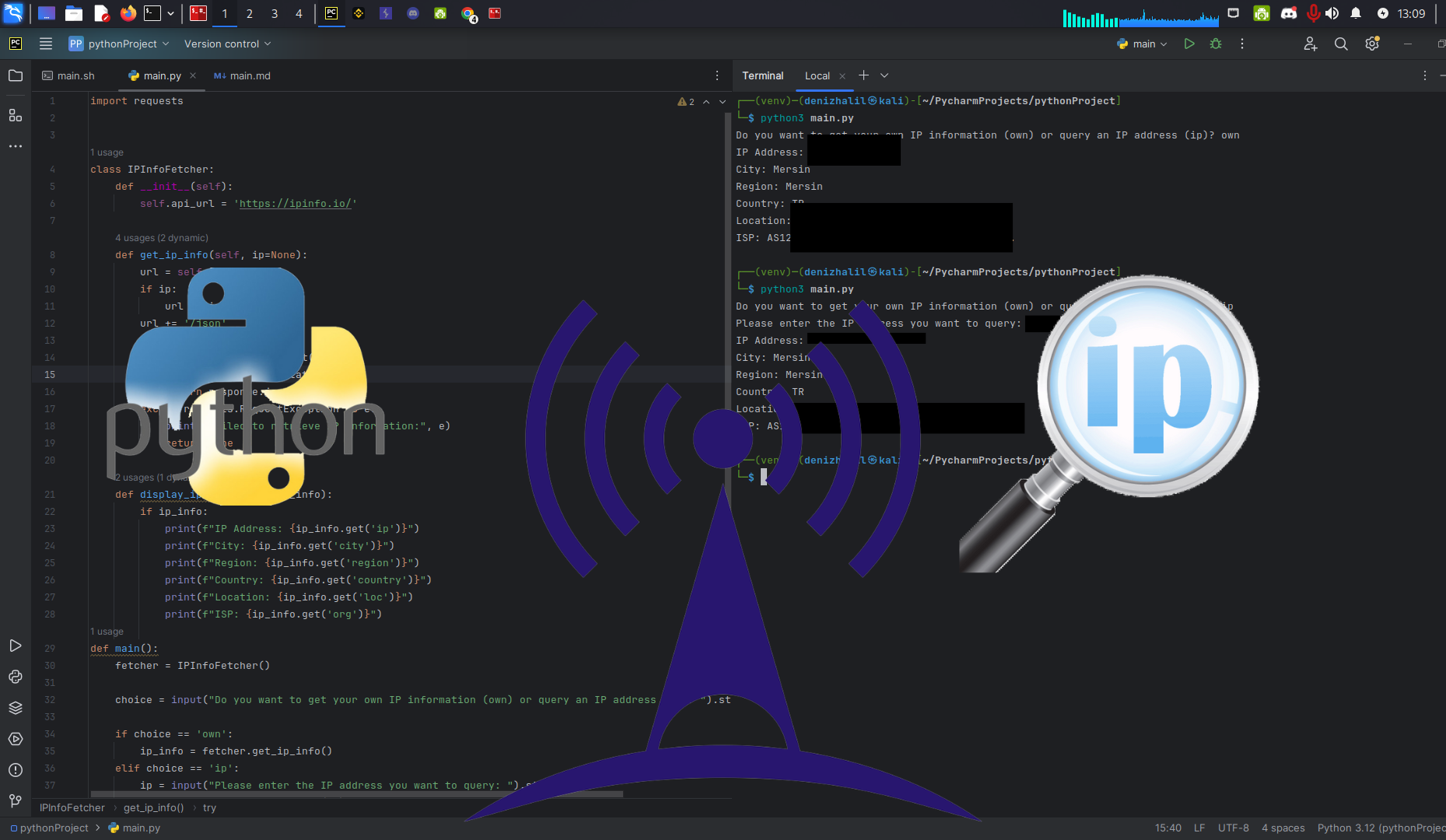
Introduction In today’s interconnected world, understanding IP addresses and their related information is crucial. Whether you’re a network administrator, cybersecurity enthusiast, or just a curious individual, having a tool to fetch IP address details can be incredibly useful. In this article, we’ll explore how to build a Python-based tool to retrieve information about an IP address, including location, ISP, and more. Learning Objectives By the … Read more