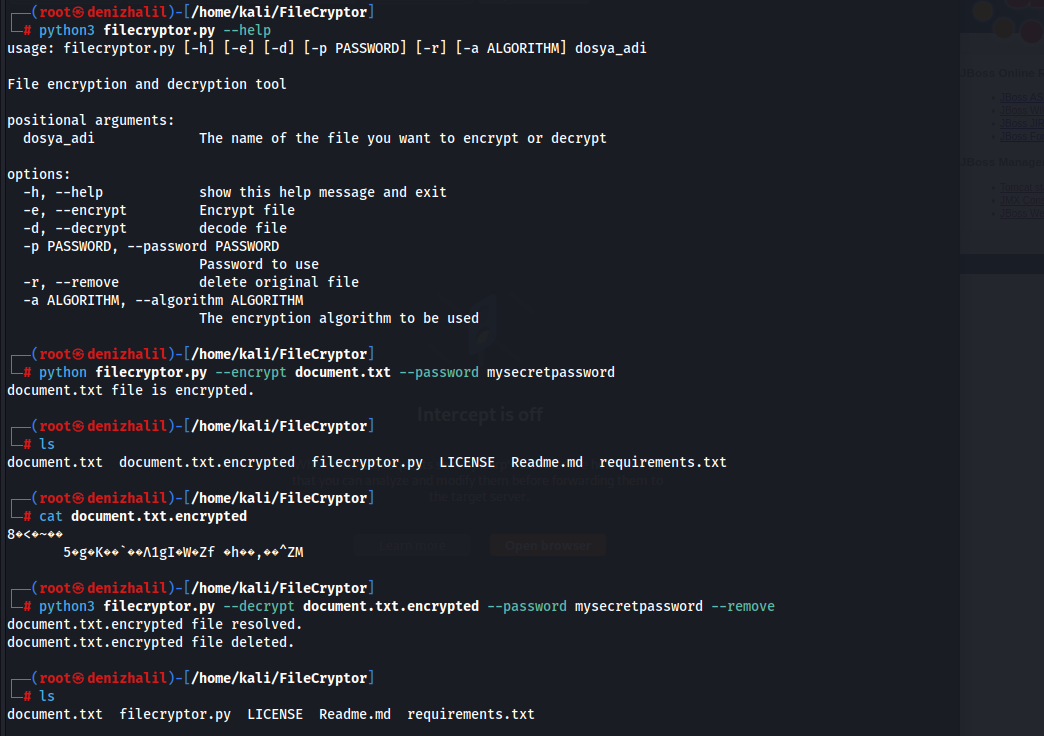
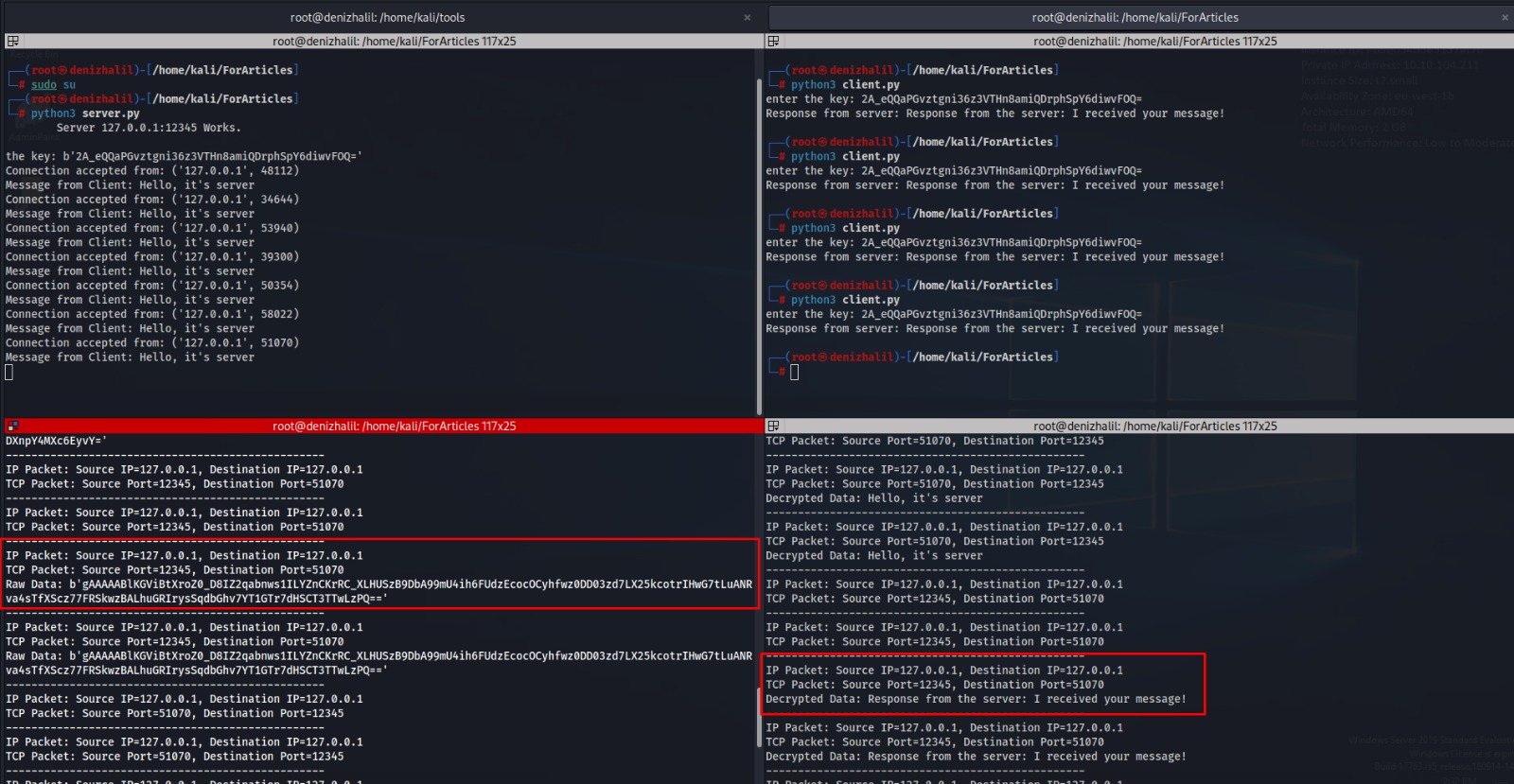
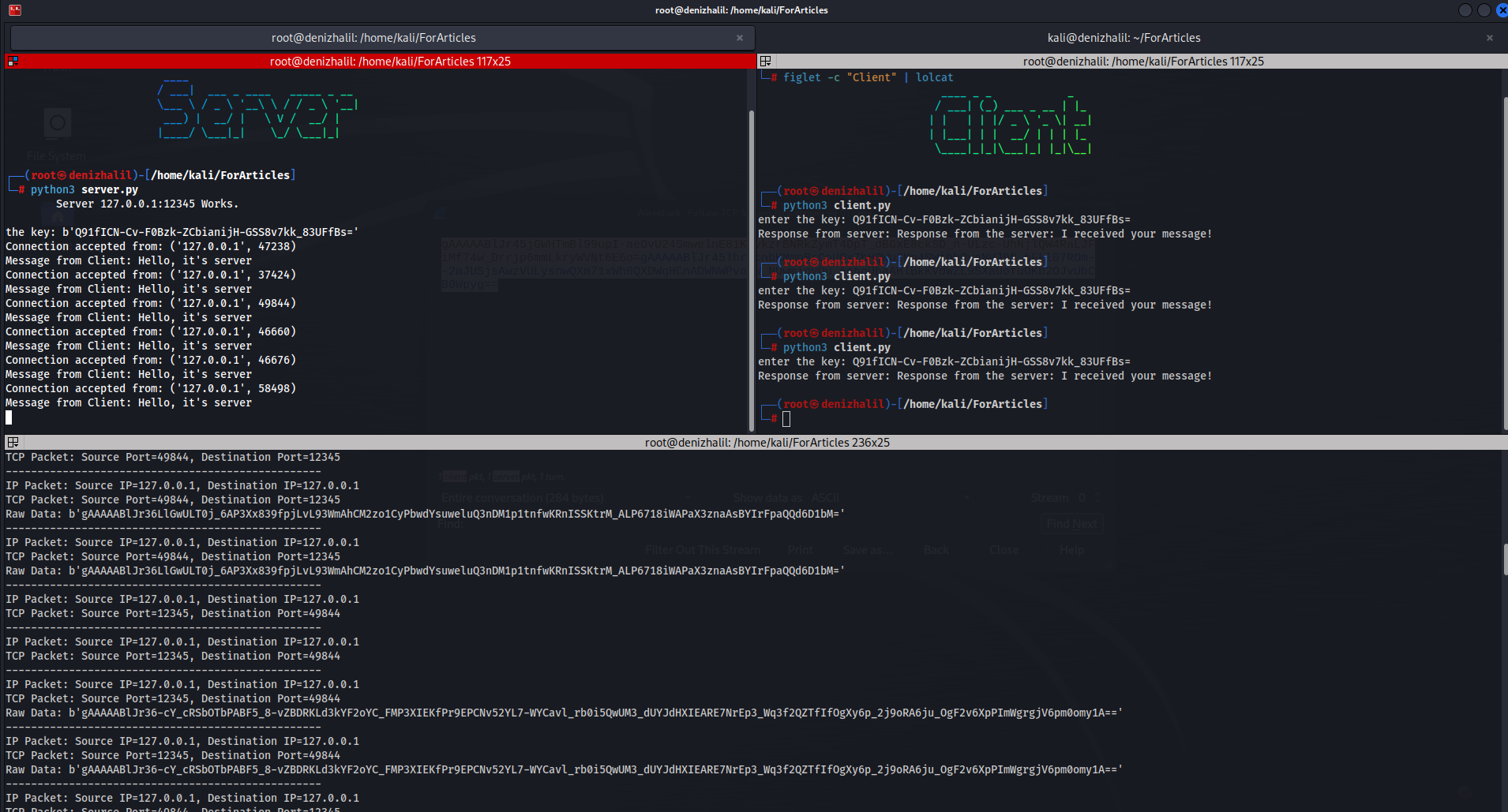
Cryptography Book Recommendations
Introduction Cryptography is the science of using mathematical techniques to protect the confidentiality and integrity of information. In today’s digital world, ensuring data security is of critical importance, and cryptography is one of the most vital tools in this domain. In this article, we will discuss the basic concepts of cryptography, why it is important, and then present some of the best … Read more