Detecting XSS (Cross-Site Scripting) Vulnerabilities with Python
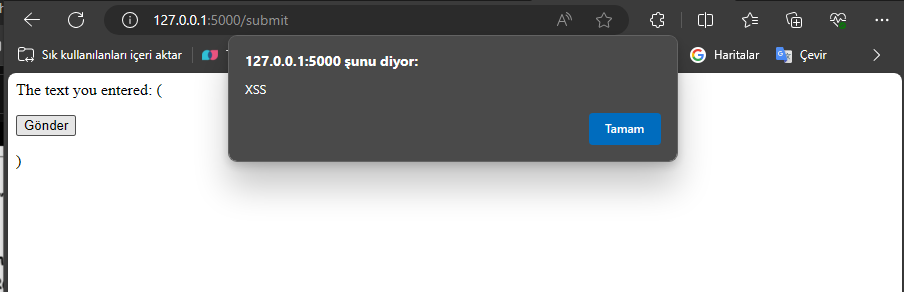
Introduction: This article focuses on how to detect Cross-Site Scripting (XSS) vulnerabilities in web applications using Python. XSS is a serious security flaw that allows attackers to inject malicious scripts into a web page. Such attacks can compromise users’ sensitive data, steal session cookies, or disrupt the normal functioning of a web application. In this article, we will explore the fundamental principles of XSS