Introduction
In today’s complex network structure, secure and flexible access has become more important than ever. Chisel is a powerful tool that responds to this need with its TCP/UDP tunneling capabilities. In this article, we will present some practical examples of how Chisel can be used.
Basic Features of Chisel:
Chisel is an open-source tool developed using the Go language. It can operate in both client and server modes and provides secure connections with SSL/TLS encryption. Here are some of Chisel’s notable features:
- Reverse Connection Tunnels
- Multiple Tunnel Support
- SSL/TLS Encryption
- Simple Command Line Interface
- Cross-Platform Compatibility
Linux Basics for Hackers(Best Seller)
This practical, tutorial-style book uses the Kali Linux distribution to teach Linux basics with a focus on how hackers would use them. Topics include Linux command line basics, filesystems, networking, BASH basics.
Advanced Usage Scenario: Bypassing Firewalls and Conducting Covert Scanning
In this scenario, we will use Chisel to bypass a firewall and perform covert scanning on the target network.
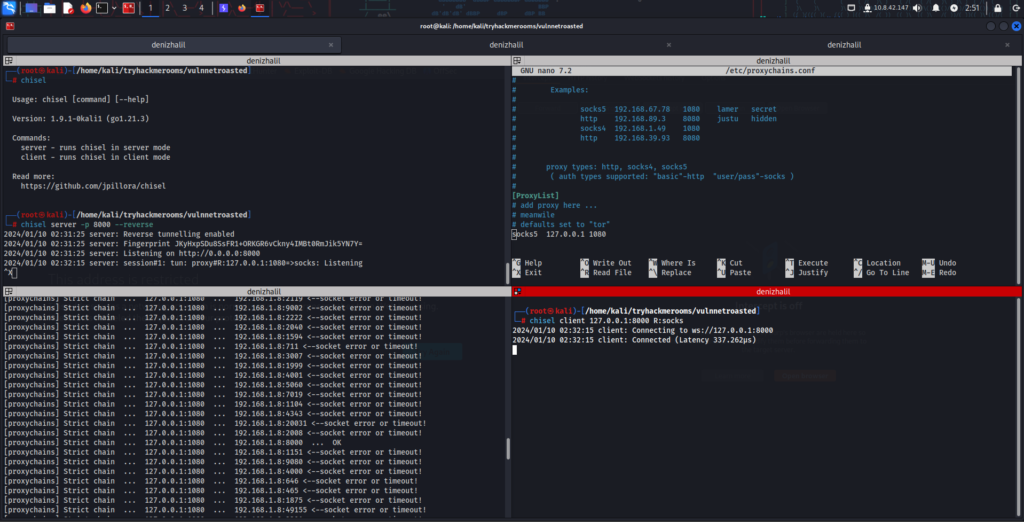
Help Menu
┌──(root㉿denizhalil)-[/home/denizhalil]
└─$ chisel --help
Usage: chisel [command] [--help]
Version: 1.9.1-0kali1 (go1.21.3)
Commands:
server - runs chisel in server mode
client - runs chisel in client mode
Read more:
https://github.com/jpillora/chiselStep 1: Setting Up Chisel Server on the Main Machine
On the main machine, start the Chisel server by running the following command:
$ chisel server -p 8000 --reverseThis command starts a Chisel server that listens on port 8000 and accepts reverse connections.
Step 2: Setting Up Chisel Client on the Target Machine
On the target machine, start the Chisel client with the following command:
$ chisel client <SERVER IP>:8000 R:socksThis command creates a SOCKS proxy tunnel from the target machine to the main machine.
Step 3: Configuring Proxy Settings
On the main machine, go to the bottom of the /etc/proxychains.conf file and edit it. The content of the file should be as follows:
[ProxyList]
socks4 127.0.0.1 1080 # you should change here This setting specifies a SOCKS4 proxy on the local machine on port 1080.
Cyber Security Coffee Mug
Cyber Security Coffee Mug 15oz Black -I’m Cybersecurity Expert – Hacker IT Security Software Engineering Programmer Coder IT Analyst Network Engineer Computer Engineer.
$19.99 on AmazonStep 4: Conducting Covert Scanning
Now, you can perform covert scanning using proxychains. For example, to scan a website, you can use the following command:
$ proxychains nmap -sT -p 80 <TARGET IP>This command uses the nmap tool to scan port 80 on the target IP address, directing all traffic through Chisel.
Conclusion:
Chisel is a powerful and flexible solution for secure network tunneling. Whether for corporate access, remote work, or educational purposes, it is a valuable tool in various scenarios. However, it is important to remember that the use of Chisel should be within ethical standards and legal limits. Necessary permissions should be obtained before intervening in any network.






Wonderful items from you, man. I have take into accout your stuff
previous to and you are just extremely fantastic. I actually like what you have acquired
right here, certainly like what you are saying and the best way wherein you say it.
You make it enjoyable and you continue to care for to stay it
smart. I cant wait to read far more from you. That is actually a
great site.