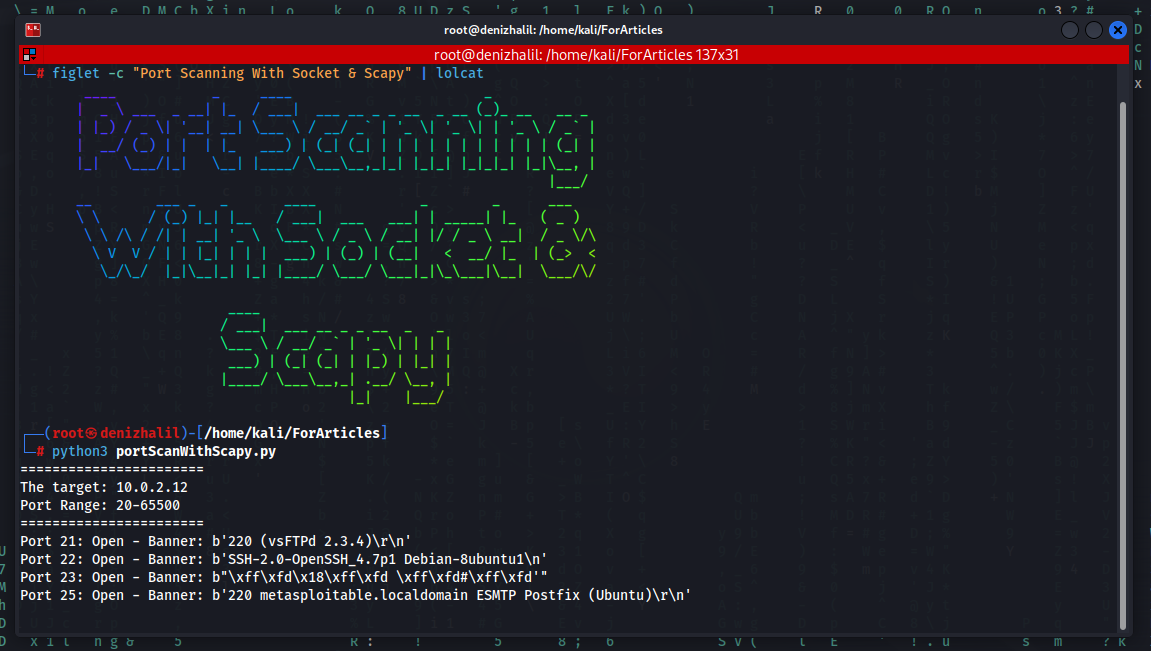
Understanding and Utilizing Microsoft Azure – A Comprehensive Cheat Sheet
Introduction In the rapidly evolving world of cloud computing, Microsoft Azure stands out as a prominent player, offering a plethora of services and solutions for businesses and developers. This article aims to provide a concise yet comprehensive cheat sheet for Azure, helping both newcomers and seasoned professionals navigate its extensive offerings Why Azure? Microsoft Azure is a top-tier cloud … Read more