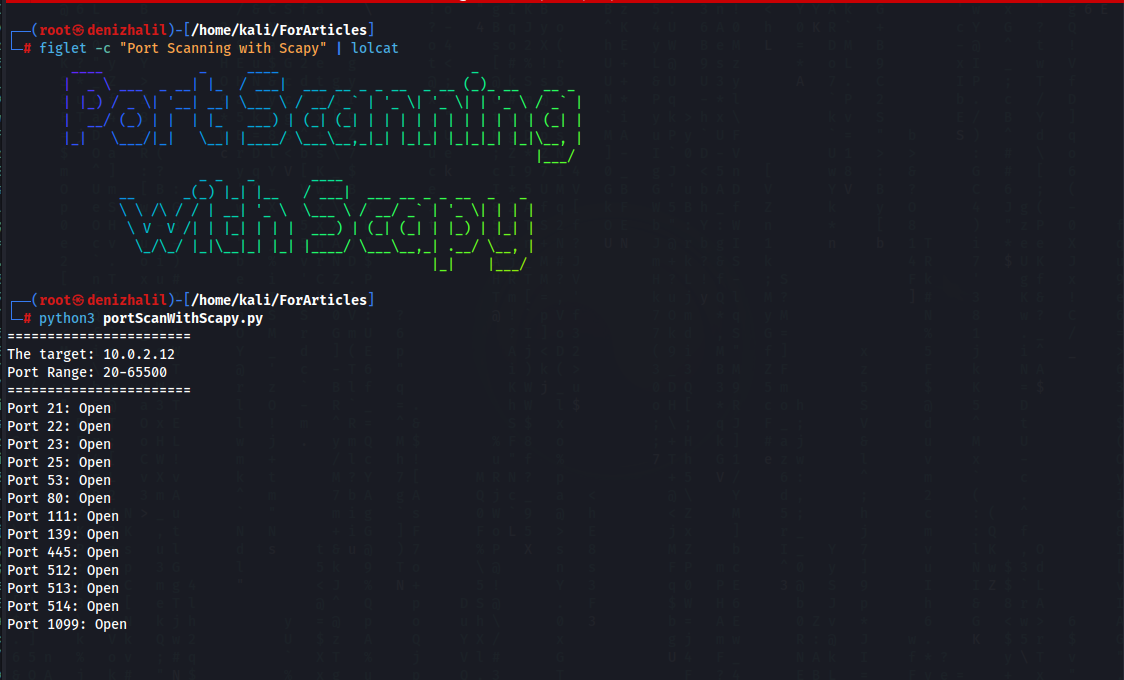
Port Scanning Techniques with Scapy
Introduction In today’s digital landscape, network security has become more crucial than ever. Professionals in this field utilize various tools and techniques to ensure system security and identify vulnerabilities. Among these tools, Scapy, a Python-based packet manipulation library, stands out for its versatility and effectiveness. This article delves into the basic features of Scapy and … Read more