Network security and analysis hold significant importance in modern information technology. Network administrators and security experts use various tools to monitor and understand the traffic on their networks. In this article, we will learn how to use Scapy, a Python-based network packet manipulation library, to sniff and analyze ARP (Address Resolution Protocol) traffic.
What is Scapy?
Scapy is a powerful network packet manipulation library developed in the Python programming language. It serves as a versatile tool for creating, sending, receiving, and analyzing network packets. Scapy has a wide range of use cases, from performing network security tests to data recovery.
What is ARP?
ARP, or Address Resolution Protocol, is a protocol used to resolve an IP address to a physical MAC (Media Access Control) address. It plays a crucial role in local networks by allowing devices to find each other. ARP packets can be classified into two main types: ARP request and ARP reply.
What is ARP Sniffing?
ARP sniffing involves listening to and analyzing ARP traffic on a network. This is an essential step to understand which devices are communicating on the network. ARP sniffing can also be used for detecting network attacks and troubleshooting network issues.
How to Perform ARP Sniffing with Scapy?
Performing ARP sniffing using Scapy is relatively straightforward. Here is a step-by-step guide:
Step 1: Install the Prerequisites
Before using Scapy, you may need to install it on your Python environment and system. Additionally, you might require administrative or root privileges, as listening to network traffic may require special permissions.
$ pip3 install scapyStep 2: Import Scapy
Import Scapy into your Python code:
from scapy.all import ARP, sniff
Step 3: Write the ARP Sniffing Code
The following code is used to sniff ARP traffic and print the information to the screen:
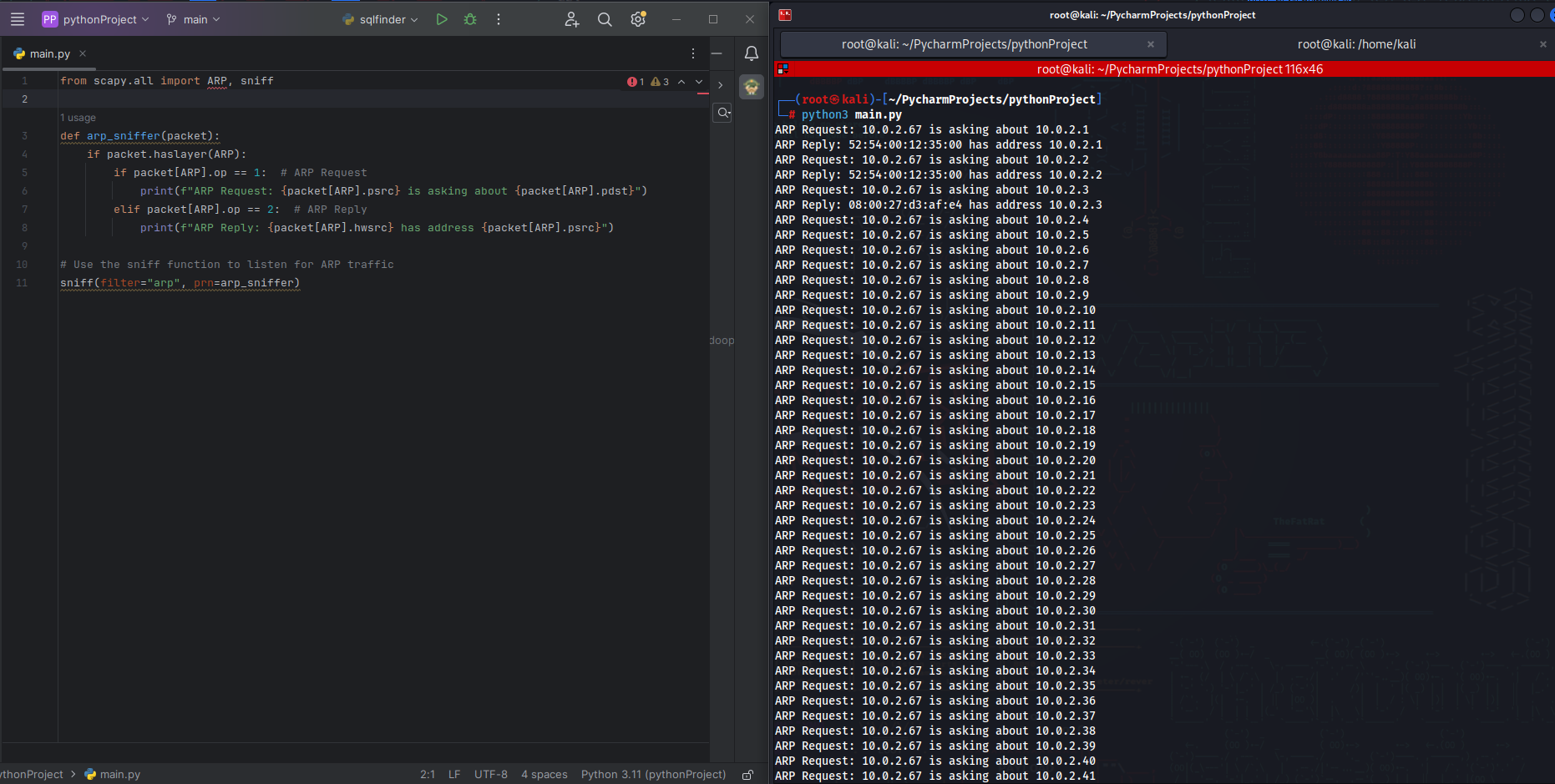
def arp_sniffer(packet):
if packet.haslayer(ARP):
if packet[ARP].op == 1: # ARP Request
print(f"ARP Request: {packet[ARP].psrc} is asking about {packet[ARP].pdst}")
elif packet[ARP].op == 2: # ARP Reply
print(f"ARP Reply: {packet[ARP].hwsrc} has address {packet[ARP].psrc}")
# Use the sniff function to listen for ARP traffic
sniff(filter="arp", prn=arp_sniffer)Step 4: Run the Code
Run the Python script in your terminal or command prompt.
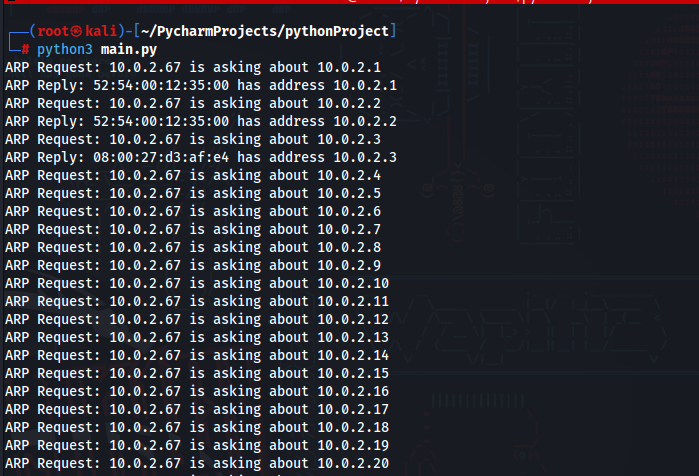
Step 5: Examine the Results
After running the code, you should see ARP traffic displayed on your screen. The output will include information about ARP requests and replies.
Conclusion
In this article, we have learned the basics of performing ARP sniffing using Scapy. Listening to ARP traffic provides network administrators and security experts with insights into their networks, helping them understand and protect their assets. However, it is crucial to use such tools legally and ethically and obtain proper permissions. Additionally, exercise caution when analyzing network traffic, as these operations can pose potential security risks.
Remember that gaining more knowledge and experience in network security is always beneficial. Tools like Scapy can serve as excellent starting points for learning in this field.