Advanced DOS Tool With Python: DoSinator
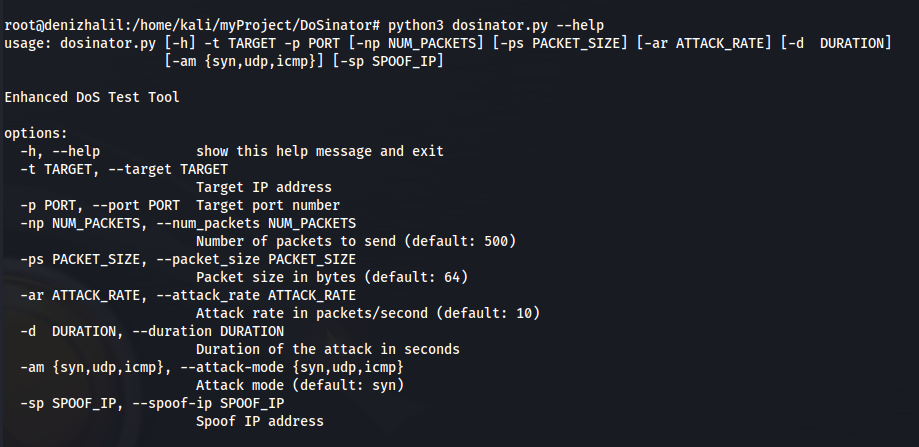
Introduction DoS (Denial of Service) attacks are commonly used and effective types of attacks against network services. In this article, we will walk through the step-by-step process of creating DoSinator, a Python-based tool for simulating and testing DoS attacks. With its powerful and flexible features, DoSinator has gained attention in the field of network security … Read more