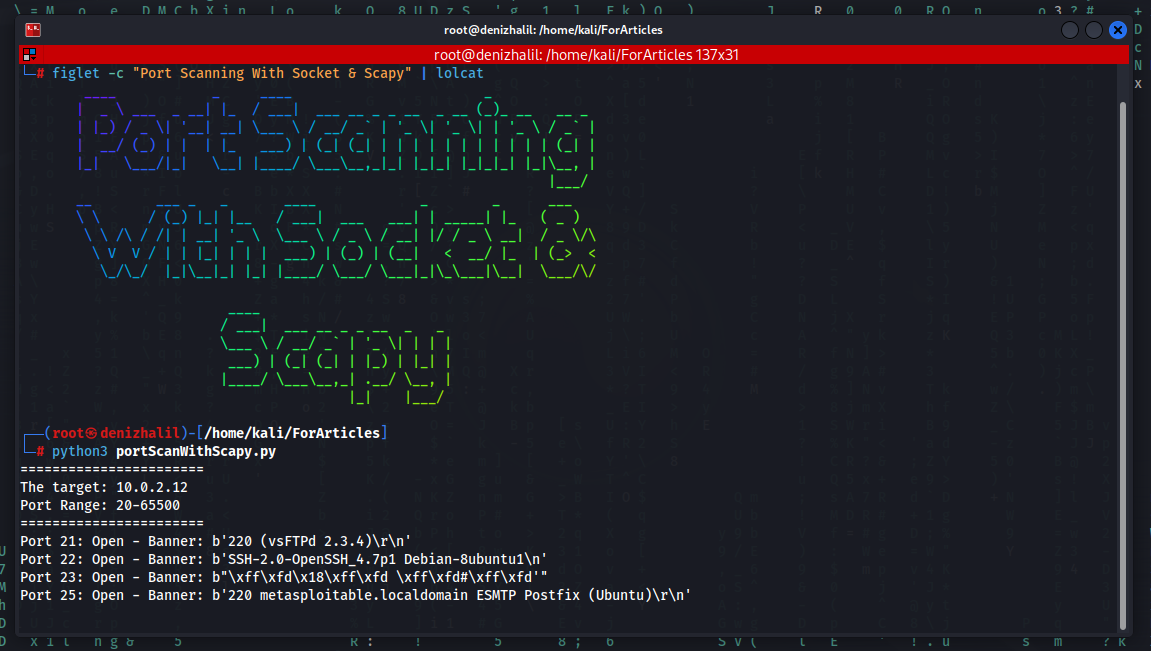
Developing Research Skills in Cybersecurity
Introduction Cybersecurity is a rapidly evolving field that plays a critical role in safeguarding digital systems and sensitive data from a wide range of threats. In this article, we will explore the essential research abilities required in the realm of cybersecurity, specifically focusing on “Developing Research Skills in Cybersecurity.” We’ll discuss how professionals can develop … Read more