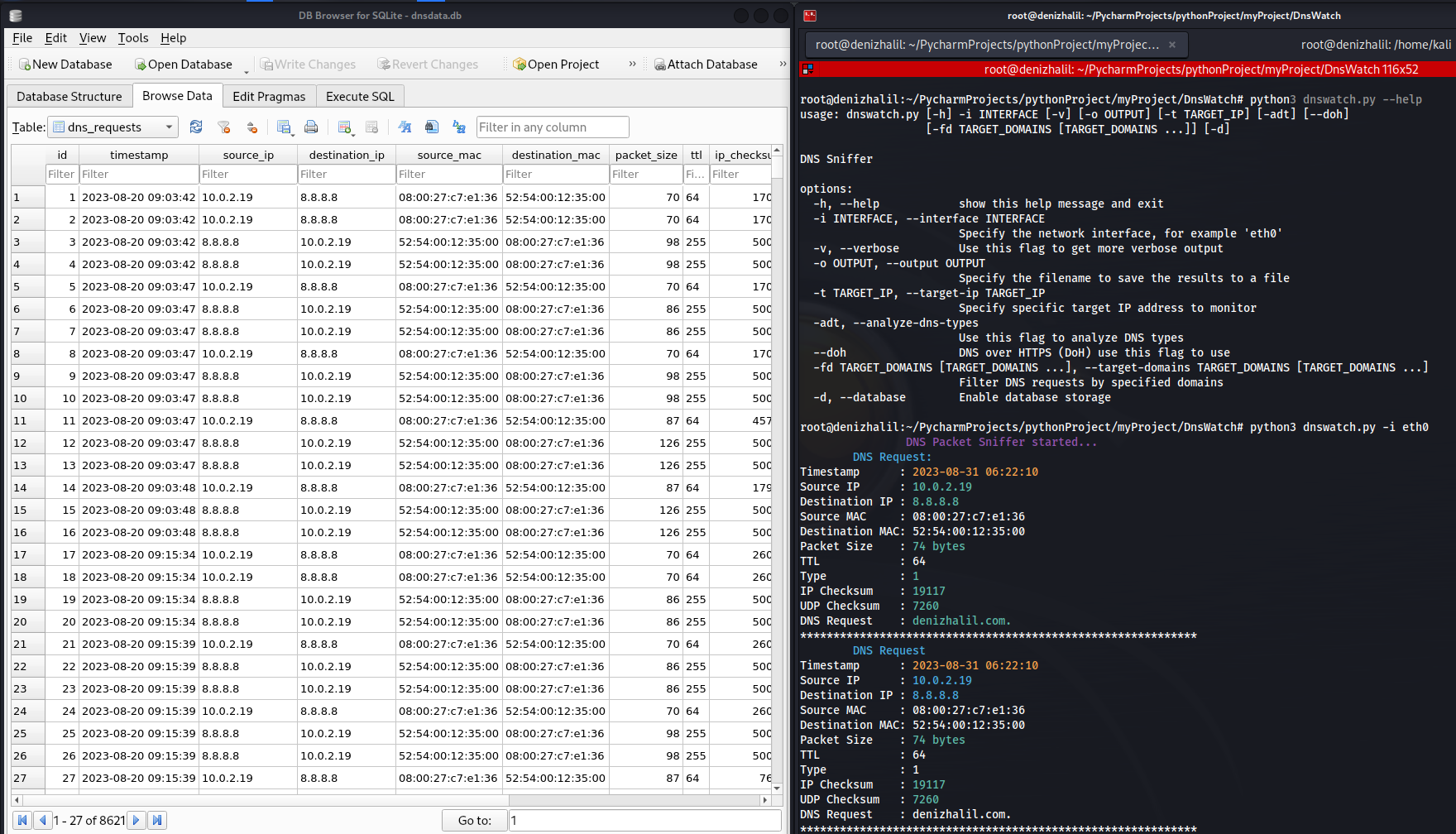
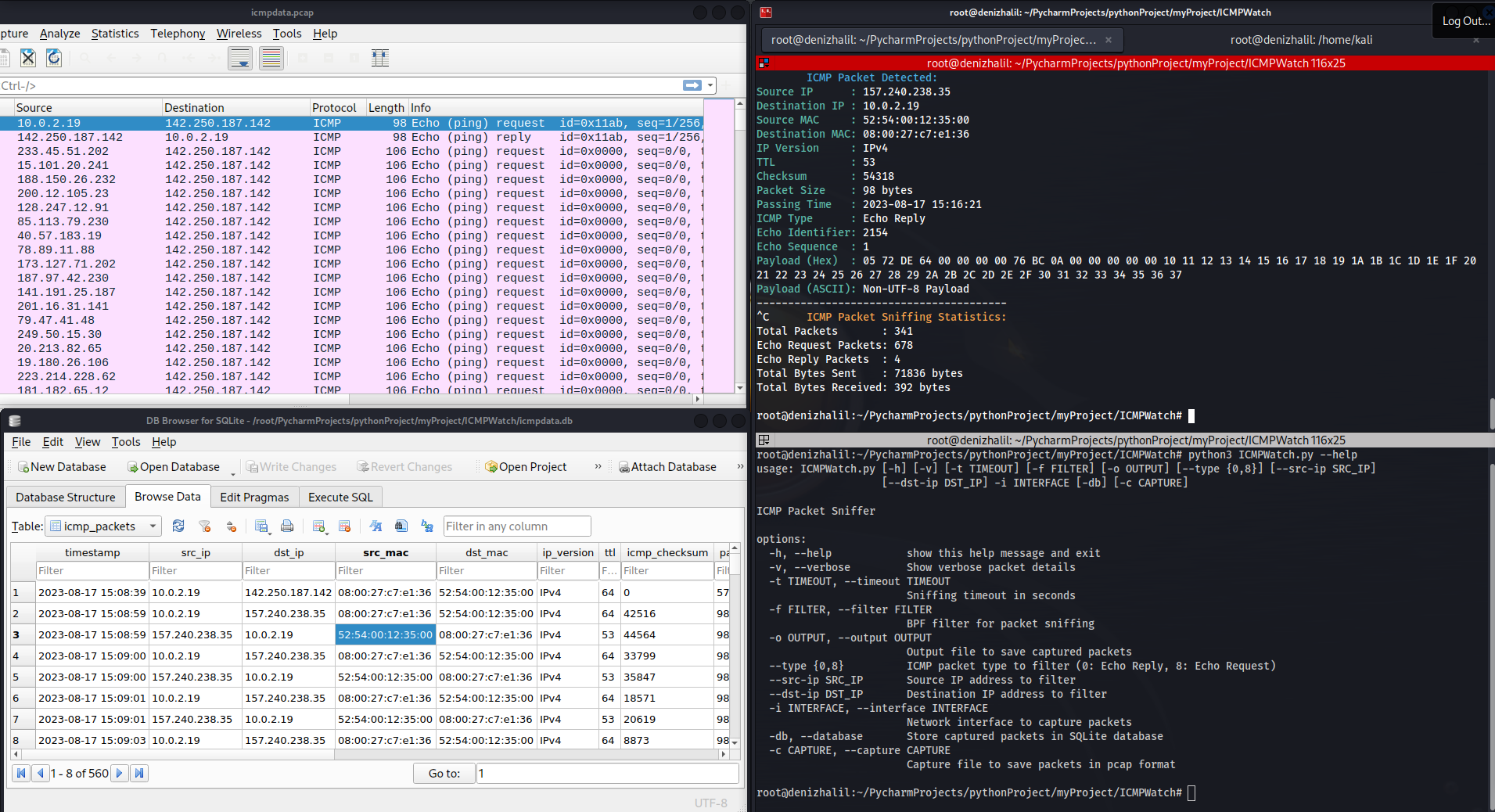
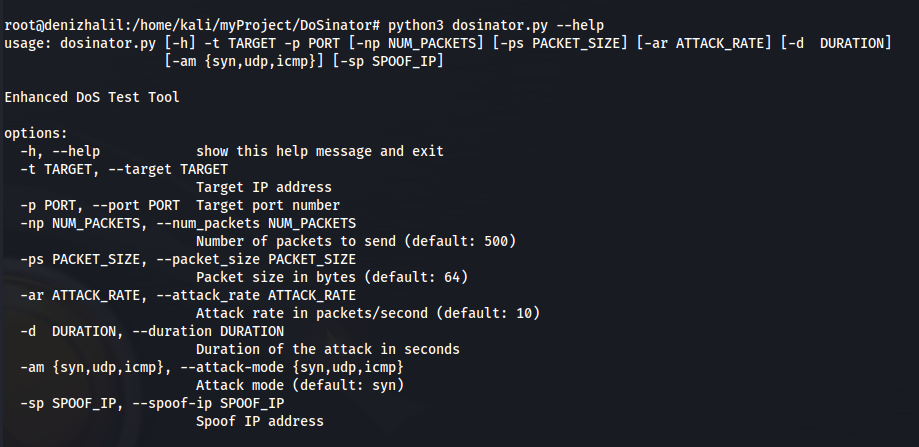
DNSWatch – DNS Traffic Sniffer and Analyzer
DNSWatch is a Python-based tool that allows you to sniff and analyze DNS (Domain Name System) traffic on your network. It listens to DNS requests and responses and provides insights into the DNS activity.And before we start the article, we recommend you to read our article called what is dns and how does it work.Note: … Read more