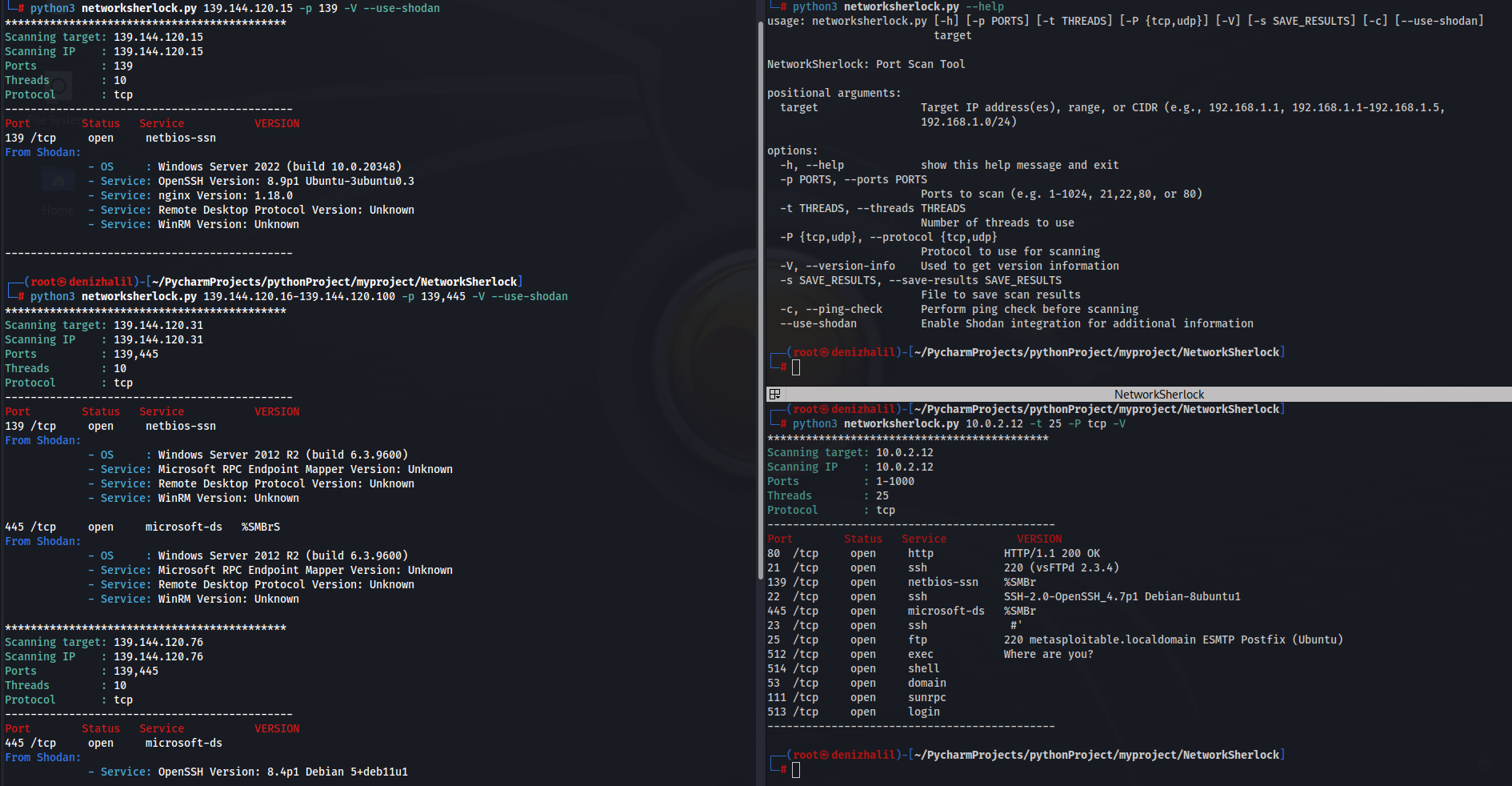
Introducing New Features in NetworkSherlock
🎉 Hello NetworkSherlock Community! We’re thrilled to announce some exciting new updates to NetworkSherlock that are sure to enhance your network scanning and analysis experience. Our latest version includes Shodan Integration, one of the most requested features, along with several other improvements! What’s New? Usage How to Get Started? Your Feedback Matters We’re always looking to improve NetworkSherlock and we’d