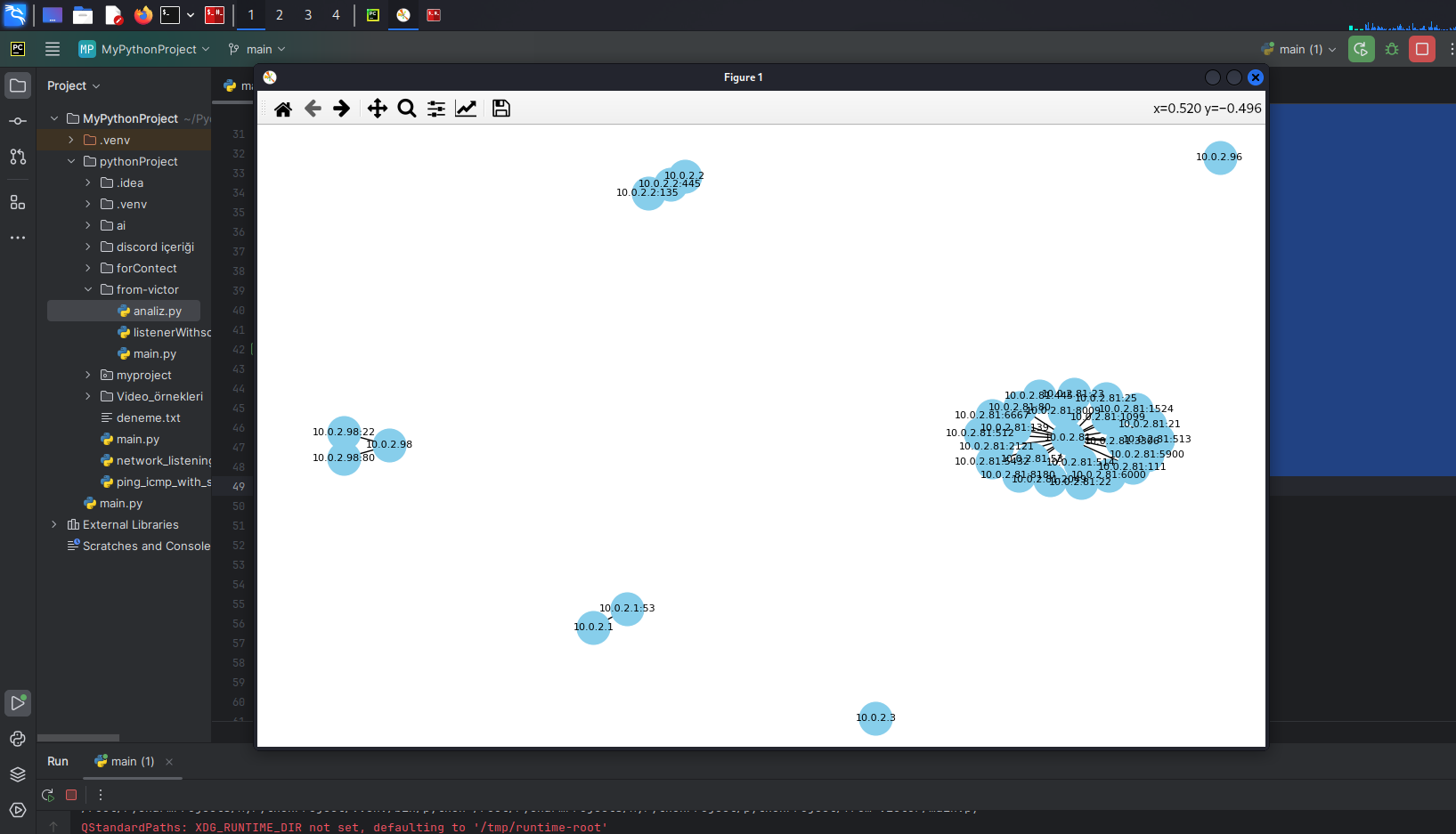
Network Traffic Monitoring and SSH Detection with Python
Introduction Network security is one of the most critical priorities in the digital world. Ensuring network security involves not only protecting against external attacks but also detecting suspicious activities occurring internally. Effective network traffic monitoring and SSH tunneling detection are crucial in achieving this. Techniques like tunneling can be used to bypass security measures or leak data. In