Introduction
In the ever-evolving digital landscape, understanding and preventing ransomware has become a cornerstone of cybersecurity education. “Ransomware: The Anatomy of Digital Threats and Its Role in Education” delves into this critical aspect, offering insights into how ransomware operates and its profound impact on individuals and organizations. Our focus on ransomware prevention education stems from the urgent need to equip people with knowledge and tools to combat these digital threats effectively. As ransomware continues to evolve, becoming more sophisticated and damaging, it’s more important than ever to understand its mechanisms and the best practices for defense.
Structure and Mechanism of Ransomware
Ransomware attacks are known for being particularly cunning and destructive among malware. These malicious programs can infiltrate a system through various methods and then inflict serious damage.
Methods of Spread
- Phishing Emails: One of the most common methods of spread involves phishing emails containing malicious attachments or links.
- Fake Downloads: Websites that lure users into downloading fake programs that appear legitimate but contain malware.
- Weak Network Security: Security vulnerabilities allow attackers to penetrate systems via the network.
Key Elements
- Encryption: Ransomware typically uses strong encryption algorithms like AES and RSA, making it nearly impossible to retrieve encrypted files without the corresponding key.
- Ransom Demand: Following an attack, victims usually encounter a ransom note detailing how to recover the encrypted data and where to send the ransom payment, often demanded in cryptocurrency.
- Anonymity: Attackers often prefer hard-to-trace cryptocurrencies like Bitcoin and communicate over anonymous networks like Tor.
Impacts
- Data Loss: Recovery of encrypted data is generally not feasible, leading to significant data loss.
- Disruption of Business Continuity: In corporate environments, ransomware attacks can seriously impact business continuity.
- Cost: Beyond the ransom payments, the cost of cleaning up the attack and restoring systems can be substantial.
Prevention Methods
- Education and Awareness: Educating users about phishing and social engineering tactics.
- Backup Strategies: Regular and secure data backups can reduce the risk of data loss.
- Up-to-date Security Measures: Antivirus programs and network security solutions provide protection against ransomware threats.
RansomwareSim: A Tool for Education and Awareness
RansomwareSim is a tool designed to understand the effects of ransomware attacks and develop defense strategies. This simulation tool helps users comprehend the dangers of ransomware and the methods of prevention.
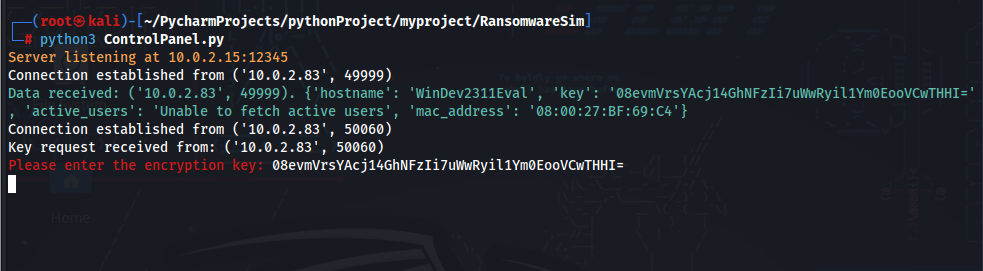
Features
- File Encryption Simulation: Encrypts files in a specified directory to mimic a real ransomware attack.
- Command and Control Server Communication: Demonstrates simulated communication with a command and control server.
- Decryption and Restoration: Shows how encrypted files can be decrypted with the correct key.
- Desktop Alerts and README File: Notifies users of the attack with an alert and creates a README file on the desktop.
Educational Scenarios
RansomwareSim can be used in various educational settings:
- Cybersecurity Workshops: Teach students the basics of ransomware.
- Simulation Training for IT Professionals: Offer real-time attack simulations to IT teams.
- Corporate Awareness Programs: Educate corporate employees about ransomware threats.
- Emergency Simulation Exercises: Test IT teams’ responses to ransomware attacks and develop emergency plans.
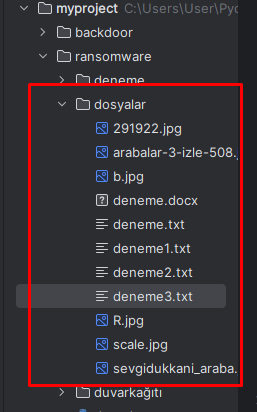
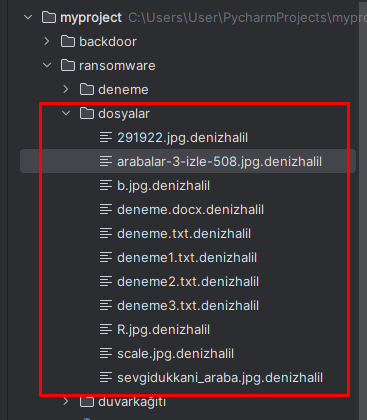
Conclusion
Ransomware poses a significant risk in the ever-evolving landscape of cyber threats. Being prepared against such threats is vital for preventing data loss and minimizing the impacts of security breaches. Tools like RansomwareSim play a crucial role in raising awareness against these threats and in developing effective defense strategies.