Introduction
In today’s digital landscape, information security is paramount. Networks are complex highways transporting sensitive data, making their protection a critical concern. This article provides an in-depth look at password sniffing, a potent capability within the Metasploit Framework (msfconsole). Password sniffing involves intercepting usernames, passwords, and other sensitive information by monitoring network traffic. However, it’s crucial to remember the ethical and legal implications. Unauthorized password sniffing can lead to serious legal repercussions. The information presented here should only be used for security testing on networks and systems where you have explicit authorization. This guide will help you identify weak passwords and vulnerabilities within your authorized networks, enabling you to strengthen your security posture. Remember, responsible and ethical use of this knowledge is paramount.
Learning Objectives
By the end of this article, you will have gained proficiency in the following areas:
- Understanding the concept of password sniffing and its impact on network security.
- Performing the necessary preparations for password sniffing using Msfconsole.
- Identifying and configuring the network interface and enabling “promiscuous mode.”
- Comparing and selecting the appropriate sniffer modules in Msfconsole (psnuffle, tcp sniffer, etc.).
- Configuring the selected sniffer module and setting the necessary parameters (INTERFACE, FILTER, FILE).
- Starting, stopping, and running the sniffer in the background on Msfconsole.
The Logic Behind Password Sniffing with Msfconsole
Msfconsole stands as a powerful and versatile penetration testing platform, a favorite among cybersecurity professionals and ethical hackers. It offers a broad spectrum of features designed for assessing and improving security, and password sniffing is just one of its many capabilities. This technique fundamentally relies on passively monitoring network traffic, acting as a silent observer. Under normal circumstances, a network card is designed to only listen to and process traffic specifically addressed to it. However, when the network card is placed in “promiscuous mode,” it transcends this limitation and begins capturing all network traffic passing through the network segment.
Msfconsole provides a range of specialized tools and modules for dissecting this captured traffic. These tools are designed to extract potentially sensitive information, such as usernames, passwords, email addresses, credit card numbers, and other confidential data. These modules are protocol-aware, meaning they can analyze traffic from a variety of protocols, including HTTP, FTP, POP3, IMAP, SMTP, and many others. To identify and extract relevant data, these modules frequently employ regular expressions to search for specific patterns that often indicate the presence of sensitive information within the captured network packets. The power of these modules lies in their ability to automate the process of sifting through vast amounts of network data to pinpoint potential security vulnerabilities.
Alright, here’s an expanded version of the “Let’s Sniff Passwords” section, providing more detail and context:
Let’s Sniff Passwords with Msfconsole: A Step-by-Step Guide
The following steps provide a detailed, practical walkthrough of how to use Msfconsole to listen for password traffic on a network where you have explicit authorization to conduct security testing. It’s important to reiterate that performing these actions without proper authorization is illegal and unethical. This guide is purely for educational and authorized security assessment purposes.
1. Launch msfconsole:
The first step is to start the Metasploit Framework console. Open your terminal and type:
msfconsole
This command will initialize the Msfconsole environment, loading all the necessary modules and libraries. Be patient, as this process may take a few moments. Once loaded, you’ll see the msf6 > prompt, indicating that Msfconsole is ready to accept commands.
2. Select a sniffer module:
Metasploit offers a variety of sniffer modules, each with slightly different capabilities. To find suitable modules, you can search using the keywords “sniffer” or “capture“. Type the following command into the msfconsole
search sniffer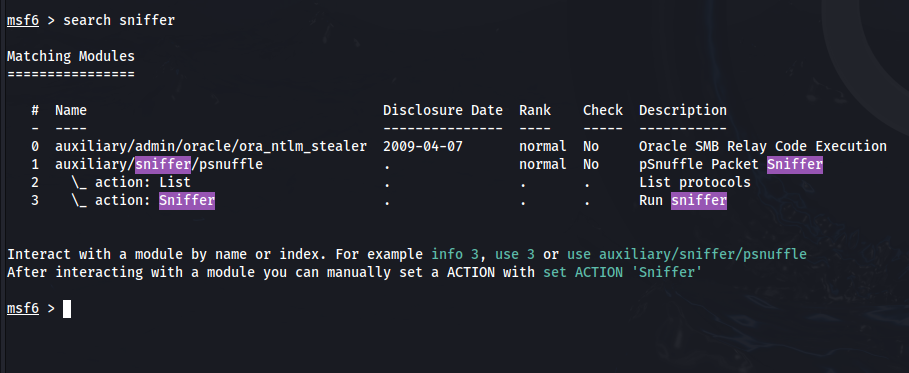
This will display a list of available modules. Carefully review the descriptions to determine which module best suits your needs. Some of the commonly used modules include:
(Here you would list the modules as you have in the original, but you could add a very brief description of what makes each one suitable for different scenarios)
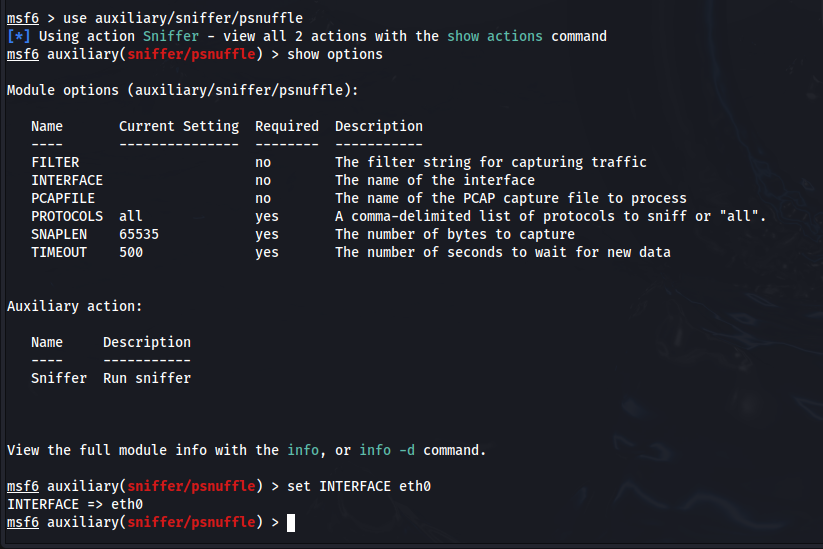
3. Configure the module:
Once you’ve selected a module, you need to tell Metasploit that you want to use it. For example, if you chose auxiliary/sniffer/psnuffle, you would type:
use auxiliary/sniffer/psnuffleThis will display a list of configurable parameters. The most crucial option is usually the network interface to listen on (INTERFACE). To set the interface, use the following command, replacing eth0 with the actual name of your network interface
set INTERFACE eth0Identifying Your Network Interface:
To determine the correct interface name, use the ifconfig (on older systems) or ip addr (on newer systems) commands in a separate terminal window. The output will list all available network interfaces along with their associated IP addresses and other information. Look for the interface that is actively connected to the network you wish to monitor.
Other important options might include:
FILTER: TheFILTERoption allows you to use BPF (Berkeley Packet Filter) syntax to selectively capture traffic based on specific criteria. This is extremely useful for focusing on traffic of interest and reducing the amount of captured data. For example, to filter traffic from a specific IP address, you would use:set FILTER host 192.168.1.100. You could also filter by port number (e.g.,set FILTER port 80to capture HTTP traffic). BPF syntax can be complex, so consult online resources for more advanced filtering techniques.FILE: If you want to save the captured traffic to a file for later analysis, use theFILEoption. For example:set FILE captured_traffic.pcap. The captured data will be saved in PCAP format, which can be opened with tools like Wireshark.
4. Start the sniffer:
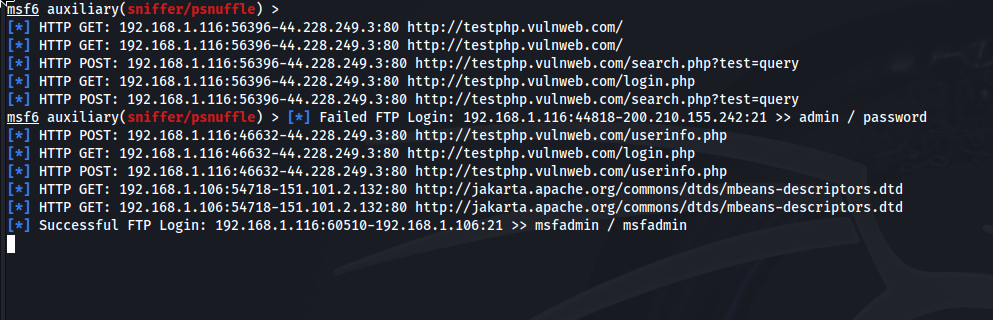
After carefully configuring the module options, you’re ready to start the sniffer. Use the run or exploit command:
runThis command initiates the sniffer, and it will begin capturing password traffic on the network (according to your configured filter, if any). The captured data, including any potentially sensitive information, will be displayed in the msfconsole window.
5. Analyze the results:
Carefully examine the captured data displayed in msfconsole. Modules like psnuffle often attempt to automatically parse the captured passwords and usernames, presenting them in a more readable format. However, this automatic parsing is not always perfect. In some cases, you may need to manually analyze the raw captured data to extract the desired information.
Conclusion
In this article, we’ve explored the core steps and ethical dimensions of password sniffing using Msfconsole. We hope this information is a valuable tool for enhancing your network security and pinpointing potential vulnerabilities within authorized environments. Understanding these techniques empowers you to think like an attacker and proactively address weaknesses. However, it’s crucial to remember that this knowledge must be used for legal and ethical purposes only. Respect the privacy of others and adhere to all applicable laws. This guide is intended to facilitate security assessments on networks where you have explicit authorization. By identifying vulnerabilities, you can implement stronger security measures to protect sensitive data. Continuous monitoring, regular assessments, and ongoing education are key to a robust security posture. Use this knowledge responsibly and ethically to contribute to a more secure digital environment.


Hey, that’s really so cool, please much for