Introduction
OnSystemsHellDredd is a Capture The Flag (CTF) machine provided by Offensive Security. This machine contains various vulnerabilities that are ideal for penetration testing and security research. CTF events offer participants the opportunity to discover vulnerabilities they may encounter in real-world scenarios and exploit these vulnerabilities to gain access to systems. This OnSystemsHellDredd Offsec Walkthrough will detail the steps needed to compromise the OnSystemsHellDredd machine.
Learning Objectives
The objectives of this walkthrough include:
- Gathering information about the target system.
- Identifying open ports and running services.
- Detecting vulnerabilities and exploiting them.
- Gaining user and root access.
- Understanding methods to mitigate security weaknesses.
Participants will enhance their skills in using penetration testing tools and acquire the necessary knowledge to improve system security throughout this walkthrough of the OnSystemsHellDredd Offsec machine.
Purpose of This CTF
The purpose of this OnSystemsHellDredd CTF is to help participants develop their penetration testing skills and discover vulnerabilities they may encounter in real-world scenarios. Participants will have the opportunity to practice finding security weaknesses in systems and leveraging these weaknesses to gain access. Additionally, such events provide security professionals with insights on how to remain prepared against current threats. This OnSystemsHellDredd Offsec Walkthrough provides a clear guide on how to achieve these goals.
Enumeration
Target Information Gathering
Before starting the exploitation process, the target machine’s IP address must be identified. For example, an address like 192.168.43.86 can be used. At this stage, general information about the target system is collected, including operating system version, services in use, and open ports. This walkthrough on the OnSystemsHellDredd Offsec machine will provide detailed instructions for this stage.
Port Scanning
Nmap is used to identify open ports and running services on the target machine:
nmap -sV -sC 192.168.43.86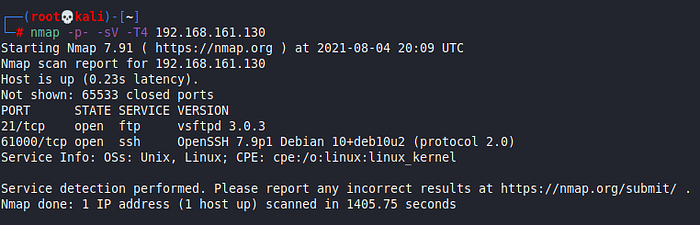
This command reveals which ports are open and which services are running on those ports, such as FTP (21) or SSH (22). This information will guide subsequent steps in identifying potential vulnerabilities for this OnSystemsHellDredd Offsec Walkthrough.
Exploitation
Accessing the FTP Service
The next step is to access the FTP service on the target system using anonymous login:
ftp 192.168.43.86During the FTP session, hidden directories are checked, and a directory named .hannah is discovered. This directory may contain sensitive files or data that can be exploited. The detailed steps for this procedure are documented in the OnSystemsHellDredd Offsec Walkthrough.
Obtaining the Key File
The private key file id_rsa located within the hidden directory is downloaded:
cd .hannah/
get id_rsa
This file will be used for SSH access to the target machine. After downloading, it is essential to review its contents carefully following the guidelines provided in this OnSystemsHellDredd Offsec Walkthrough.
Privilege Escalation
Changing Key Permissions
The permissions of the downloaded key file are modified:
chmod 600 id_rsaThis step ensures that only the owner can read the key, preventing unauthorized access as per the OnSystemsHellDredd Offsec Walkthrough.
Establishing an SSH Connection
Using the private key, an SSH connection is established with the target machine:
ssh -i id_rsa hannah@192.168.43.86 -p61000At this point, user access is obtained, allowing for further exploration of the system in accordance with the steps in this OnSystemsHellDredd Offsec Walkthrough.

Finding the First Flag
Within the user directory, the user.txt flag is located:
cat user.txtThis flag signifies success in the first stage of the penetration test as detailed in the OnSystemsHellDredd Offsec Walkthrough.
Checking Sudo Permissions
Checking SUID Binaries
SUID binaries are checked for potential privilege escalation opportunities:
find / -type f -perm -u=s 2>/dev/null
These steps culminate in obtaining root access following the OnSystemsHellDredd Offsec Walkthrough.
Executing Privilege Escalation Command
A SUID binary is exploited for privilege escalation:
/usr/bin/cpulimit -l 95 -f /bin/bash<br>
Retrieving the Root Flag
Finally, navigate to the root directory and read the root.txt flag:
cd /root
cat root.txtThis flag represents success at the final stage of exploitation, indicating that all steps have been completed successfully with the help of the OnSystemsHellDredd Offsec Walkthrough.
Conclusion
This OnSystemsHellDredd Offsec Walkthrough covers the essential steps taken to compromise the OnSystemsHellDredd machine. It details how to discover vulnerabilities within a target system, exploit those vulnerabilities, and ultimately gain root access. Such CTF scenarios not only help security professionals enhance their skills but also provide valuable insights into improving system security practices. Participants who engage in these exercises take a significant step toward becoming more effective security experts by applying what they learn in real-world situations.

