Introduction
Metasploitable2 is a virtual machine specifically designed for cybersecurity professionals and penetration testers. This machine contains various vulnerabilities and security flaws, making it an ideal environment for testing and security assessments. Compatible with the Metasploit Framework, Metasploitable2 is highly useful for real-world security testing. In this article, we will guide you step by step on how to install and use Metasploitable2 on VirtualBox. This Metasploitable2 installation guide will be helpful for you.
Learning Objectives
- Understand what Metasploitable2 is and how it works.
- Learn the necessary steps to install Metasploitable2 on VirtualBox.
- Gain hands-on experience in creating and configuring a virtual machine in VirtualBox.

What is Metasploit?
Metasploit is a popular open-source tool used to discover, test, and remediate security vulnerabilities. The Metasploit Framework allows security professionals to conduct attacks on target systems and analyze vulnerabilities. The various modules, attack simulations, and exploits provided by Metasploit help you test security flaws. Metasploitable2 is compatible with the Metasploit Framework, providing a test environment for security assessments. You’ll need this system to get the most out of your Metasploitable2 installation guide.
Let’s Start Installing Metasploit
Step 1: Downloading Metasploitable2
- Use the following link to download Metasploitable2: Metasploitable2 Download Link. Once the download is complete, save the zip file to your computer.
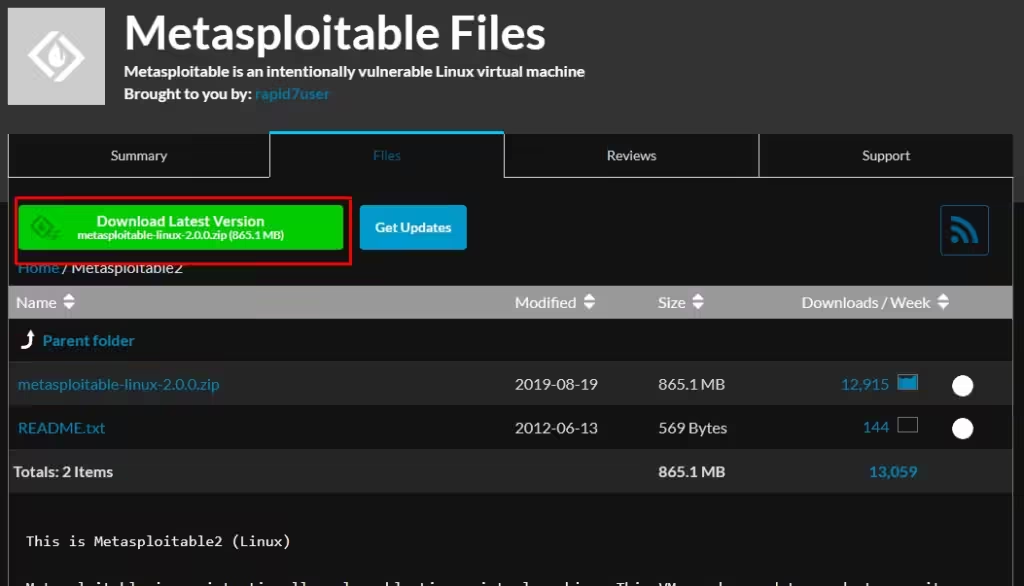
Step 2: Extracting the Downloaded File
- Right-click the downloaded zip file and select “Extract Here.” The extracted content will include a virtual machine image (in VMDK or OVF format) (Shell to Meterpreter Transition in Metasploit).
Step 3: Adding a New Virtual Machine to VirtualBox
- Open the VirtualBox application and click on the “New” button.
- In the window that appears, give your virtual machine a name, such as “Metasploitable2.”
- Optionally, you can specify a folder path to store the virtual machine files. This step is optional and allows you to select a directory for storing your virtual machine files.
- Select “Linux” as the “Type” and “Other Linux (64-bit)” as the “Version.”
- Click “Next.”
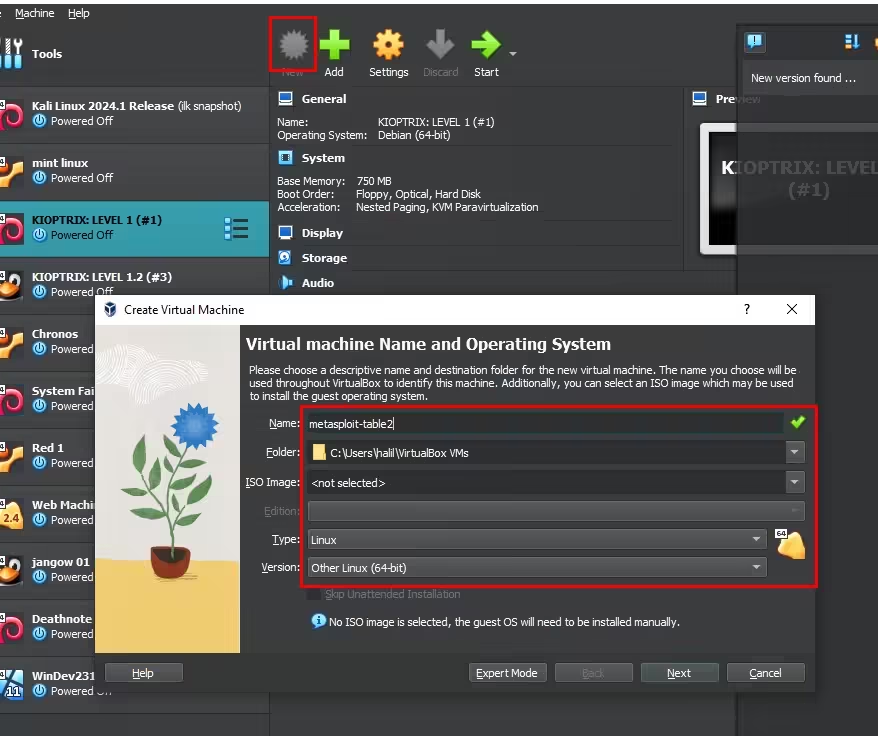
Step 4: Configuring the Virtual Machine Settings
- Adjust the amount of RAM and other resources according to your needs. You can use the default settings; however, allocating sufficient RAM and CPU resources may enhance performance.
Step 5: Using an Existing VirtualBox Disk File
- Select “Use an existing virtual hard disk file.”
- Choose and add the extracted Metasploitable2 file. At this step, you will have loaded the virtual machine image into VirtualBox (What is Metasploit-Framework and How is it Used?).
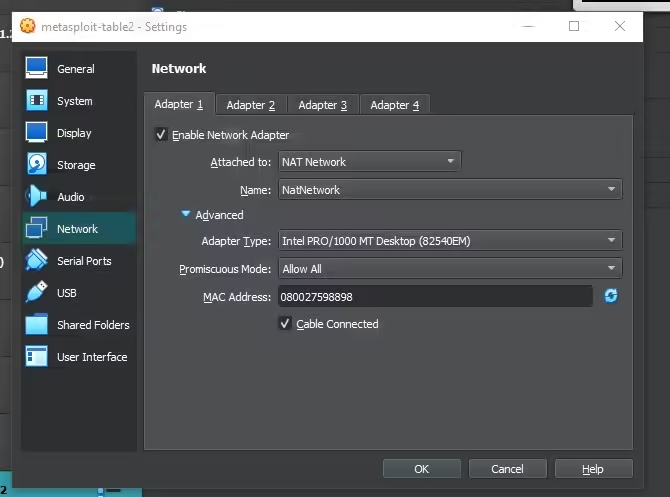
Step 6: Configuring Network Settings
- Right-click on the created virtual machine and go to “Settings.”
- Go to the “Network” tab and configure your network settings. Typically, “NAT” or “Bridged Adapter” is used. This setting manages the network connection of your virtual machine and ensures that it has the appropriate network configuration for your tests.
Conclusion
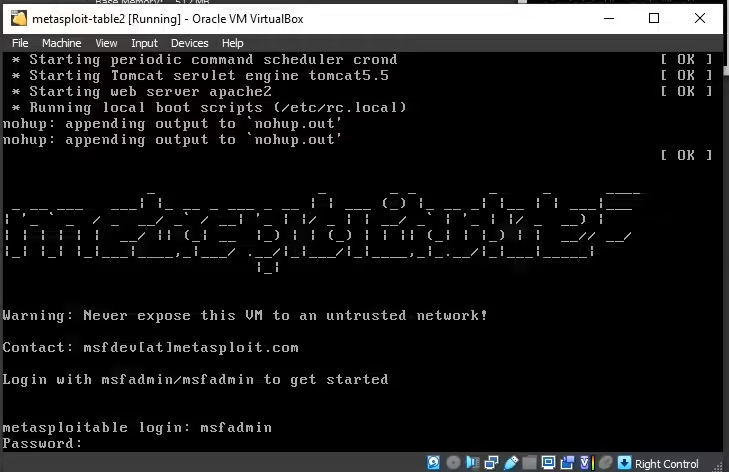
Your Metasploitable2 virtual machine is now successfully installed on VirtualBox. To start the virtual machine, double-click on it. Once Metasploit launches, you can interact with it using your keyboard. Follow this Metasploitable2 installation guide closely. At the login screen, enter the username and password as “msfadmin” to log in. From this point on, you can perform various penetration tests and analyze security vulnerabilities using the Metasploit Framework (Virtual Machines and How Do They Work).
In future articles, we will delve deeper into conducting real-world penetration tests and security assessments using different tools. Learning more about the various modules and tools offered by Metasploit will help you succeed in these tests. This Metasploitable2 installation guide will be a useful reference.


If you specify in the comments the parts you are curious about and have difficulty doing, I will try to help you.
Hey man, this is really great, I understood, I couldn’t connect to the internet in many of the YouTube videos I watched.
Do I need to download any additional tools or software to use Metasploit with Metasploitable2?
Yes, Metasploit is typically installed on Kali Linux, which you can use alongside Metasploitable2 in VirtualBox. However, you don’t need additional tools specifically for this guide, as Metasploit is ready to use on the virtual machine once it’s installed.
Can I use a different hypervisor like VMware instead of VirtualBox for running Metasploitable2? If so, are there any differences in the setup process?
Yes, you can use VMware as an alternative. The setup process is very similar, but the interface and some steps, such as network configuration, might slightly differ.
Both are great options, so feel free to choose based on your preference.
For those interested in testing different vulnerabilities, Metasploitable2 also has a few intentionally weak services that can be exploited, such as FTP, SSH, and database servers. Don’t forget to explore these after installation!