Introduction
In today’s digital age, data security and privacy are paramount for both organizations and individuals. Ensuring the security of online transactions and protecting sensitive information requires robust tools. OpenSSL, an open-source software library that facilitates data encryption and secure communication using SSL and TLS protocols, is one of these vital tools. This article delves into the basic usage and essential OpenSSL commands, demonstrating their effectiveness in daily operations.
Why OpenSSL?
OpenSSL implements the secure communication protocols SSL (Secure Sockets Layer) and TLS (Transport Layer Security). These protocols aim to encrypt data sent over the internet, thereby preventing unauthorized third-party access. It also includes fundamental cryptographic functions like digital certificates and key management.
The popularity and widespread use of OpenSSL stem from its open-source nature. This means that developers worldwide can contribute, quickly identifying and fixing security vulnerabilities. Its flexibility and modular structure also make it easily integrable in various applications and services.
In this article, we will explore OpenSSL’s most basic and common uses: creating your own SSL certificates, file encryption, data signing, and establishing secure server connections. These insights will help you create a secure digital environment.
Flags and Descriptions in OpenSSL Commands
OpenSSL is a tool providing various cryptographic functions for SSL and TLS protocols, managed through command-line flags. Each flag controls a different feature or function of OpenSSL. Here are the most commonly used OpenSSL flags and their explanations:
-x509: This flag is used to create a self-signed certificate directly from a Certificate Signing Request (CSR).-newkey rsa:4096: Creates a new RSA key pair. The number4096specifies the key length in bits, with 2048 or 4096 bits commonly preferred for stronger encryption.-keyout: Specifies the filename where the generated private key will be saved.-out: Specifies the filename where the generated certificate or CSR will be saved.-days: Specifies the validity period of the certificate in days. For example,-days 365creates a one-year certificate.-nodes: This flag ensures that the private key is stored without encryption (no DES). It’s often used in automated processes where manual decryption of the key is not required.-req: Used for a CSR process or to create a certificate from a CSR.-in: Specifies the name of the input file, which could be a CSR or a private key file.-CAand-CAkey: Specifies the Certificate Authority (CA) certificate and CA’s private key, used for signing a CSR.-CAcreateserial: Creates a serial number file for the CA, ensuring unique serial numbers for certificates signed by the same CA.-outform: Specifies the format of the output file (e.g., PEM or DER).-pubout: Used to extract the public key from a private key.-enc: Used for encrypting files with a specific encryption algorithm (e.g.,-aes-256-cbc).-d: Used for decryption, typically to revert encrypted files to their original state.-md5: Computes the hash value of a file using the MD5 hash algorithm.
Understanding and Implementing OpenSSL Features
The various commands and flags offered by OpenSSL are used to manage the fundamental aspects of cryptography and data security. This section will address how to implement OpenSSL’s basic features and practical usage scenarios.
Creating your SSL certificates, establishing secure server connections, encrypting and signing data are reflections of OpenSSL’s everyday applications. These features not only ensure the security of websites but also play a critical role in protecting sensitive data and facilitating secure communications. For instance, a self-signed SSL certificate created with OpenSSL can securely establish and operate a website.
This section will delve into more detailed explanations of OpenSSL’s basic usage scenarios and features, demonstrating how this tool can be effectively used in daily tasks. It will also provide best practices and security recommendations to be aware of when using OpenSSL.
1. Create Your Own SSL Certificate
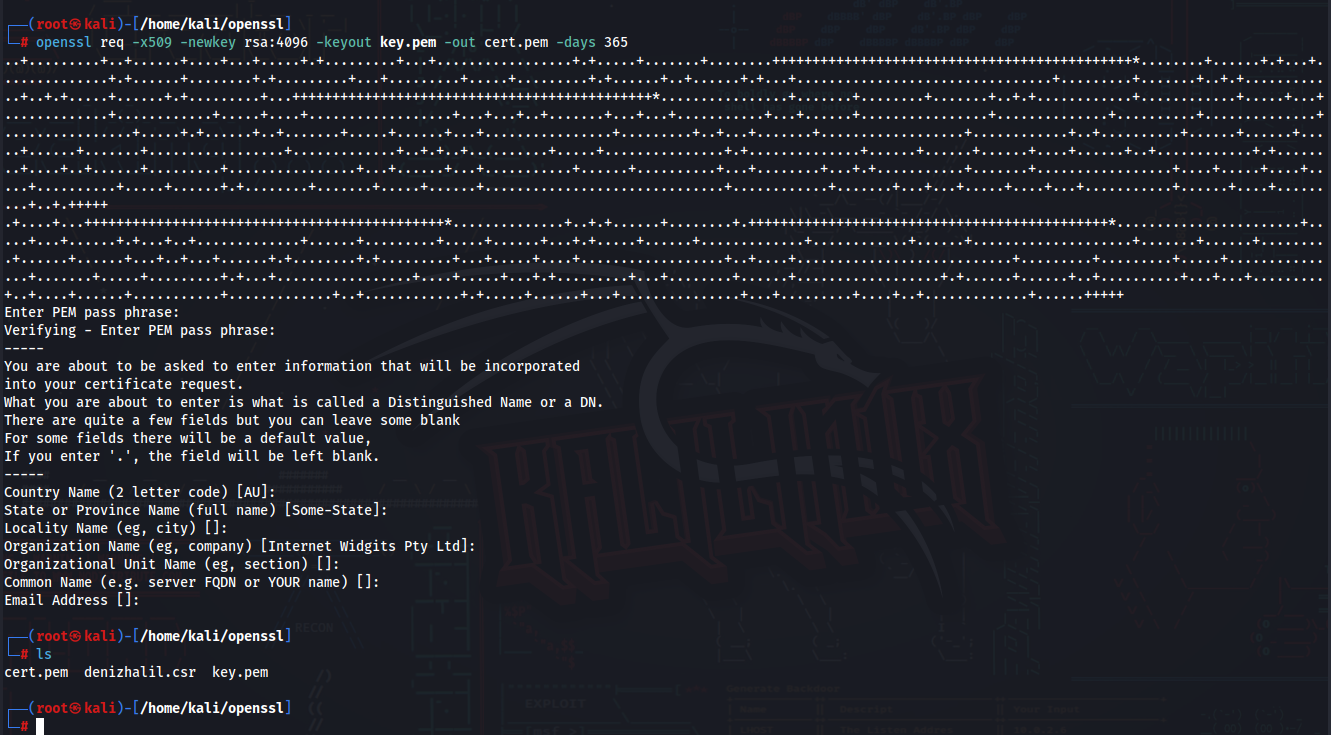
SSL certificates are fundamental to website security. Use the following command to create a self-signed certificate:
$ openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365This command creates a new RSA key pair and a SSL certificate valid for 365 days.
2. Create a CSR
To create a Certificate Signing Request (CSR) to be signed by a certificate authority (CA):
$ openssl req -new -newkey rsa:4096 -nodes -keyout mykey.key -out mycsr.csrThis step is often required to obtain an SSL certificate.
3. Sign Certificates
To sign a CSR using your own CA:
$ openssl x509 -req -days 365 -in mycsr.csr -CA myCA.pem -CAkey myCA.key -CAcreateserial -out mycert.pemThis process allows you to create customized certificates for a website or application.
4. Create RSA Key Pairs
Create RSA key pairs for secure data exchange:
$ openssl genpkey -algorithm RSA -out private_key.pem
$ openssl rsa -pubout -in private_key.pem -out public_key.pemThis is especially useful for encrypted communications.
5. Encrypt Files
Protect important files with AES-256 encryption:
$ openssl enc -aes-256-cbc -salt -in file.txt -out file.enc -pass pass:myPasswordThis method is effective for securing sensitive data.
6. Decrypt Files
To access the contents of an encrypted file:
$ openssl enc -d -aes-256-cbc -in file.enc -out file.dec -pass pass:myPasswordThis command reverts encrypted data back to its original state.
7. Sign Files
Verify the integrity of your files with an MD5 hash:
$ openssl dgst -md5 file.txtThis is used to ensure the file has not been altered.
8. Test SSL/TLS Connections
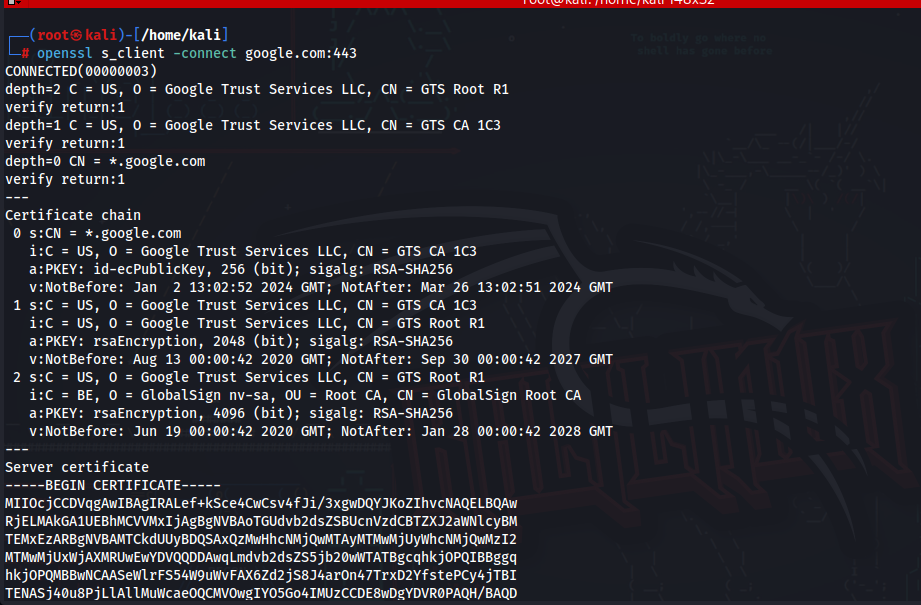
To test a server’s SSL/TLS configuration:
$ openssl s_client -connect example.com:443This command helps check if SSL/TLS connections are functioning correctly.
9. Key Format Conversion
To convert a key from PEM format to DER format:
$ openssl rsa -in key.pem -outform der -out key.derThis is necessary for key compatibility across different systems and applications.
10. Inspect Certificates
To view the details of an SSL certificate:
$ openssl x509 -in cert.pem -text -nooutThis command is useful for analyzing certificates.
11. Create a Diffie-Hellman Parameter File
Generate Diffie-Hellman parameters for key exchange:
$ openssl dhparam -out dhparam.pem 2048This enhances the security of SSL/TLS connections with stronger key exchange.
12. Generate a CSR with a Config File
Use a configuration file to create a more detailed CSR:
$ openssl req -new -key mykey.key -out mycsr.csr -config openssl.cnfThis approach allows for more customized certificate requests.
13. Verify a Certificate Chain
Check the validity of a certificate chain:
$ openssl verify -CAfile ca_bundle.pem cert.pemThis ensures the trustworthiness of the certificate chain.
14. Extract Certificate Information
Extract information like serial number, issuer, and validity from a certificate:
$ openssl x509 -in cert.pem -noout -serial -issuer -datesThis is useful for auditing and managing certificates.
15. Convert Certificate Formats
Convert a certificate from one format to another (e.g., PEM to DER):
$ openssl x509 -in cert.pem -outform der -out cert.derThis is necessary for compatibility with various applications that require different certificate formats.
Conclusion
OpenSSL is a powerful and flexible tool in the cybersecurity world. These commands will meet your basic security needs in daily operations and protect your data integrity. However, it’s always important to follow best practices and stay updated with current security protocols.