Bettercap: Network Discovery and Security Testing
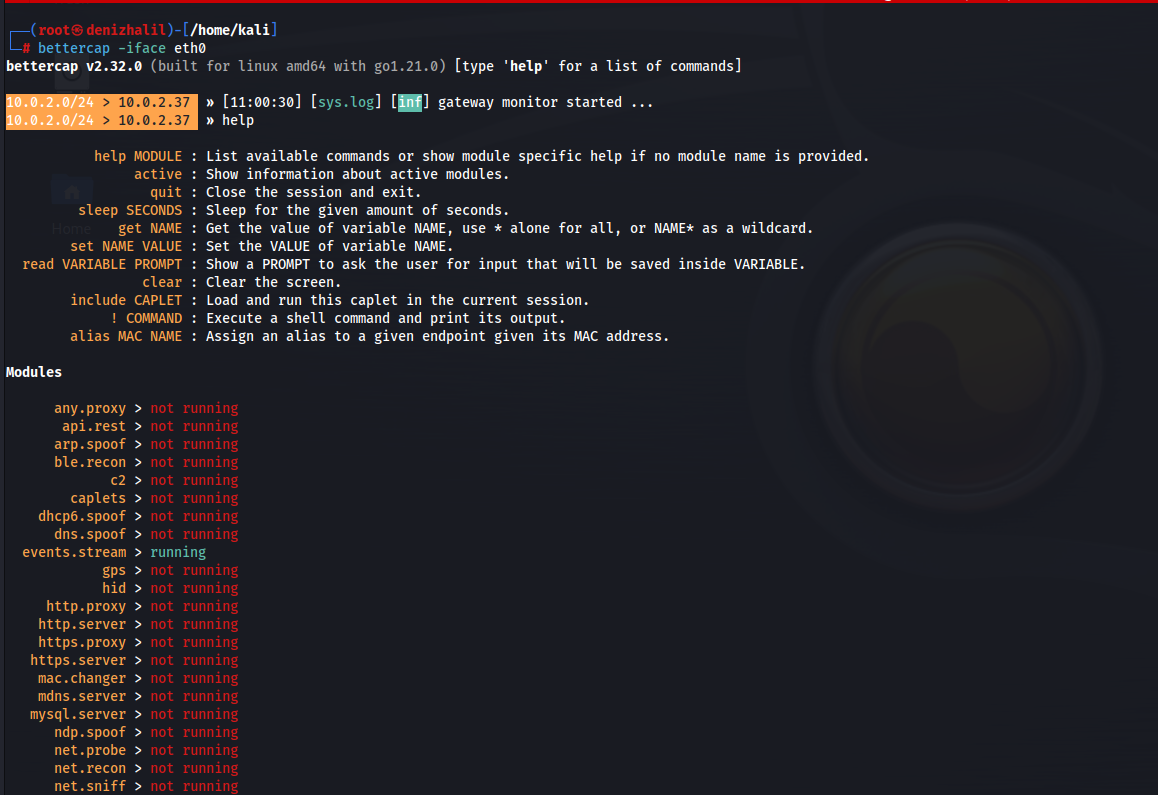
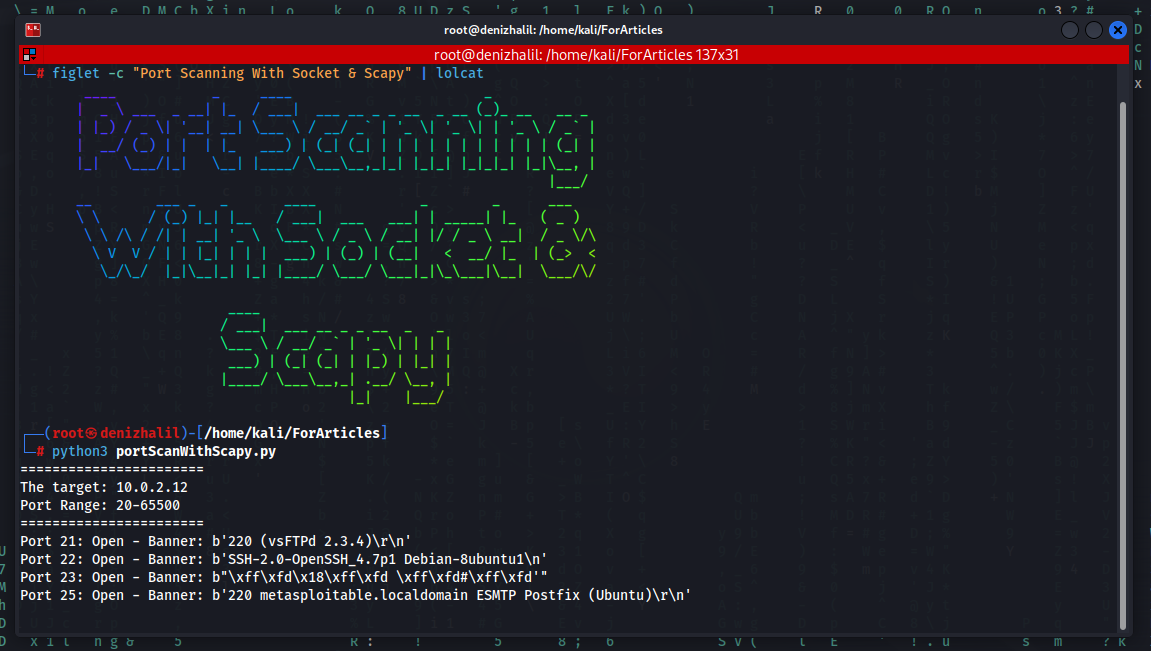
Introduction Bettercap stands as a highly regarded open-source tool among cybersecurity professionals, ethical hackers, and network administrators. It plays a pivotal role in advanced network reconnaissance and security assessments. Functioning across Linux, macOS, and Windows platforms, Bettercap is integral for scrutinizing network traffic, executing penetration tests, and identifying network vulnerabilities. Its operation demands not only