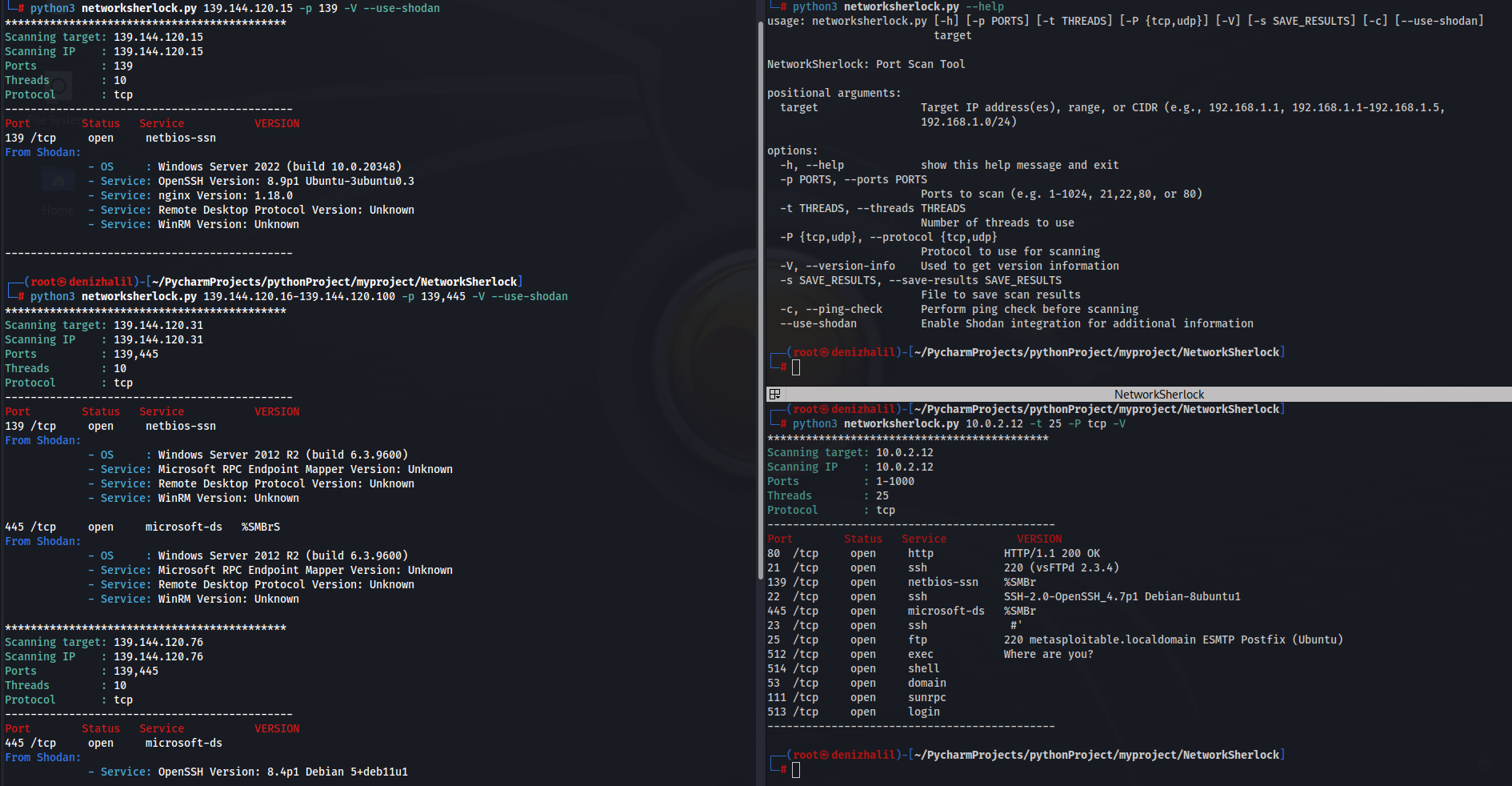
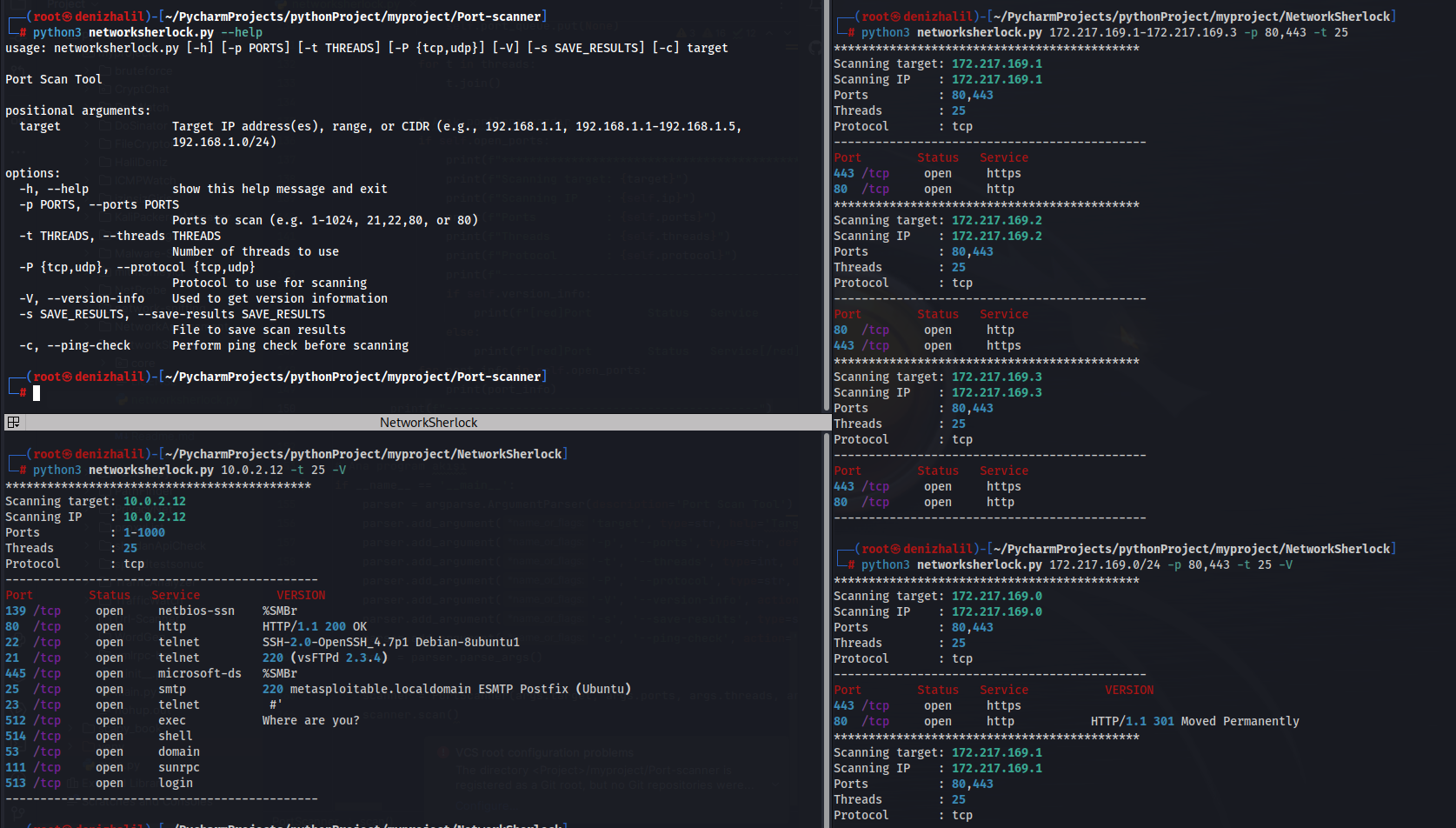
Tools for Preparing for Bug Bounty Programs
Introduction In the dynamic world of cybersecurity, Bug Bounty programs have emerged as a crucial bridge between ethical hackers and organizations. These programs incentivize the discovery and reporting of vulnerabilities, enhancing the overall security of digital assets. This comprehensive guide delves into the essential tools that are integral to preparing for successful participation in Bug