PassBreaker: Password Cracking Tool
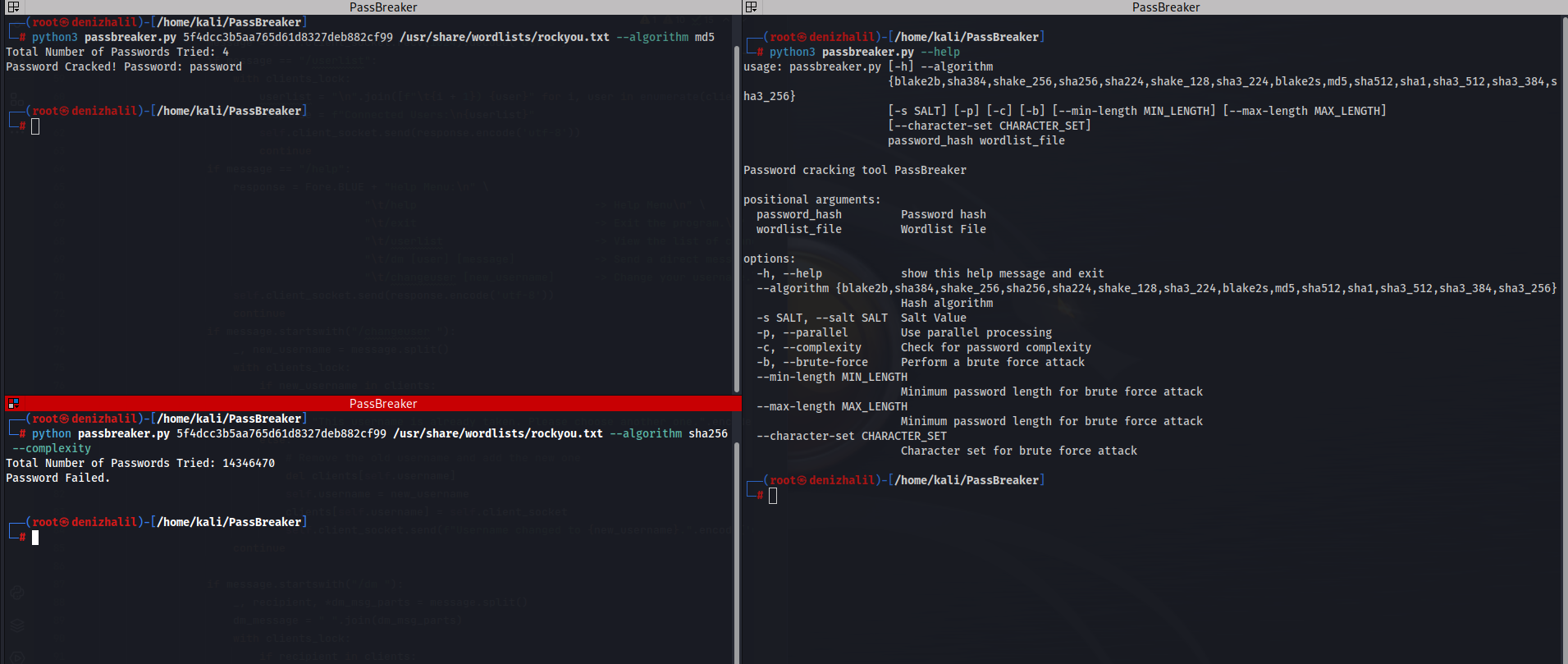
PassBreaker is a command-line password cracking tool developed in Python. It allows you to perform various password cracking techniques such as wordlist-based attacks and brute force attacks. Features Installation Usage Replace <password_hash> with the target password hash and <wordlist_file> with the path to the wordlist file containing potential passwords.Don’t forget to read our article on