Creating Ransomware with Python | Part 1
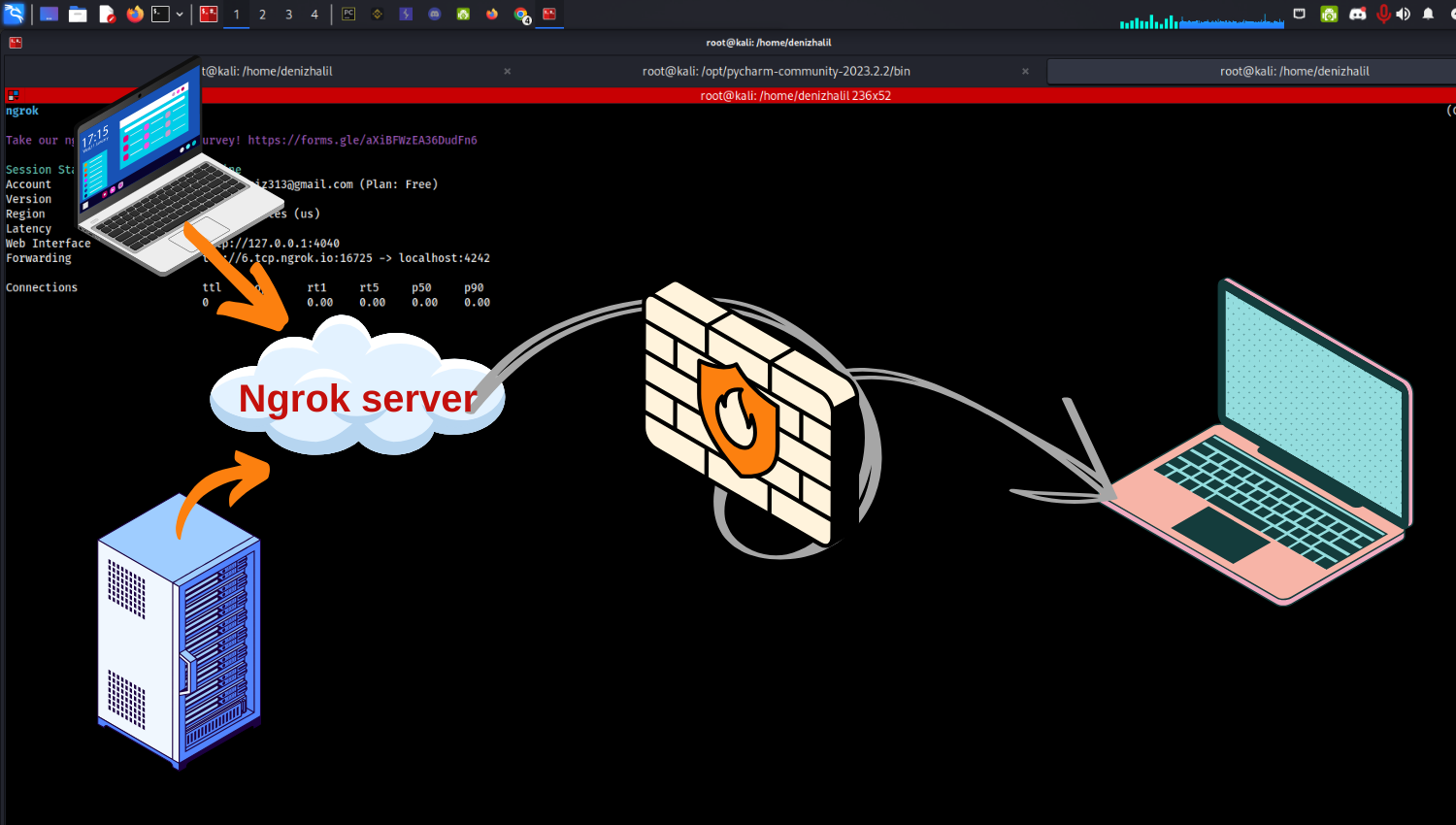
Introduction In this article, we will provide a step-by-step guide to creating a simple ransomware using Python. Ransomware is a type of malicious software that encrypts a user’s files, locking access to them. However, the ransomware we create in this article is for educational purposes only, to improve coding skills and raise awareness about cybersecurity,