Assessing Password Strength with Machine Learning in Python
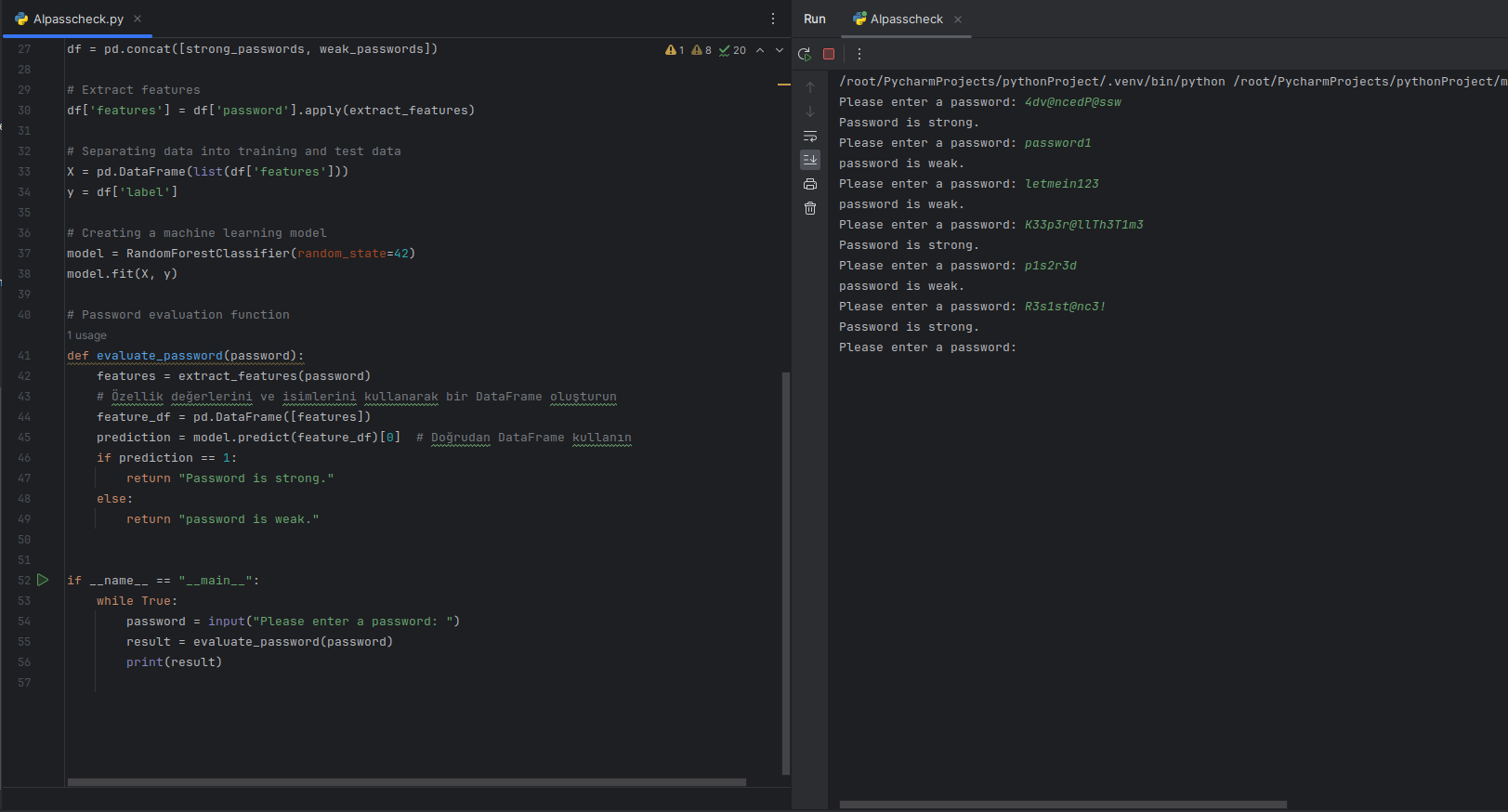
In the digital age, password security is a crucial aspect of protecting personal and sensitive information. Traditional methods of password validation often rely on predetermined rules, such as minimum length or the inclusion of various character types. However, these methods can be insufficient in determining the true strength of a password. To address this challenge, we turn to machine learning (ML) python as an