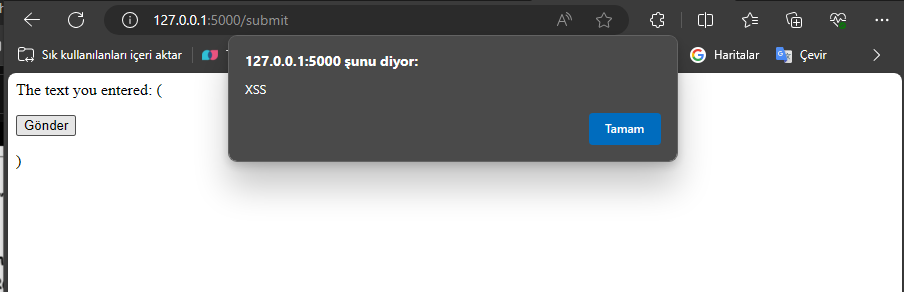
Data Transmission and Machine Learning with Client-Server Model
Introduction: In today’s world, data processing and communication technologies are becoming increasingly important. With the widespread use of the Internet, computing systems like the client-server model are commonly used for data transmission and processing. In this article, we will focus on data transmission and machine learning using a client-server model. Learning Objectives: What is Machine Learning? Machine learning is a