Introduction
In the evolving landscape of cybersecurity, Red Team operations have become essential for organizations seeking to assess their defensive capabilities against sophisticated threats. At the heart of these operations lies the Command & Control (C2) infrastructure, a critical component that enables security professionals to simulate adversarial tactics, techniques, and procedures in controlled environments. The Python-C2-Server-for-Red-Teaming project represents an accessible, open-source solution designed specifically for authorized penetration testing and security research. This framework demonstrates how modern C2 systems operate, providing hands-on experience with encrypted communication channels, multi-agent management, and remote command execution. Built with Python, it offers a lightweight yet powerful platform for security professionals, students, and researchers to understand the mechanics of C2 operations while maintaining focus on ethical and legal compliance.
Understanding C2 frameworks is not merely an academic exercise—it’s a practical necessity for anyone involved in offensive security, threat intelligence, or defensive security operations. By examining how these systems function, security teams can better detect, respond to, and mitigate real-world threats. This guide walks through the entire process of deploying and operating this C2 framework, from initial setup to practical operational scenarios.
Learning Objectives
By the end of this article, readers will have achieved several key learning outcomes that are fundamental to modern Red Team operations:
- Multi-Agent Management
- Real-Time Command Execution
- Legal and Ethical Frameworks
- Operational Security Awareness
- Practical Implementation Skills
- Encrypted Communication Techniques
- Comprehensive Understanding of C2 Architecture
What is a C2 Server and Agent?
Command & Control (C2) infrastructure represents the backbone of modern offensive security operations and, unfortunately, real-world cyberattacks. To fully appreciate its significance, we must understand both its components and their interactions.
- The C2 Server: functions as the central command hub—a nerve center from which security professionals (or in malicious scenarios, threat actors) coordinate operations across multiple compromised systems. The server maintains persistent connections with deployed agents, processes incoming data, distributes commands, and aggregates results from distributed operations. In Red Team scenarios, the C2 server enables operators to maintain control over simulated compromised assets, execute reconnaissance activities, perform lateral movement, and exfiltrate data—all while remaining undetected by defensive systems.
- The Agent: (also called an implant, beacon, or client) is the lightweight component deployed on target systems during penetration tests. Once executed on a target machine, the agent establishes an encrypted connection back to the C2 server, effectively creating a secure communication channel. The agent’s responsibilities include executing commands received from the server, gathering system information, maintaining persistence, and reporting back to the command center. Modern agents are designed to be stealthy, resilient, and adaptable to various operating systems and network environments.
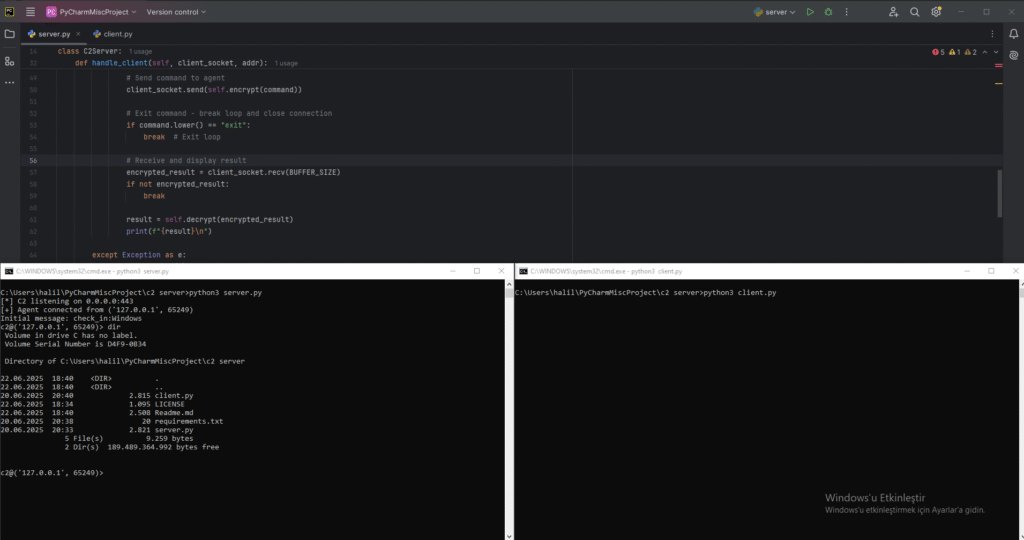
In the Python-C2-Server-for-Red-Teaming framework, the server listens on a configurable IP address and port (defaulting to 0.0.0.0:443), while agents automatically detect their operating system and report this information during initial check-in. This architecture mirrors real-world C2 systems used by advanced persistent threat (APT) groups, albeit in a simplified, educational format. The relationship between server and agent is bidirectional: the server pushes commands while agents pull instructions and push results. This design allows for flexible operational models, from simple command execution to complex, automated post-exploitation workflows.
How Does It Work? Purpose and Mechanisms
The Python-C2-Server-for-Red-Teaming framework employs several sophisticated mechanisms to achieve secure, reliable, and flexible C2 operations. Understanding these mechanisms is crucial for both offensive and defensive security practitioners.
- Encryption and Secure Communication: At the core of this framework lies AES-CBC (Advanced Encryption Standard in Cipher Block Chaining mode) encryption with 256-bit keys. Every message transmitted between the server and agents is encrypted before transmission and decrypted upon receipt. This encryption layer serves multiple purposes: it protects operational data from network monitoring, prevents tampering with commands or results, and helps evade basic intrusion detection systems that rely on pattern matching of plaintext commands. The framework uses a shared key that must be configured identically on both server and agent sides, emphasizing the importance of secure key management in real operations.
- Threading and Multi-Agent Support: Real-world Red Team operations rarely involve single targets. The framework addresses this reality by implementing multi-threaded agent handling. When an agent connects, the server spawns a dedicated thread to manage that connection, allowing the operator to interact with multiple compromised systems simultaneously without blocking. This design pattern is essential for scenarios involving lateral movement across network segments or coordinating actions across multiple endpoints. Each agent connection maintains its own context, command history, and execution state.
- Automatic Reconnection and Persistence: Network interruptions are inevitable in real-world scenarios—firewalls may temporarily block connections, systems may reboot, or network segments may become temporarily unavailable. The framework addresses this challenge through automatic reconnection logic. When an agent loses its connection to the C2 server, it enters a retry loop, attempting to reestablish communication every 60 seconds. This persistence mechanism ensures that temporary disruptions don’t result in complete loss of access, mimicking the behavior of sophisticated malware families.
- Interactive Command Execution: The server provides an interactive console interface that allows operators to send arbitrary shell commands to connected agents. When a command is issued, it’s encrypted and transmitted to the target agent, which executes it within the context of the local operating system’s shell (cmd.exe on Windows, /bin/sh on Unix-like systems). The output is captured, encrypted, and returned to the operator in real time. This interactive model enables reconnaissance, privilege escalation attempts, data gathering, and other post-exploitation activities.
- Cross-Platform Compatibility: The agent automatically detects its operating system during initialization and reports this information to the server during the check-in process. This capability allows operators to adapt their commands and techniques based on the target environment, whether dealing with Windows, Linux, or other platforms.
- Operational Flexibility: The framework’s configuration parameters—including server IP, listening port, and encryption keys—are easily customizable, allowing operators to adapt the infrastructure to specific engagement requirements, network constraints, or operational security considerations.
The ultimate purpose of this C2 framework is educational and defensive: by understanding how such systems operate, security professionals can better detect them in their networks, develop appropriate countermeasures, and improve incident response capabilities. For Red Teams, it provides a foundation for learning C2 operations in authorized testing scenarios.
Hands-On: Example Workflow
Let’s walk through a complete operational scenario, from initial setup to active C2 operations. This hands-on example demonstrates the practical application of the framework in a controlled testing environment.
Step 1: Environment Preparation and Download
Begin by ensuring you have a proper testing environment—ideally, isolated virtual machines or a dedicated lab network to prevent any accidental impact on production systems. Open your terminal and clone the repository:
git clone https://github.com/HalilDeniz/Python-C2-Server-for-Red-Teaming.git
cd Python-C2-Server-for-Red-TeamingThis downloads the complete project structure, including both server and agent components, to your local system.
Step 2: Dependency Installation
The framework relies on cryptographic libraries for its encryption functionality. Install the required dependencies using pip:
pip install pycryptodomeThis package provides the AES encryption implementation used for securing communications. If you’re working in a virtual environment (recommended for Python projects), ensure it’s activated before installing dependencies.
Step 3: Configuration (Optional but Recommended)
Before launching the framework, review the configuration settings in both server.py and client.py. Critical parameters include:
- Server IP Address: The interface on which the C2 server listens (0.0.0.0 listens on all interfaces)
- Port Number: Default is 443 (HTTPS port), but you may need to change this depending on your environment or if you lack root privileges
- Encryption Key and Passphrase: For security, always change these from their default values before any real testing
Open the files in your preferred text editor and modify these values as needed for your specific testing scenario.
Step 4: Starting the C2 Server
Launch the server component, which will listen for incoming agent connections and Upon successful initialization, you should see output similar to:
$ python server.py
[*] C2 listening on 0.0.0.0:443The agent will attempt to establish an encrypted connection to the C2 server. If successful, it performs an initial check-in, reporting its operating system and connection details.
Step 5: Agent Connection and Initial Reconnaissance
Back in the server terminal, you should see a connection notification:
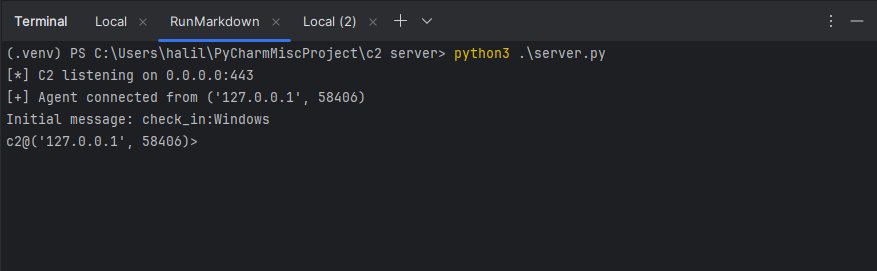
This indicates a successful connection from an agent running on a Windows system with IP address 192.168.1.10. The server now presents an interactive prompt for that specific agent
Step 6: Executing Commands and Gathering Intelligence
Now you can begin issuing commands to the connected agent. Start with basic reconnaissance:
c2@('192.168.1.10', 54321)> whoami
DESKTOP\user
c2@('192.168.1.10', 54321)> hostname
DESKTOP-ABC123
c2@('192.168.1.10', 54321)> ipconfig
Ethernet adapter Local Area Connection:
IPv4 Address. . . . . . . . . . . : 192.168.1.10
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.1Step 7: Graceful Shutdown
When you’ve completed your testing, disconnect the agent cleanly
c2@('192.168.1.10', 54321)> exit
[-] Agent ('192.168.1.10', 54321) disconnectedThis workflow provides a complete operational cycle, from deployment through active operations to clean termination.
Legal Disclaimer
The legal and ethical dimensions of C2 framework usage cannot be overstated—they represent the most critical aspect of any offensive security work.
- Strict Authorization Requirements: This software is designed exclusively for authorized penetration testing, security research, and educational purposes. “Authorized” means having explicit, documented, written permission from the owner or authorized representative of any systems you test. Verbal permission is insufficient—always obtain signed authorization documents that clearly specify the scope, timing, and methods of your testing activities.
- Criminal Liability: Unauthorized access to computer systems, even for educational purposes, constitutes a serious crime in virtually every jurisdiction worldwide. Laws such as the Computer Fraud and Abuse Act (CFAA) in the United States, the Computer Misuse Act in the United Kingdom, and similar legislation in other countries impose severe criminal penalties—including imprisonment—for unauthorized access, damage to systems, or theft of data.
- Professional Responsibility: Security professionals have an ethical obligation to use their skills responsibly. The tools and techniques demonstrated in this article are powerful and can cause significant harm if misused. Always operate within the boundaries of your authorization, respect privacy and confidentiality, and prioritize the safety and integrity of systems under test.
- Educational Context: When using this framework for learning purposes, restrict all testing to systems you own, properly configured lab environments, or authorized training platforms. Never test against production systems, public infrastructure, or third-party networks without explicit authorization.
- User Responsibility: The author and contributors of the Python-C2-Server-for-Red-Teaming project explicitly disclaim responsibility for any misuse. All legal, ethical, and professional responsibility lies solely with the user. By downloading, installing, or using this software, you accept full responsibility for ensuring your activities are legal, authorized, and ethical.
Remember: the purpose of Red Team operations and offensive security tools is to improve security, not to cause harm. Always operate with integrity, respect legal boundaries, and use your skills to make systems safer and more resilient.
Conclusion
The Python-C2-Server-for-Red-Teaming framework serves as an invaluable educational resource for anyone seeking to understand the mechanics of Command & Control infrastructure in modern cybersecurity operations. Through hands-on experience with this project, security professionals can develop practical skills in secure communication, multi-agent management, and interactive post-exploitation techniques—all essential capabilities for effective Red Team operations. Beyond its immediate educational value, this framework provides a foundation for understanding how real-world threat actors operate, enabling defensive security teams to better detect, analyze, and respond to sophisticated attacks. By studying C2 mechanics from an offensive perspective, blue teams can enhance their threat hunting capabilities, improve their security monitoring, and develop more effective incident response procedures. The project’s roadmap includes exciting future enhancements such as dynamic key exchange, TLS/SSL encryption, traffic obfuscation, and agent auto-update capabilities—features that will bring it closer to production-grade C2 frameworks while maintaining its educational focus. As the cybersecurity landscape continues to evolve, the gap between offensive and defensive capabilities must narrow. Projects like this democratize knowledge about adversarial techniques, empowering security professionals to stay ahead of emerging threats. However, with this knowledge comes profound responsibility: always operate within legal and ethical boundaries, obtain proper authorization, and use these skills exclusively to improve security rather than compromise it.