Introduction
In the world of network security, understanding how data packets traverse through networks is crucial. One of the most powerful tools available for packet manipulation is Scapy, a Python-based interactive packet manipulation program. Scapy allows users to create, send, and analyze network packets, making it an essential tool for network engineers, security professionals, and researchers. This guide will delve into the process of sending fake packets using Scapy, explaining its significance, practical applications, and ethical considerations.
Learning Objectives
By the end of this guide, readers will be able to:
- Grasp the fundamentals of packet manipulation and its relevance in network security.
- Utilize Scapy to craft and send spoofed packets effectively.
- Recognize the ethical implications associated with packet manipulation.
- Develop a basic Python script that leverages Scapy for network testing and analysis.
Sending Fake Packets with Scapy
Scapy provides a flexible environment for crafting packets at various layers of the OSI model. Users can manipulate IP headers, TCP segments, and even application-layer protocols. Sending fake packets—also known as packet spoofing—can simulate various network conditions or attacks, such as Denial of Service (DoS) attacks or reconnaissance efforts. Packet spoofing involves altering the source address of a packet to make it appear as though it originated from a different device. This technique can be used for legitimate purposes such as testing firewalls or intrusion detection systems (IDS), but it can also be exploited for malicious activities. Understanding how to create and send these packets is vital for both testing defenses and recognizing potential threats.
Project Purpose
The primary purpose of this project is to demonstrate how to use Scapy for sending spoofed packets effectively. This serves multiple applications:
- Network Testing: By sending spoofed packets, network administrators can assess how well their systems handle unexpected traffic. This can help identify vulnerabilities in firewalls or other security measures.
- Learning Tool: For students and professionals alike, Scapy offers an excellent opportunity to learn about packet structures and network protocols. Crafting packets from scratch helps deepen understanding of how networks operate.
- Security Research: Researchers can use packet manipulation to explore vulnerabilities in various protocols and configurations. By simulating attacks, they can better understand how to defend against them.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffeeLet’s Write Our Code
To get started with sending fake packets using Scapy, we will write a Python script that allows users to input various parameters for packet creation. Below is an example code snippet that demonstrates this functionality:
1. Importing Libraries
from scapy.all import *
from colorama import Fore, Back, Style, init
# Initialize Colorama
init(autoreset=True)
- Scapy: This line imports all necessary functions and classes from the Scapy library, which is used for creating and manipulating network packets.
- Colorama: This imports the Colorama library to add color to console output, enhancing user experience.
- The
init(autoreset=True)function initializes Colorama. Theautoreset=Trueparameter ensures that the console text automatically resets to its default color after each print statement, making it easier to manage colored outputs.
2. Defining the Packet Sender Class
class SpoofedPacketSender:
def __init__(self, target_ip, target_port):
self.target_ip = target_ip
self.target_port = target_port- Class Definition: The
SpoofedPacketSenderclass encapsulates all functionality related to sending spoofed packets. - Constructor: The
__init__method initializes the class withtarget_ipandtarget_port, which represent the destination IP address and port number where the packet will be sent.
3. Sending Spoofed Packets Method
def send_spoofed_packet(self, source_ip=None, source_port=None, flags='S', payload=None):- This method defines how to send a spoofed packet. It takes several optional parameters:
source_ip: The IP address to use as the source (if not provided, a random IP will be generated).source_port: The port number to use as the source (if not provided, a random port will be generated).flags: TCP flags (default is ‘S’ for SYN).payload: Any additional data to include in the Packet spoofing.
4. Generating Random Source IP and Port
# If source IP is not provided, generate a random IP
if source_ip is None:
source_ip = RandIP()
# If source port is not provided, generate a random port
if source_port is None:
source_port = RandShort()- Random Source IP: If no source IP address is specified by the user, a random IP address is generated using Scapy’s
RandIP()function. - Random Source Port: Similarly, if no source port is specified, a random short port number is generated using Scapy’s
RandShort()function.
5. Creating Packet Layers
# Define IP and TCP layers
ip_packet = IP(src=source_ip, dst=self.target_ip)
tcp_segment = TCP(sport=source_port, dport=self.target_port, flags=flags)- This section creates the layers of the packet:
- An IP layer (
ip_packet) is created with the specified or generated source IP and the target IP. - A TCP segment (
tcp_segment) is created with the specified or generated source port and target port along with any flags provided by the user.
- An IP layer (
6. Adding Payload and Sending the Packet
# If payload is provided, add it to the TCP segment
if payload:
packet = ip_packet / tcp_segment / Raw(load=payload)
else:
packet = ip_packet / tcp_segment
# Send the packet
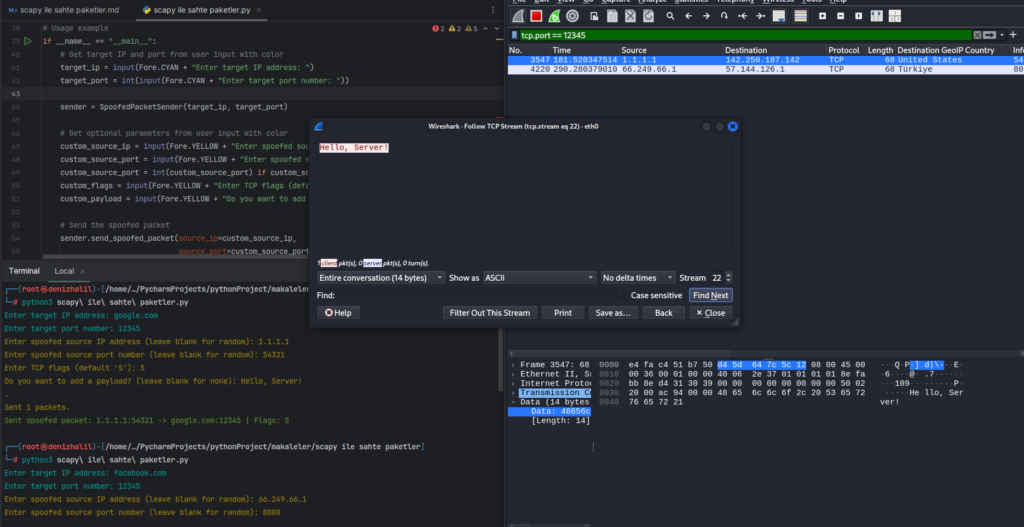
send(packet)
print(Fore.GREEN + f"Sent spoofed packet: {source_ip}:{source_port} -> {self.target_ip}:{self.target_port} | Flags: {flags}")- Adding Payload: If a payload is provided by the user, it is added to the TCP segment using Scapy Packet spoofing
/operator for layering packets. If no payload is specified, only the IP and TCP layers are combined. - Sending the Packet: The constructed packet is sent over the network using Scapy’s
send()function. - A message indicating that a spoofed packet has been sent is printed in green color for better visibility.
Mastering Scapy: A Comprehensive Guide to Network Analysis
Mastering Network Analysis with Scapy” is not just about learning a tool; it’s about unlocking a deeper understanding of the digital world that surrounds us
-5% $20 on buymeacoffee7. Main Program Execution
if __name__ == "__main__":
# Get target IP and port from user input with color
target_ip = input(Fore.CYAN + "Enter target IP address: ")
target_port = int(input(Fore.CYAN + "Enter target port number: "))
sender = SpoofedPacketSender(target_ip, target_port)
# Get optional parameters from user input with color
custom_source_ip = input(Fore.YELLOW + "Enter spoofed source IP address (leave blank for random): ") or None
custom_source_port = input(Fore.YELLOW + "Enter spoofed source port number (leave blank for random): ")
custom_source_port = int(custom_source_port) if custom_source_port else None
custom_flags = input(Fore.YELLOW + "Enter TCP flags (default 'S'): ") or 'S'
custom_payload = input(Fore.YELLOW + "Do you want to add a payload? (leave blank for none): ")
# Send the spoofed packet
sender.send_spoofed_packet(source_ip=custom_source_ip,
source_port=custom_source_port,
flags=custom_flags,
payload=custom_payload)- Main Execution Block: This block checks if the script is being run as the main program. It prompts users for input regarding:
- Target IP address.
- Target port number.
- An instance of
SpoofedPacketSenderis created using user-provided values. - Additional optional parameters are collected from user input.
- Finally, it calls the
send_spoofed_packetmethod on the sender instance with all collected parameters to send out the constructed Packet spoofing.
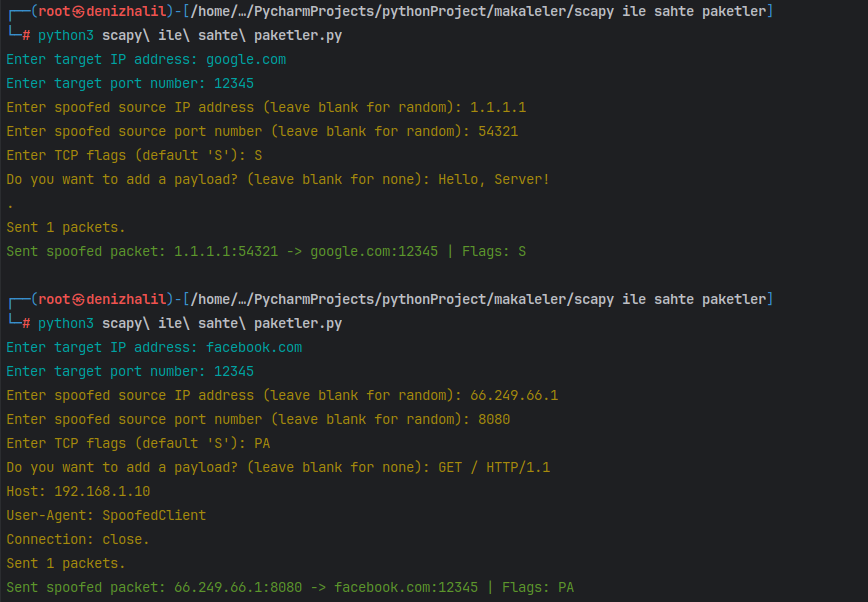
This breakdown provides a clear understanding of how each part of the code functions in creating and sending spoofed packets using Scapy while allowing user interaction through colored console inputs and outputs.
Conclusion
In conclusion, Scapy Packet spoofing provides an effective way to manipulate network packets for testing and educational purposes. By understanding how to send spoofed packets, users can gain valuable insights into network behavior and security vulnerabilities. However, it is crucial to use these skills responsibly and ethically to avoid potential legal issues.
As you explore the capabilities of Scapy Packet spoofing further, remember that knowledge comes with responsibility in the field of cybersecurity. Engaging in ethical hacking practices not only enhances your skills but also contributes positively to the cybersecurity community by helping organizations strengthen their defenses against malicious attacks. Always ensure that your activities comply with legal standards and ethical guidelines in your jurisdiction.




Nice work, how can we make different versions of this?
You can actually get different versions of V in many ways, especially depending on what you want to do.
for example: Sending ICMP Packets with Python Socket: Adventure in Signaling
thank you guys
I don’t know what you mean by different version, but you can also try with socket programming, but it’s much easier with scapy.