Introduction
Active Directory (AD) is a directory service developed by Microsoft for Windows environments, playing a crucial role in managing users, computers, and network resources. Since its launch with Windows 2000, AD has become essential for organizations of all sizes, providing functionalities such as authentication, authorization, and centralized management of access and policies. One of the key benefits of Active Directory is its ability to streamline administrative tasks. IT administrators can efficiently create and manage user accounts, set permissions, and enforce security policies from a single interface. This centralization not only enhances security but also reduces administrative overhead.
Active Directory uses a hierarchical structure that organizes data into domains, trees, and forests, allowing for efficient management of large networks. This organization facilitates resource sharing and establishes trust relationships between different domains. In this article, we will explore Active Directory in detail, discussing its significance, potential threats, security assessments, and best practices for maintaining a secure environment. Understanding these elements will empower organizations to leverage Active Directory effectively while protecting their critical data assets.
Learning Objectives
- Understand the fundamental concepts of Active Directory.
- Recognize the importance of securing Active Directory.
- Identify common threats targeting Active Directory systems.
- Learn how to perform a security assessment on Active Directory.
- Implement best practices for Active Directory security.
What is Active Directory Security?
Active Directory (AD) security is vital for protecting user credentials, company systems, sensitive data, software applications, and more from unauthorized access. AD, a Microsoft Windows directory service, allows IT administrators to manage users, applications, data, and various other aspects of their organization’s network. Since AD is central to authorizing users, access, and applications throughout an organization, it is a prime target for attackers. A security compromise of AD can undermine the integrity of an organization’s identity management infrastructure, leading to catastrophic levels of data leakage and system corruption.
Comprehensive AD security involves multiple steps and strategies, including access control lists (ACLs), encryption, and auditing capabilities to protect sensitive data and resources. Default security settings in AD may not be ideal for an organization’s needs and are well-understood by hackers who exploit gaps and vulnerabilities. Therefore, organizations should adjust default security settings to fit their specific requirements. Active Directory offers security features like access control lists (ACLs), encryption and auditing capabilities to protect sensitive data and resources. These are all important features to employ. But comprehensive and ongoing Active Directory security involves many other steps and strategies.
Active Directory Security Overview
Why is Securing Active Directory Important?
Securing Active Directory (AD) is of paramount importance because it serves as the central nervous system of a Windows-based network. As the primary point of authentication and authorization, AD controls access to critical systems, applications, and sensitive data. A compromise in AD security can have far-reaching and devastating consequences, making it a prime target for cyberattacks. When AD falls victim to malicious actors, the entire organization is exposed to a multitude of risks, including unauthorized access, data breaches, system-wide disruptions, and substantial financial losses. Protecting AD ensures that only authenticated and authorized users can access network resources, thus maintaining the integrity, confidentiality, and availability of organizational data. Implementing robust security measures helps prevent privilege escalation, where attackers gain control over critical systems by exploiting vulnerabilities. Securing AD also mitigates the risk of unauthorized information disclosure, ensuring that sensitive data remains protected from prying eyes.
Neglecting AD security can lead to various cyberattacks and escalations. Initially, malicious users may steal credentials or gain access using malware and then monitor your activity. They can then infiltrate additional accounts and move laterally through your system. With extensive access to your network, malicious users can either steal data or corrupt your system. Furthermore, maintaining a secure AD environment is often a requirement for regulatory compliance. Many industries are subject to regulations like HIPAA and PCI DSS, which mandate specific security measures, including those related to AD. Compliance ensures that your AD security practices align with any applicable regulations. It’s also important to evaluate your organization’s physical security. Ensure that physical access to the servers hosting Active Directory is restricted to authorized personnel only. You may need to implement physical security measures, such as card key access, biometric authentication, and surveillance.
Threats to Active Directory Systems
Active Directory (AD) systems are integral to the functioning of many organizations, serving as the backbone for user authentication and resource management. However, they also face a multitude of threats that can compromise their security and integrity. Here are eight significant threats to Active Directory systems:
- Unauthorized Access: One of the most pressing threats is unauthorized access, where attackers gain entry to AD without permission. This can occur through stolen credentials or exploiting vulnerabilities in the system. Once inside, attackers can access sensitive data, modify permissions, or disrupt services, leading to severe operational and reputational damage.
- Privilege Escalation: Attackers often seek to escalate their privileges within AD to gain control over critical systems. By exploiting misconfigurations or vulnerabilities, they can elevate their access rights, allowing them to perform administrative tasks or access sensitive information that should be restricted.
- Malware: Malicious software poses a significant risk to AD environments. Malware can infiltrate the network and compromise AD by stealing credentials or corrupting data. For instance, ransomware attacks can encrypt files and demand payment for decryption, while keyloggers can capture user credentials for later exploitation.
- Phishing Attacks: Phishing remains a prevalent method for attackers to gain access to AD. By sending deceptive emails that appear legitimate, attackers trick users into revealing their credentials. Once they have these credentials, they can access the AD environment and launch further attacks.
- Insider Threats: Employees or contractors with legitimate access can pose a substantial risk if they act maliciously or negligently. Insider threats may involve data theft, unauthorized changes to configurations, or even sabotage. Organizations must be vigilant in monitoring user activities and implementing strict access controls.
- Pass-the-Hash Attacks: This sophisticated attack method allows attackers to use hashed passwords instead of cleartext passwords to authenticate themselves on systems within the network. By stealing password hashes from memory, attackers can gain unauthorized access without needing the actual password.
- Kerberoasting: In this attack, an attacker targets service accounts in AD by requesting service tickets for high-privilege accounts from the Key Distribution Center (KDC). The attacker then extracts these tickets and attempts to crack them offline, potentially gaining access to high-level services with elevated privileges.
- DCSync Attacks: This type of attack involves an attacker impersonating a domain controller to synchronize with other domain controllers and extract sensitive information such as password hashes. Tools like Mimikatz make it easier for attackers to execute DCSync attacks, posing a severe threat to AD security.
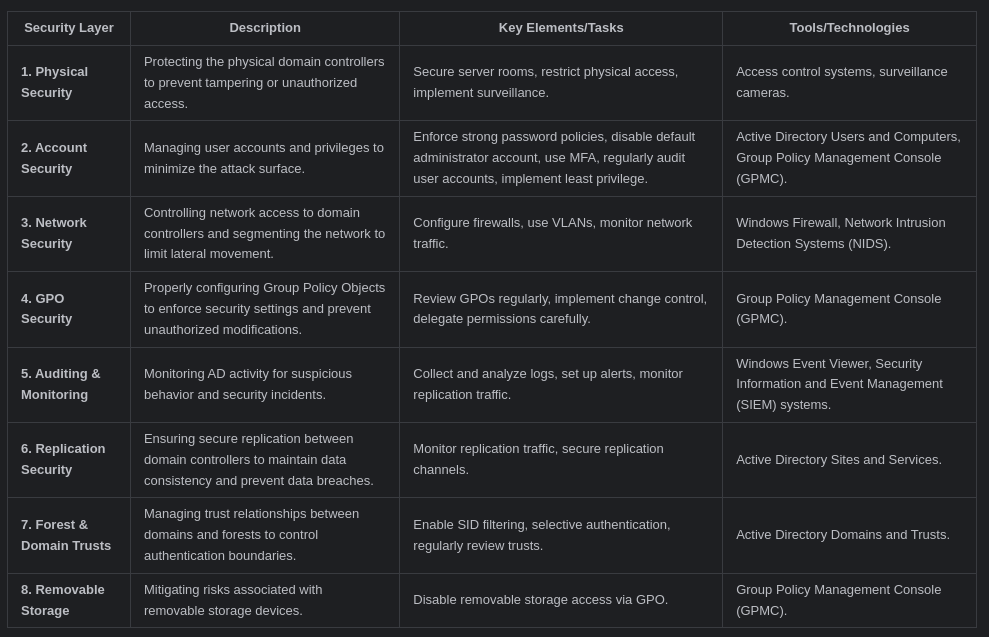
Active Directory Security Assessment Checklist
An Active Directory security assessment checklist helps identify vulnerabilities and weaknesses in the AD environment, providing a structured approach to enhance overall security posture. Here’s a detailed checklist to guide your assessment:
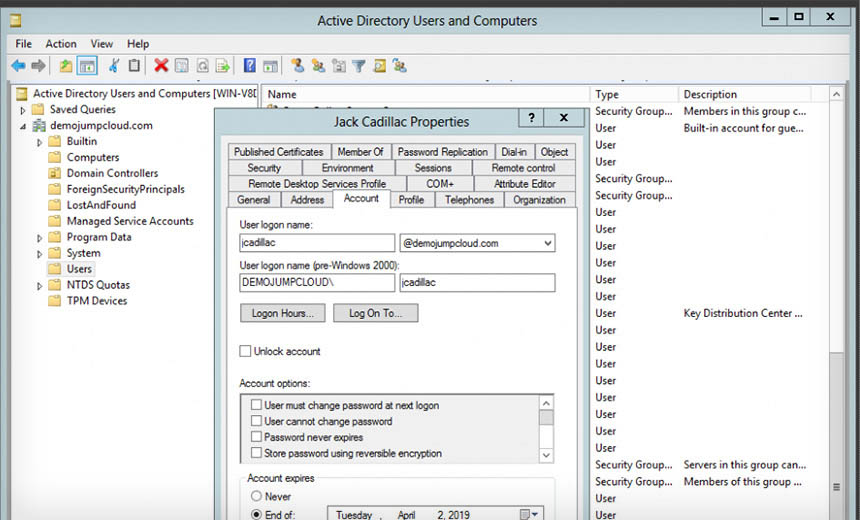
- User Account Review: Conduct a thorough review of all user accounts, focusing on identifying and managing inactive, orphaned, or privileged accounts. Ensure that accounts are appropriately named, follow naming conventions, and have accurate details. Disable or remove inactive accounts promptly to reduce potential attack vectors.
- Password Policies: Enforce strong password policies that require complex passwords, regular password changes, and prevent password reuse. Implement multi-factor authentication (MFA) to add an extra layer of security beyond just a username and password, mitigating the risk of compromised credentials.
- Group Membership: Regularly review group memberships and permissions to adhere to the principle of least privilege. Ensure that users have only the necessary access rights for their roles and responsibilities. Remove users from groups if their access requirements change to prevent unauthorized data access.
- Domain Controller Security: Harden domain controllers by applying security best practices, such as disabling unnecessary services, restricting administrative access, and implementing firewalls. Regularly patch and update domain controllers with the latest security updates to protect against known vulnerabilities.
- Group Policy Objects (GPOs): Review Group Policy Objects to ensure they are correctly configured and aligned with security best practices. Verify that GPOs are not misconfigured in a way that introduces vulnerabilities or provides excessive privileges. Implement change management controls to prevent unauthorized modifications.
- Auditing and Monitoring: Implement robust auditing and monitoring mechanisms to track changes and user activity within the AD environment. Collect and analyze logs regularly for suspicious activity, potential security breaches, or policy violations. Set up alerts to notify administrators of critical events in real-time.
- Physical Security: Secure the physical location of domain controllers to prevent unauthorized access and tampering. Restrict physical access to authorized personnel only and implement security measures such as surveillance cameras, access controls, and environmental monitoring.
- Replication Security: Ensure secure replication between domain controllers to maintain data consistency and prevent unauthorized access to AD data. Monitor replication traffic for anomalies, such as unexpected spikes or replication failures, which could indicate a security incident.
- Access Control Management: Regularly assess access controls to enforce the principle of least privilege, ensuring users have only the minimum necessary permissions to perform their job functions. Review and update access control lists (ACLs) on critical resources to prevent unauthorized access.
- Backup and Recovery Plans: Establish comprehensive backup and recovery plans for Active Directory data to ensure quick restoration in case of data loss, corruption, or a security incident. Regularly test the backup and recovery process to verify its effectiveness and reliability. Store backups securely and offsite to protect against physical disasters or cyberattacks.
Best Practices for Active Directory Security
To enhance the security of Active Directory (AD), organizations should adopt a comprehensive set of best practices that address various aspects of identity and access management. Implementing these strategies can significantly reduce vulnerabilities and protect sensitive data from unauthorized access. Here are some key best practices for securing Active Directory:
- Implement the Principle of Least Privilege (PoLP): This foundational security principle involves granting users only the minimum necessary rights and permissions required to perform their job functions. By limiting access, organizations can reduce the risk of unauthorized actions and potential data breaches. Regularly review and adjust permissions to ensure they align with current job responsibilities.
- Regularly Audit User Accounts and Group Memberships: Conduct frequent audits of user accounts and group memberships to verify their accuracy and appropriateness. This practice helps identify inactive or unnecessary accounts that can be disabled or removed, reducing the attack surface. Additionally, reviewing group memberships ensures that users have only the necessary access rights.
- Harden Domain Controllers: Domain controllers are critical to AD security, so it is essential to apply security best practices to protect them. This includes disabling unnecessary services, applying security patches promptly, and implementing firewalls to restrict access. Consider using dedicated servers for domain controllers to minimize exposure to potential threats.
- Implement Multi-Factor Authentication (MFA): Adding an extra layer of security through multi-factor authentication significantly enhances protection against unauthorized access. MFA requires users to verify their identity through multiple methods, such as a password combined with a one-time code sent to their mobile device. This makes it much harder for attackers to gain access even if they have stolen user credentials.
- Regularly Monitor and Audit AD Activity: Continuous monitoring of Active Directory logs is crucial for detecting suspicious activity or potential security incidents. Implement automated monitoring solutions that can alert administrators to unusual behavior, such as multiple failed login attempts or unauthorized changes to user accounts or permissions.
- Keep AD Updated with the Latest Patches: Regularly updating all components of Active Directory with the latest security patches is vital for protecting against known vulnerabilities. Establish a patch management process that ensures timely updates are applied to domain controllers and other related systems.
- Regularly Back Up Active Directory: Performing regular backups of the Active Directory database is essential for recovery in case of data loss or corruption due to accidental changes or cyberattacks. Ensure that backup processes are tested periodically to verify that data can be restored quickly and effectively when needed.
- Implement a Robust Password Policy: Enforce strong password policies that require complex passwords and regular changes. Encourage users to create long passphrases instead of simple passwords, making them more resistant to brute-force attacks. Additionally, educate users about password hygiene and the importance of not sharing credentials.
- Educate Users About Security Threats: Providing ongoing security training for users is crucial in fostering a culture of security awareness within the organization. Training should cover topics such as recognizing phishing attempts, understanding social engineering tactics, and following secure practices when accessing company resources.
- Network Segmentation: Implement network segmentation to isolate critical systems and limit the potential impact of a breach. By separating sensitive data and systems from less secure areas of the network, organizations can reduce the risk of lateral movement by attackers who gain initial access.
By following these best practices, organizations can strengthen their Active Directory security posture, protect sensitive information, and minimize the risk of costly breaches. Regular reviews and updates to security policies will help ensure ongoing protection against emerging threats in an ever-evolving cybersecurity landscape.
Conclusion
Active Directory (AD) stands as a pivotal component within Windows Server environments, offering essential services for managing network resources, user identities, and access controls. Its central role in authentication and authorization makes it an indispensable tool for modern organizations. However, the very importance of AD also makes it a prime target for cyberattacks, underscoring the critical need for robust security measures. Securing AD is not merely an IT task; it is paramount to protecting organizational data, maintaining network integrity, and ensuring business continuity. By thoroughly understanding the potential threats that AD faces, organizations can proactively fortify their defenses. This understanding should drive regular security assessments, enabling the identification of vulnerabilities and misconfigurations that could be exploited by malicious actors. Employing a comprehensive security assessment checklist ensures that no critical area is overlooked, from user account management and password policies to domain controller security and Group Policy Objects.
Implementing best practices for Active Directory security is an ongoing process that requires diligence and adaptability. These practices range from implementing the principle of least privilege and regularly auditing user accounts to hardening domain controllers and enforcing multi-factor authentication. Moreover, staying informed about the latest security threats and emerging best practices is essential to adapting your security measures accordingly. Security is not a one-time fix but an evolving strategy that must keep pace with the ever-changing threat landscape. In conclusion, securing Active Directory is a continuous and multifaceted endeavor that demands a holistic approach. By prioritizing AD security, organizations can safeguard their valuable assets, maintain the trust of their stakeholders, and ensure the long-term success of their operations. Through vigilance, proactive measures, and a commitment to best practices, organizations can significantly enhance the security of their Active Directory systems and protect against the ever-present threat of cyberattacks.

What are the sites where I can practice?
You can practice with Tryhackme, hackthebox or vulnhub. you can search for what I recently saw in 3 projects on github.
are you able to give me any links?