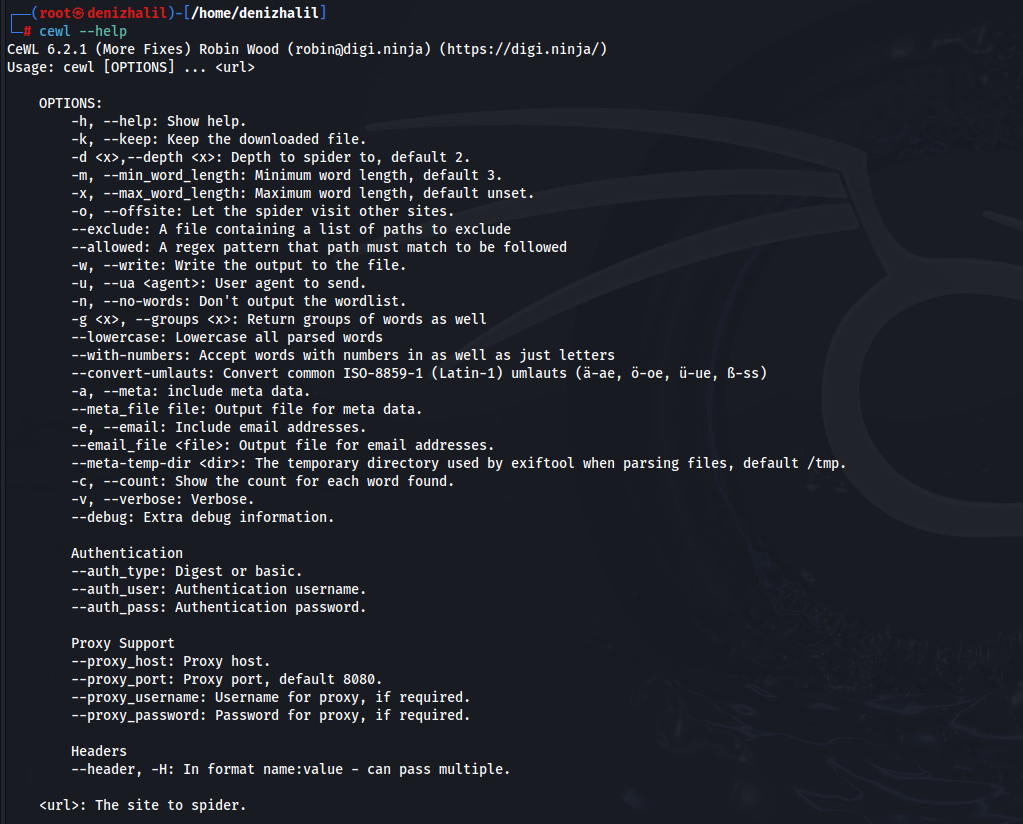
Introduction
CeWL (Custom Word List generator) is a powerful and versatile tool widely utilized in the field of cybersecurity, particularly in penetration testing. This tool enables security professionals to create custom wordlists by crawling specific websites, which can then be employed in various security assessments, including password cracking. The ability to generate tailored wordlists based on the vocabulary and content of a target site significantly enhances the effectiveness of penetration testing efforts. This cheat sheet aims to provide a comprehensive overview of CeWL, detailing its advantages, the types of information it can gather, and practical usage examples.
Learning Objectives
After reading this article, you will:
- Understand the fundamental functions of CeWL.
- Learn about the advantages of using CeWL and the types of information it can collect.
- Discover how to effectively use CeWL to generate wordlists.
What is CeWL?
CeWL is a Ruby-based application designed to crawl a specified URL, extracting words and phrases that are unique to that site. By leveraging the content from targeted websites, users can create tailored wordlists that are particularly useful for password cracking and other security assessments. This tool operates by spidering the website to a defined depth, allowing it to collect a wide array of terms that may be relevant for brute-force attacks or other forms of credential guessing. The flexibility and customization options offered by CeWL make it an invaluable asset for ethical hackers and security researchers who aim to simulate real-world attack scenarios.
Advantages of CeWL and Example Information Gathered
Advantages:
- Customization: One of the standout features of CeWL is its ability to create wordlists that are specifically tailored to the vocabulary used on a given website. This means that the generated lists are more likely to contain relevant terms that could be used as passwords or usernames.
- Comprehensive Crawling: CeWL allows users to specify how deep they want the spidering process to go, which means it can gather data from multiple layers of a website. This comprehensive approach ensures that no potential keywords are overlooked.
- Ease of Use: The command-line interface of CeWL is user-friendly, making it accessible even for those who may not have extensive experience with command-line tools. The straightforward syntax allows users to quickly generate wordlists without complicated setups.
Example Information Gathered:
- Keywords and Phrases: CeWL extracts various keywords and phrases found throughout the website, which can be critical in understanding the terminology used by the target organization.
- Potential Usernames and Password Combinations: By analyzing the content on the site, CeWL can help identify potential usernames and password combinations that may be used by employees or systems.
- Email Addresses: The tool can also extract email addresses from “mailto” links present on web pages, which can be useful for social engineering attacks or further reconnaissance.
- Specific Text from Designated Pages: Users can target specific pages or sections of a website to gather text that may contain sensitive information or relevant keywords.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffeeUsage Examples
1. Basic Wordlist Generation:
cewl http://www.example.com -w output.txt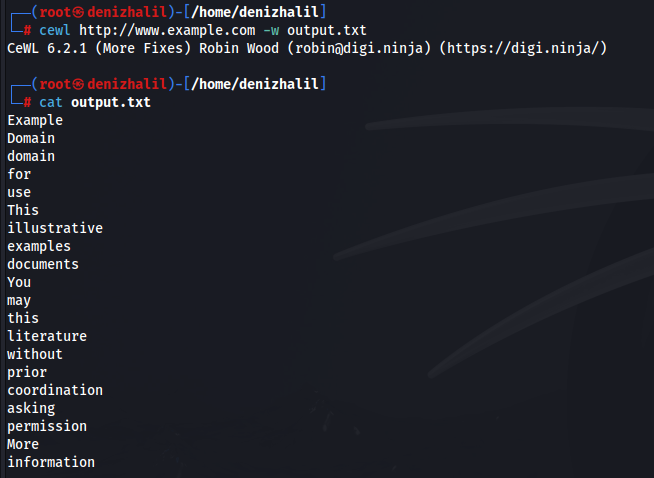
To generate a wordlist from a website:
2. Setting Minimum Word Length:
cewl http://www.example.com -m 10 -w dict.txt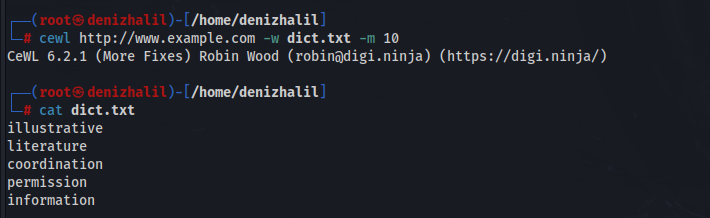
To create a wordlist with words of at least 10 characters:
3. Retrieving Emails:
cewl http://www.example.com -e -n
To extract email addresses from a website:
4. Counting Word Occurrences:
cewl http://www.example.com -c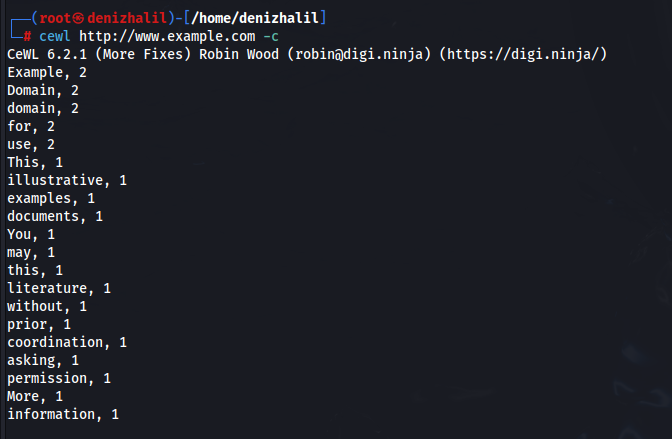
To count how many times each word appears on the site:
5. Increasing Spider Depth:
cewl http://www.example.com -d 3To crawl deeper into the website:
6. Using Authentication:
cewl http://www.example.com/login --auth_type basic --auth_user username --auth_pass password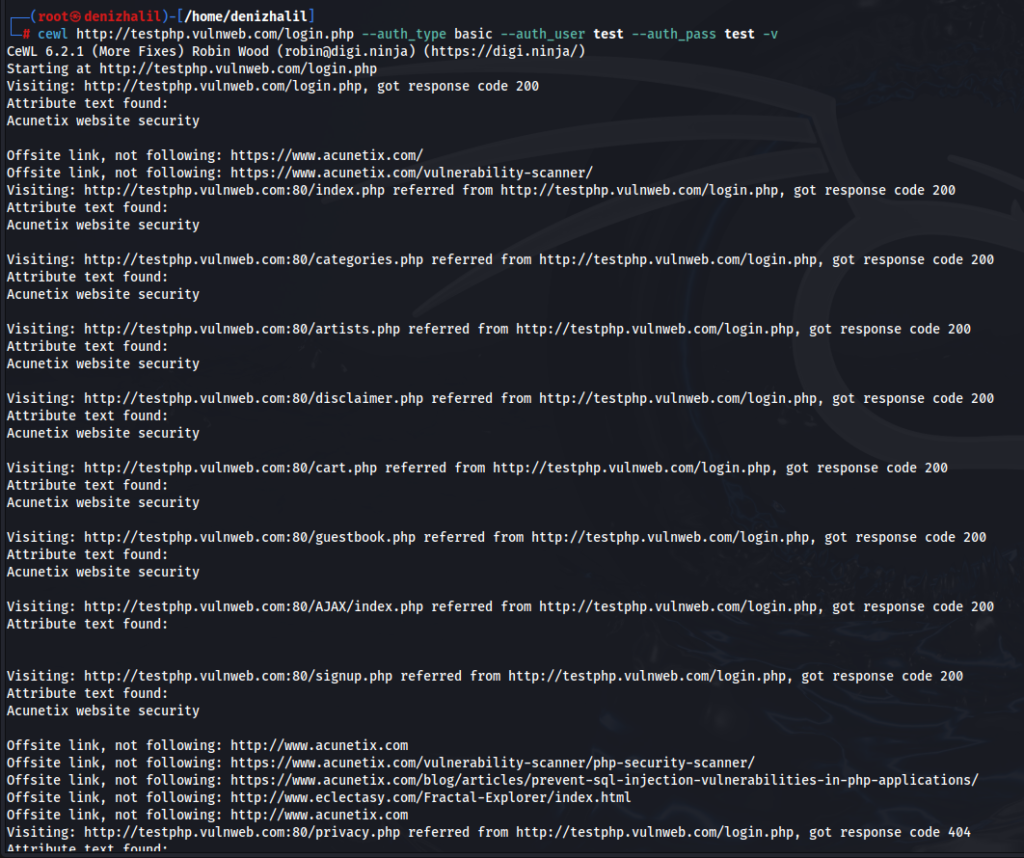
For sites requiring login credentials:
7. Proxy Support:
To use a proxy while crawling:
cewl http://www.example.com --proxy_host proxy_ip --proxy_port proxy_portConclusion
CeWL is an indispensable tool for cybersecurity professionals involved in penetration testing and ethical hacking. Its ability to generate targeted wordlists from specific websites significantly enhances the effectiveness of security assessments and password cracking efforts. By utilizing CeWL, security testers can gain valuable insights into the vocabulary and terminology of their targets, enabling them to develop more effective attack strategies. Understanding how to leverage CeWL’s features is crucial for any cybersecurity practitioner. The tool not only aids in creating customized wordlists but also helps identify potential vulnerabilities within a target’s online presence. By extracting relevant keywords, email addresses, and other critical data, CeWL empowers professionals to simulate real-world attacks more accurately.
In an era where cyber threats are increasingly sophisticated, having the right tools is vital for maintaining robust security measures. This cheat sheet serves as a practical guide for both novice and experienced users looking to effectively utilize CeWL in their security practices. By integrating CeWL into their toolkit, security professionals can enhance their strategies against potential threats, ultimately leading to a more secure digital environment.



I have to say that I use the cewl tool a lot in ctf solutions (thanks for the cheat sheet)