Introduction
In the digital age, safeguarding sensitive information during transmission across networks is paramount. Encryption is a fundamental technique for ensuring data confidentiality and preventing unauthorized access. However, there are legitimate scenarios where analyzing encrypted network traffic becomes necessary, such as for security monitoring, troubleshooting, or debugging. This article explores two scenarios: one where we possess the encryption key, enabling decryption, and another where the key is unavailable, limiting our analysis to metadata. Utilizing Python and the Scapy library, we will delve into network packet analysis and the challenges of working with encrypted data.
Learning Objectives
By the end of this article, you will:
- Understand the fundamentals of network encryption and its significance in data protection.
- Learn how to intercept and analyze encrypted network traffic using Python and Scapy.
- Explore scenarios with and without access to the encryption key, highlighting the challenges and limitations of each.
- Gain practical experience in writing Python scripts to decrypt traffic when the key is available and extract metadata when it is not.
Network Encryption Methods
Network encryption involves converting data into a secure format that can only be decrypted by authorized parties. Common encryption methods include symmetric encryption, where the same key is used for both encryption and decryption, and asymmetric encryption, which uses a pair of keys—one public and one private. Understanding these methods is crucial before diving into decryption and traffic analysis.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $13 on buymeacoffeePurpose of This Project and Its Working Principle
The purpose of this project is to demonstrate how encrypted network traffic can be intercepted and analyzed using Python and Scapy. By doing so, we can either decrypt the data (when the key is available) or analyze the metadata (when the key is not). The project is based on the following principles:
- Scenario 1: When the key is unavailable, the script focuses on analyzing the metadata of the encrypted packets, providing insights into network communication without decrypting the actual content.
- Scenario 2: Decryption is possible when we have access to the encryption key. In this scenario, the Python script will decrypt the captured packets in real-time.
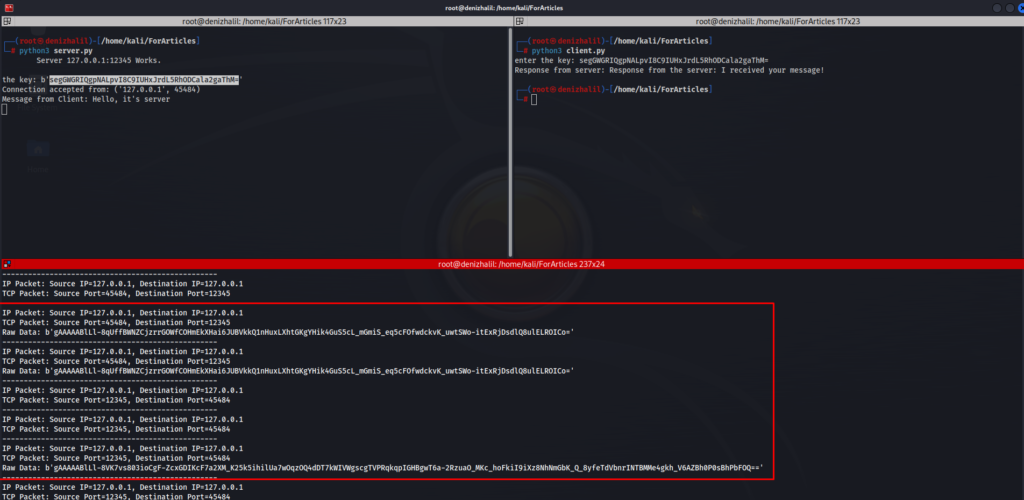
Scenario 1: Analyzing Encrypted Traffic Without the Encryption Key
In this scenario, the encryption key is not available, posing a greater challenge. Without the key, we cannot decrypt the traffic. However, by analyzing the metadata, we can still gather valuable information about the network traffic, such as source and destination IP addresses, ports, and any unencrypted parts of the packets, Python: Creating an Encrypted Server and Client.
from scapy.all import *
def packet_handler(packet):
if packet.haslayer(IP):
src_ip = packet[IP].src
dst_ip = packet[IP].dst
print(f"IP Packet: Source IP={src_ip}, Destination IP={dst_ip}")
if packet.haslayer(TCP):
src_port = packet[TCP].sport
dst_port = packet[TCP].dport
print(f"TCP Packet: Source Port={src_port}, Destination Port={dst_port}")
if packet.haslayer(Raw):
raw_data = packet[Raw].load
print(f"Raw Data: {raw_data}")
if packet.haslayer(UDP):
src_port = packet[UDP].sport
dst_port = packet[UDP].dport
print(f"UDP Packet: Source Port={src_port}, Destination Port={dst_port}")
print("-" * 50)
# Use the sniff function to listen to network traffic
# Replace "lo" with the network interface you want to listen on
sniff(iface="lo", prn=packet_handler, filter="tcp or udp")This script focuses on collecting metadata from the packets. Although the content remains encrypted, the metadata can still provide insights into communication patterns, potentially identifying anomalies or suspicious activity.
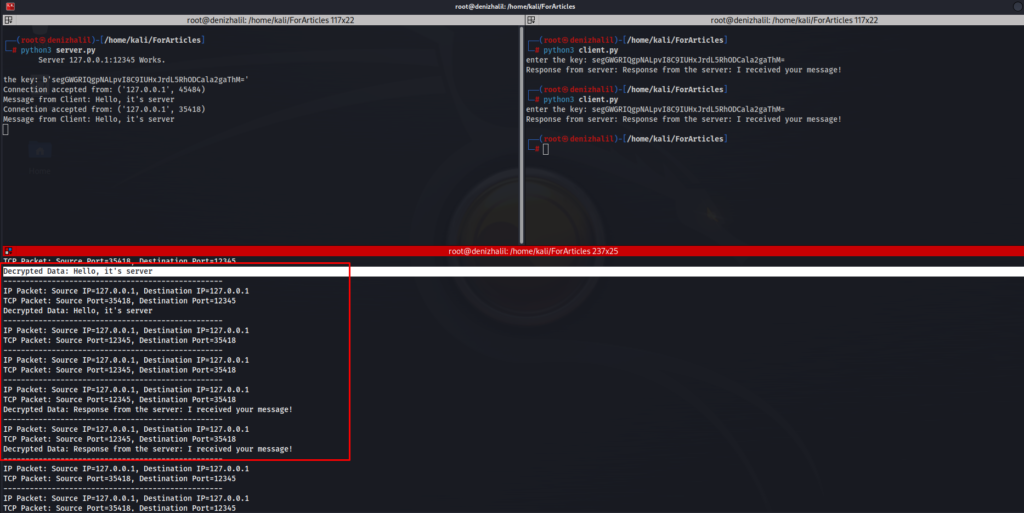
Scenario 2: Analyzing Encrypted Traffic with the Encryption Key
Beginning Your Journey in Programming and Cybersecurity
This book is more than just a technical manual; it’s a journey into the heart of the digital age. Designed for beginners and intermediate enthusiasts
-10% $5 on buymeacoffeeIn this scenario, we assume access to the encryption key, which allows us to decrypt the data packets intercepted during network communication. Using Python and Scapy, we can capture incoming network packets and decrypt them on the fly
from scapy.all import *
from cryptography.fernet import Fernet
# Define the encryption key
key = b'your_secret_key_here' # Replace with your encryption key
def packet_handler(packet):
if packet.haslayer(IP):
src_ip = packet[IP].src
dst_ip = packet[IP].dst
print(f"IP Packet: Source IP={src_ip}, Destination IP={dst_ip}")
if packet.haslayer(TCP):
src_port = packet[TCP].sport
dst_port = packet[TCP].dport
print(f"TCP Packet: Source Port={src_port}, Destination Port={dst_port}")
if packet.haslayer(Raw):
raw_data = packet[Raw].load
try:
decrypted_data = Fernet(key).decrypt(raw_data).decode("utf-8")
print(f"Decrypted Data: {decrypted_data}")
except Exception as e:
print(f"Decryption error: {e}")
if packet.haslayer(UDP):
src_port = packet[UDP].sport
dst_port = packet[UDP].dport
print(f"UDP Packet: Source Port={src_port}, Destination Port={dst_port}")
print("-" * 50)
# Use the sniff function to listen to network traffic
# Replace "lo" with the network interface you want to listen on
sniff(iface="lo", prn=packet_handler, filter="tcp or udp")In this scenario, the script captures packets, checks for the presence of encrypted data, and decrypts it using the provided encryption key. This approach is beneficial for troubleshooting encrypted traffic when the key is known, File Encryption and Decryption for Data Security.
Conclusion
Decrypting encrypted network traffic is a critical skill for network administrators, security professionals, and developers. The two scenarios explored in this article highlight the importance of encryption keys and the limitations faced when the key is unavailable. Python, combined with Scapy, offers a powerful toolkit for network packet analysis, whether you’re decrypting traffic or extracting metadata.
Cyber Security Specialist Coffee Mug
Black -Cyber Security Expert – Cyber Security Specialist Gift IT Network Engineer Computer Engineer Nerd
-10% $17.99 on AmazonIt’s essential to remember that intercepting and analyzing network traffic should always be done ethically and in compliance with relevant laws and regulations. Unauthorized decryption or monitoring can lead to serious legal consequences, Cybersecurity with Python: A Comprehensive Roadmap.
In summary, this article provides practical insights into decrypting and analyzing encrypted network traffic, emphasizing the significance of encryption keys and the analytical possibilities when the key is not accessible. Whether you’re working in a security role or simply exploring network traffic, these techniques can enhance your understanding of network communications and data protection.



Muhteşem olmuş
elinize sağlık teşekkür ederim
Hey last time I saw this article it wasn’t like this, it’s really great that you updated your article.
It’s definitely a great perspective. However, more secure encryption methods need to be used
So if there is such a network, how can I find this password?
For example, you can analyze encrypted packets by adding the wifi password to a wifi network you are listening to with wireshark.
It’s a great article, well done.
I’m one of the people who bought the mastering scapy book on buymeacoffe, it’s really great but we’re waiting for the second part as soon as possible
Dude please keep posting projects like this. I felt like a real hacker
Dude this is really cool, more examples please