Introduction
SQL injection is a common and highly risky security vulnerability encountered in web applications. This vulnerability typically arises when database queries are constructed directly from user input, allowing malicious users to manipulate the system. SQL injection can lead to serious consequences such as data leakage, user account compromise, and complete system takeover. In this article, we will walk through the steps to develop a simple tool using Python to detect SQL injection vulnerabilities. This tool will guide developers and security experts in identifying security weaknesses in their applications. If you’ve been curious about SQL Injection Detection with Python, keep reading to learn more.
Learning Objectives
By the end of this article, you will have gained knowledge in the following areas:
- Understanding why SQL injection is dangerous and how attackers can exploit it.
- Developing a tool using the Python programming language to detect security vulnerabilities in web applications.
- Creating a vulnerable web application using Flask and SQLite and launching attacks against it.
- Learning how to use the developed tool and understanding how it works, especially for SQL Injection Detection with Python.
Purpose of This Project
The aim of this project is to develop a simple Python tool that can detect SQL injection vulnerabilities in web applications. Common security vulnerabilities like SQL injection often result from the unsafe construction of database queries. With this tool, we will identify vulnerable points, enabling a more secure application development process. Additionally, by the end of the project, we will have a deeper understanding of how SQL injection works and how it can be prevented, SQL Injection: Understanding the Threat and Prevention. SQL Injection Detection with Python becomes intuitive with this comprehensive guide.
Let’s Start Coding
The first step of the project is to create a web application vulnerable to SQL injection attacks. Then, we will develop a Python tool to test for these vulnerabilities, focusing on SQL Injection Detection with Python.

Creating a Vulnerable Form with Flask
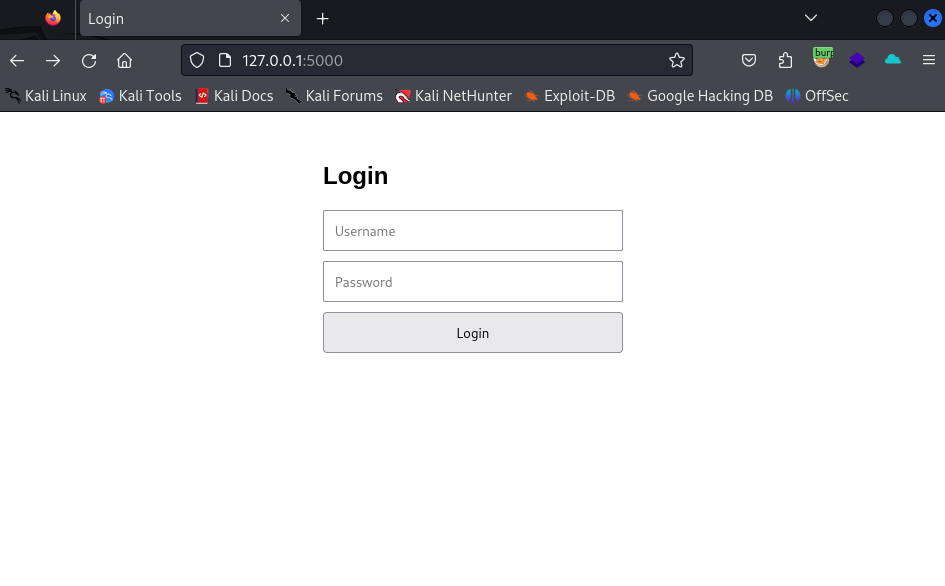
To demonstrate SQL injection attacks and test our detection tool, we will create a simple Flask-based web application. This application will contain a login form that allows users to authenticate using an SQLite database. However, user input will be directly embedded in the SQL query, making the application vulnerable to SQL injection attacks.
from flask import Flask, request, render_template_string
import sqlite3
app = Flask(__name__)
# A simple HTML form
HTML = '''
<html>
<head>
<title>Login</title>
<style>
body { font-family: Arial, sans-serif; }
.container { width: 300px; margin: auto; margin-top: 50px; }
input { margin-bottom: 10px; width: 100%; padding: 10px; }
button { width: 100%; padding: 10px; }
</style>
</head>
<body>
<div class="container">
<h2>Login</h2>
<form method="post" action="/login">
<input type="text" name="username" placeholder="Username">
<input type="password" name="password" placeholder="Password">
<button type="submit">Login</button>
</form>
</div>
</body>
</html>
'''
@app.route('/')
def home():
return HTML
@app.route('/login', methods=['POST'])
def login():
username = request.form['username']
password = request.form['password']
# Unsafe SQL query
query = "SELECT * FROM users WHERE username = '{}' AND password = '{}'".format(username, password)
conn = sqlite3.connect('database.db')
cursor = conn.cursor()
cursor.execute(query)
result = cursor.fetchone()
conn.close()
if result:
return "Welcome, {}!".format(username)
else:
return "Login failed!"
if __name__ == '__main__':
app.run(debug=True)The above application creates a simple login form that accepts username and password input. However, since these inputs are directly incorporated into the SQL query, the application is vulnerable to SQL injection attacks. A user can manipulate the SQL query with improperly structured inputs to gain unauthorized access to the database.
Developing Our SQL Injection Detection Tool
Now, we will develop a basic Python tool to detect SQL injection vulnerabilities in web applications. This tool will use the requests library to send specific HTTP POST requests and analyze the server’s responses, Using SQLMap: A Comprehensive Guide for SQL Injection Testing.
Steps for Developing the Tool
- Import the Required Library: We will start by using the
requestslibrary to send HTTP requests. - Define the Testing Function: We will create a function named
test_sql_injectionto test for SQL injection vulnerabilities. - Specify SQL Injection Payloads: We will prepare a list of typical payloads used in SQL injection attacks.
- Test the Payloads: Each payload will be sent as a POST request to the target application, and the server’s response will be examined.
- Analyze the Responses: The presence of phrases like “Welcome” in the response indicates a successful injection attack.
import requests
def test_sql_injection(url):
# Typical payloads used for SQL injection testing
payloads = ["' OR '1'='1", "' OR '1'='1' --", "' OR 1=1--", "' OR 'x'='x"]
vulnerable = False
for payload in payloads:
# Add payload to form data
params = {'username': payload, 'password': 'random'}
response = requests.post(url, data=params)
# If the response is unexpected, it may indicate an injection
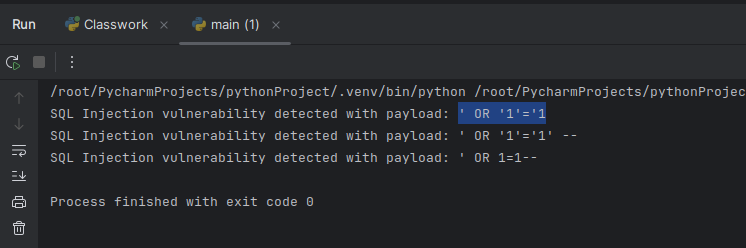
if "Welcome" in response.text:
print(f"SQL Injection vulnerability detected with payload: {payload}")
vulnerable = True
if not vulnerable:
print("No SQL Injection vulnerability detected.")
# URL to be tested
test_url = "http://127.0.0.1:5000/login" # Replace this URL with the one you want to test
test_sql_injection(test_url)This tool sends SQL injection test payloads to the target application and analyzes the response. If the response indicates a successful login, an SQL injection vulnerability has been detected. This simple tool can help developers and security experts identify basic SQL injection vulnerabilities in web applications and discover the vulnerable areas. SQL Injection Detection with Python can be efficiently implemented using this approach.
Conclusion
In this article, we developed a simple tool using Python to detect SQL injection vulnerabilities. Identifying and fixing such vulnerabilities in web applications is crucial for ensuring security. The tool presented here provides a basic level of testing. For more comprehensive security testing, advanced security tools and methodologies should be used, and appropriate improvements should be made for each identified security vulnerability. Hence, mastering SQL Injection Detection with Python is essential for any web developer or security professional.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffee


I recently read Mastering Python for Ethical Hacking, and this article aligns perfectly with the concepts covered in the book. It’s great to see practical applications of the techniques discussed
Thank you so much, have a nice reading
Excellent article! The step-by-step approach makes it easy to understand how SQL injection vulnerabilities work and how to detect them using Python. Great work!
Mastering Python for Ethical Hacking was a game changer for me and provided me with in-depth knowledge on building various security tools. This article complements the book’s teachings by providing a hands-on approach to detecting SQL injection vulnerabilities, and I would also like to point out that it would be appreciated if you could occasionally quote the book and share it here. My advice for beginners would be to buy Denizhalil’s book and follow the site as it continues.
SQL injection vulnerabilities are one of the OWASP Top 10 security risks for web applications, highlighting their prevalence and the need for secure coding practices.
How can this SQL injection detection tool be further improved?
The tool can be enhanced by adding more sophisticated payloads, testing multiple input fields simultaneously, and integrating with a proxy tool like Burp Suite for deeper analysis. Additionally, logging results and exporting them in various formats like JSON or CSV would improve usability.