Introduction
Subdomain takeover is a critical security vulnerability that allows attackers to gain unauthorized control over a subdomain of a legitimate domain through misconfigured or abandoned DNS records. This vulnerability exploits the gap between DNS configuration and actual resource ownership, creating an entry point for sophisticated attacks that leverage the trust associated with legitimate domain names. Unlike traditional vulnerabilities requiring complex technical exploitation, subdomain takeovers often succeed due to simple administrative oversights, making them a persistent and increasingly dangerous threat when exploited through automation and AI-powered reconnaissance tools. Organizations of all sizes remain vulnerable to this attack vector, as demonstrated by high-profile incidents involving technology giants like Uber, Microsoft, and government agencies.
Learning Objectives
By the end of this article, you will understand the following key concepts:
- The fundamental mechanics of how subdomain takeover vulnerabilities are created and exploited by attackers
- The common causes and root causes that lead to vulnerable subdomain configurations within organizations
- The distinction between different exploitation vectors including phishing, cookie theft, and malware distribution
- The reconnaissance and enumeration techniques attackers use to identify vulnerable subdomains
- The tools and methodologies security professionals employ to perform subdomain takeover assessments
- The practical prevention strategies and best practices for DNS management and mitigation
- The security implications of wildcard certificates and overly permissive cookie scoping
- How to implement organizational processes and controls to prevent subdomain takeovers
How Subdomain Takeover Works
A subdomain takeover attack follows a predictable progression that attackers exploit methodically. Organizations commonly delegate subdomains to external services such as GitHub Pages, AWS S3, Heroku, Azure Web Services, Netlify, or Shopify to host specific content or functionality. When creating these delegations, administrators configure DNS CNAME records pointing the subdomain to the third-party service’s domain. However, when services are decommissioned or migrated, organizations frequently forget to remove the corresponding DNS entries, creating dangling DNS records that point to non-existent resources. The attack surface expands significantly because cloud services typically don’t maintain strict verification of subdomain ownership during resource registration. If an organization deletes an AWS S3 bucket named assets.company.s3.amazonaws.com but leaves the CNAME record intact pointing to it, an attacker can register a new bucket with the identical name and assume complete control over the subdomain.
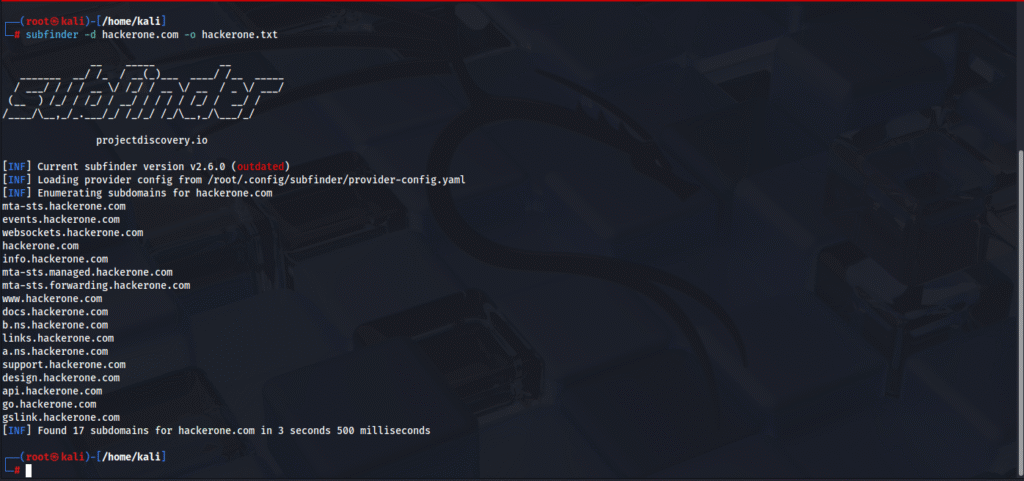
The exploitation process begins with passive reconnaissance, where attackers enumerate an organization’s external infrastructure using subdomain enumeration tools. Tools like Subfinder, assetfinder, and chaos build comprehensive subdomain inventories that can be analyzed for potential vulnerabilities. Once enumeration is complete, attackers perform DNS queries using dig or host commands to reveal CNAME records pointing to third-party services. Successful exploitation requires attempting to claim or register the resource on the identified service using the exposed hostname. For example, if assets.example.com points to an unclaimed S3 bucket endpoint, the attacker creates a new S3 bucket using that same endpoint name and gains full control.
The successful exploitation of this vulnerability depends on three critical conditions: First, the victim’s DNS server must contain a subdomain record pointing to a non-existent or inactive external service endpoint. Second, the service provider must not properly verify subdomain ownership when users attempt to claim or create resources. Third, the subdomain must remain accessible for the attacker to interact with it. When these conditions align, attackers can serve arbitrary content through the compromised subdomain, leveraging the inherent trust users place in legitimate domain names.
Common Causes of Subdomain Takeovers
Subdomain takeover vulnerabilities generally arise not from advanced technical flaws but from lapses in administrative processes and oversight. Many organizations, especially large or rapidly growing ones, find it difficult to maintain up-to-date DNS records as services are frequently added, migrated, or retired. When DNS entries outlive the resources they point to, previously secure subdomains become vulnerable to takeover attacks. Attackers routinely scan for such misalignments, knowing they are both common and easily exploited for further malicious activities such as phishing, defacement, or malware distribution. Most often, the root of the problem lies in how services are decommissioned or transferred. Resources on cloud or SaaS platforms like AWS, Azure, or GitHub Pages are frequently deleted or allowed to expire, but without an accompanying update to the DNS zone file. This results in dangling DNS records—entries that still point to reclaimable endpoints controlled by outside parties. Additionally, the absence of a comprehensive subdomain inventory, lack of inter-team communication, or changes by external vendors can stretch the vulnerability window, sometimes leaving abandoned subdomains forgotten for years.
Misconfigurations also play a critical role, especially when organizations use overly-permissive wildcard DNS or SSL/TLS certificates, or fail to scope cookies correctly. In these cases, even a single neglected subdomain can threaten all related authentication flows and user sessions throughout the primary domain. As providers rarely enforce strict ownership verification, attackers can easily claim released resources and leverage them for attacks.
- Abandoned cloud or SaaS resources with unresolved DNS records: When organizations discontinue projects using cloud or SaaS platforms (such as AWS S3 buckets, Heroku apps, GitHub Pages, or Azure sites) but fail to remove related DNS entries, their subdomains continue pointing to endpoints that attackers can easily claim by re-registering or restoring those resources. This allows attackers to serve arbitrary or malicious content from domains appearing legitimate to users and internal applications.
- Incomplete or improperly managed service decommissioning processes: Many organizations lack formal administrative checklists or workflows for retiring services. As a result, deleting a service or cloud resource is not consistently accompanied by a thorough DNS clean-up. This often leaves orphaned DNS records, exposing the organization to attackers who monitor for such lapses and claim abandoned resources nearly instantly.
- Absence of a centralized, up-to-date subdomain inventory: Without a comprehensive system to track all active subdomains and their ownership across teams and cloud providers, organizations lose visibility. This fragmented management enables overlooked DNS records and forgotten endpoints to persist—sometimes even after team members responsible have moved on or the infrastructure has changed, increasing the risk of unnoticed vulnerabilities.
- Vendor service changes, discontinued offerings, or expired domains: DNS entries may point to third-party services, partner sites, or campaign landing pages managed outside the main organization. If vendors discontinue a service, migrate endpoints, or let domains expire without proper notification, it is easy for attackers to re-register or re-activate those resources, instantly gaining control over your subdomain and any traffic routed to it.
- Misconfigurations such as over-broad wildcard certificates and insecure cookie settings: If SSL/TLS wildcard certificates or session cookies are scoped too broadly (e.g., covering all subdomains or using “.example.com”), attackers who control even a single vulnerable subdomain can intercept authentication flows or valid session tokens for the entire domain. This increases the impact and potential data loss resulting from just one neglected DNS record.
- Insufficient ownership verification or automated monitoring by service providers: Many cloud, SaaS, or third-party providers do not require evidence that the entity registering or configuring a new resource is actually authorized by the domain owner. Moreover, if organizations lack automated systems to monitor for potential subdomain takeovers or new certificate issuances, attackers can claim, configure, and exploit these resources without detection, sometimes for extended periods.
Tools and Techniques to Perform a Subdomain Takeover Attack
Security professionals and attackers employ a variety of specialized tools and techniques to identify and exploit subdomain takeover vulnerabilities. Understanding these tools is essential for both offensive security assessments and defensive preparedness.
Subdomain Enumeration Tools form the foundation of subdomain takeover reconnaissance. Tools like Subfinder, assetfinder, and chaos integrate multiple enumeration techniques including DNS brute-forcing, zone transfer attempts, and certificate transparency log analysis. These tools generate comprehensive lists of all resolvable subdomains associated with a target domain. For example, running Subfinder against example.com might identify hundreds of subdomains including development, staging, legacy, and internal service endpoints that administrators may have forgotten existed.
DNS Analysis and CNAME Detection requires tools capable of querying DNS records and identifying CNAME records pointing to external services. The dig command provides direct DNS query capabilities: dig subdomain.example.com CNAME reveals whether a subdomain delegates to an external service. More sophisticated tools automate this process across thousands of subdomains, filtering for CNAMEs pointing to known vulnerable services like AWS, Azure, GitHub, and Heroku endpoints.
Nuclei:
Nuclei is a powerful vulnerability scanner that automates subdomain takeover detection through template-based scanning. Security researchers employ Nuclei with subdomain takeover templates to identify vulnerable endpoints across large target scopes. The typical workflow involves enumeration, filtering for potential takeover candidates, then running Nuclei with subdomain-specific templates
nuclei -l subdomains.txt -t /nuclei-templates/http/takeovers/detect-all-takeovers.yaml -o results.txt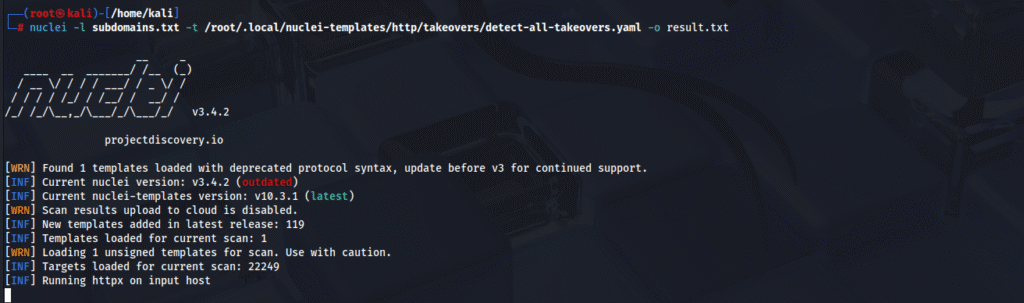
Nuclei templates match service-specific fingerprints like error messages, status codes, and response bodies. When a CNAME points to an unclaimed S3 bucket, for example, AWS returns a specific 404 response that Nuclei templates recognize as a takeover opportunity. Security researchers have reported discovering 100-1000+ vulnerable subdomains using Nuclei on single targets, though manual verification remains necessary to eliminate false positives.
Subjack:
Subjack is a Go-based scanner that identifies hostile subdomain takeovers by matching response fingerprints against known service signatures. Subjack checks subdomains that don’t return NXDOMAIN responses, examining error pages and response content to identify services where the resource can be claimed. The tool maintains an extensive fingerprint database for common cloud providers and SaaS platforms
subjack -w subdomains.txt -t 100 -timeout 30 -o results.json
Subzy:
Subzy is another Go-based tool that works through fingerprint matching based on known service signatures, supporting 50+ vulnerable platforms including AWS S3, Azure, GitHub Pages, Heroku, and Netlify. Subzy offers parallel checking capabilities for rapid scanning of large subdomain lists:
subzy run --targets subdomains.txt --timeout 5000 --hide_fails
Conclusion
Subdomain takeover vulnerabilities represent a persistent and increasingly dangerous threat exploited through automation and AI-powered reconnaissance. The combination of widespread administrative oversights, inadequate organizational processes, and permissive cloud service policies creates an environment where these vulnerabilities remain prevalent. Unlike vulnerabilities requiring complex technical exploitation, subdomain takeovers often succeed through simple DNS neglect and forgotten resources. Organizations can significantly reduce their risk through disciplined DNS management, comprehensive subdomain inventory maintenance, and clear organizational procedures for service decommissioning. The implementation of automated monitoring tools, regular DNS audits, and proper certificate scoping creates multiple defensive layers that prevent attackers from claiming abandoned subdomains. Security professionals conducting penetration tests and red team exercises should include subdomain takeover assessments as critical components of external attack surface evaluation. By understanding both the offensive techniques and defensive countermeasures, security teams can identify and remediate these vulnerabilities before attackers exploit them, transforming a widespread vulnerability into a controlled and manageable risk.
The path to securing subdomains requires a combination of technical controls, organizational discipline, and continuous monitoring. As cloud services proliferate and organizations manage increasingly complex DNS infrastructures, the importance of treating DNS hygiene with the same rigor as other security controls becomes paramount.
Common Questions and Answers
A subdomain takeover occurs when an attacker gains control over a subdomain that points to a deprovisioned or unclaimed external resource—such as a cloud service, SaaS platform, or expired domain—by registering or claiming the underlying endpoint. This typically happens due to outdated DNS records (dangling DNS), where the target subdomain’s DNS entry remains active despite the original service being deleted or moved.
CNAME records are especially susceptible to subdomain takeover, as they often point to third-party cloud services. However, A, MX, NS, and TXT records can also introduce risks if they reference expired domains, decommissioned infrastructure, or external resources that can later be claimed by attackers.
Risks include loss of control over subdomain content, phishing (using the legitimate subdomain to steal credentials), session or cookie harvesting (especially when session cookies are set for all subdomains), brand damage, and potential escalation to more advanced attacks such as XSS, CSRF, and CORS bypass. Attackers may also obtain valid SSL certificates for the compromised subdomain, increasing user trust in malicious activity.
Detection involves regular DNS audits, automated scanning for dangling DNS entries, and monitoring for new certificate issuances for their domains. Prevention requires promptly removing or updating DNS records after decommissioning resources, restricting wildcard DNS and certificate usage, and establishing robust change management for DNS configurations.
Large organizations frequently manage hundreds or thousands of subdomains across multiple teams and cloud providers. Without centralized subdomain tracking and coordination, DNS entries for decommissioned resources often go unnoticed, creating more opportunities for attackers to discover and exploit such lapses.
References:

