Introduction
The rapid advancement of digital technologies has led to a significant increase in the number of internet-connected devices across all sectors. Critical infrastructures including energy plants, transportation networks, healthcare systems, and public services are now more interconnected than ever before. This digital transformation brings undeniable benefits, such as improved operational efficiency, enhanced monitoring capabilities, and streamlined management processes. However, it also introduces new vulnerabilities, as these vital systems become accessible to a wide range of actors, both legitimate and malicious. Shodan, a specialized search engine, plays a pivotal role in this landscape. Unlike traditional search engines that index web pages, Shodan scans the internet for devices, servers, and open ports, indexing their service banners and making it possible to discover exposed or misconfigured systems with a simple query. Security professionals, researchers, and even threat actors use Shodan to identify vulnerabilities in critical infrastructure, making it a double-edged sword in the field of cybersecurity.
This article delves into the use of Shodan dorks custom search queries tailored to find specific types of devices or vulnerabilities for the discovery of critical infrastructure. By examining real-world examples and practical search techniques, it demonstrates how easily exposed systems can be identified and what risks they face. Additionally, the article highlights essential security measures that organizations must implement to protect their critical assets from cyber threats. Through proactive discovery, continuous monitoring, and robust defense strategies, the risks associated with the increasing connectivity of shodan critical infrastructure can be effectively managed.
Learning Objectives
- Understand Shodan’s core functionality and the concept of dorks
- Identify classes of critical infrastructure and how to discover them via Shodan
- Apply sample Shodan dorks for various infrastructure types
- Recognize fundamental security measures for protecting critical systems
- Develop awareness of ethical and responsible cybersecurity practices
Critical Infrastructure Discovery with Shodan
Shodan is a unique and powerful search engine designed to index service banners and metadata from internet-facing devices, rather than traditional web content. By continuously scanning the global internet, Shodan collects detailed information about devices such as servers, routers, webcams, industrial controllers, and more. This information includes open ports, running services, software versions, and even configuration details, all of which can be critical in assessing the security posture of a system. Critical infrastructure components—including industrial control systems (ICS), SCADA devices, energy grids, transportation networks, and public sector technologies—are increasingly connected to the internet for remote management and monitoring. However, when these systems are misconfigured, left with default credentials, or exposed without adequate security measures, they become visible and accessible through Shodan’s search interface. This visibility can be exploited by both security professionals and adversaries.
Shodan dorks—customized search queries—allow users to filter and pinpoint specific devices or vulnerabilities based on criteria such as device type, protocol, port number, software version, or even geographic location. For example, a security analyst might use a dork to search for industrial PLCs in a particular country, while a penetration tester could look for medical devices running outdated software. These targeted searches are invaluable for vulnerability assessments, compliance checks, and proactive defense planning. However, this same capability also presents significant risks. Malicious actors can leverage Shodan to rapidly identify and target exposed critical infrastructure, potentially leading to data breaches, service disruptions, or even physical harm. The dual-use nature of Shodan underscores the importance of proper configuration, regular audits, and robust cybersecurity practices for all organizations responsible for critical systems. Ultimately, understanding how Shodan operates—and how it can be used both defensively and offensively—is essential for anyone involved in cybersecurity, penetration testing, or infrastructure protection.
Critical Infrastructure Classes and Shodan Dork Examples
1. Energy Systems
- Power Grids:
"Server: gSOAP/2.8" "Content-Length: 583"(Electric charging stations/smart grids) - Wind Turbines:
http.title:"Nordex Control"ortitle:"xzeres wind"(Turbine control panels) - Power Management:
http.title:"Tesla PowerPack System"(Energy storage systems)
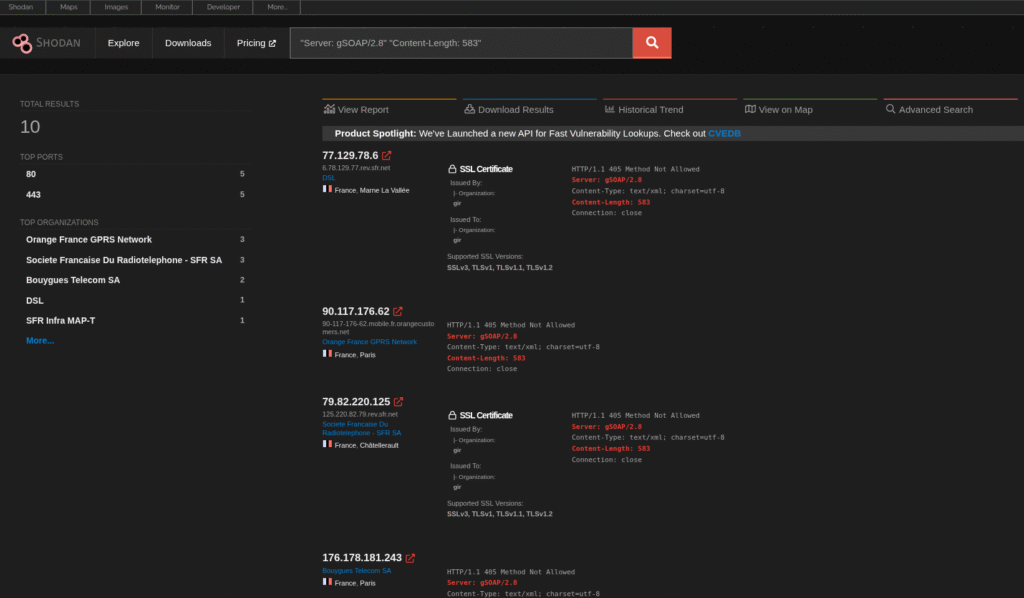
2. Industrial Control Systems (SCADA/ICS)
- Siemens PLCs:
"Siemens, SIMATIC" port:161(PLCs accessible via SNMP) - Mitsubishi Systems:
port:5006,5007 product:mitsubishi(MELSEC-Q protocol devices) - Cooling Systems:
"Server: CarelDataServer"(Industrial refrigeration units)
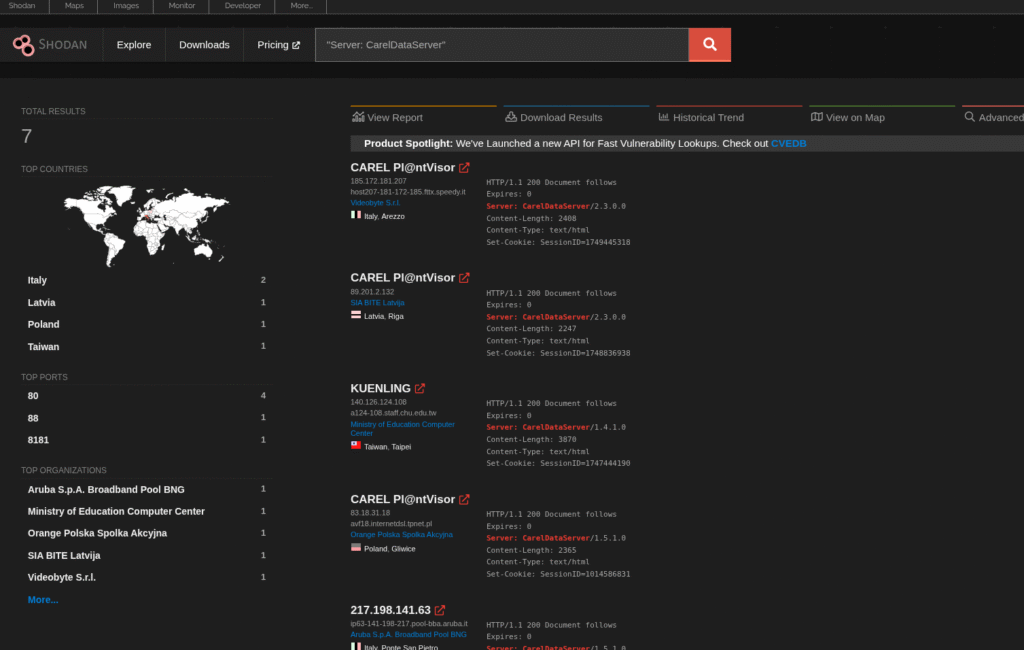
3. Transportation Infrastructure
- Traffic Control:
mikrotik streetlight(Traffic lights/red-light cameras) - License Plate Recognition:
P372 "ANPR enabled"(Automatic number plate systems) - Maritime Equipment:
"Cobham SATCOM" OR ("Sailor" "VSAT")(Ship satellite comms)
4. Public Systems
- Voting Machines:
"voter system serial" country:US(US election systems) - Prison Phones:
"[2J[H Encartele Confidential"(Prison payphones) - Medical Devices:
"DICOM Server Response" port:104(Medical imaging devices)
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffee5. Critical Network Infrastructure
- RDP Access:
"\x03\x00\x00\x0b\x06\xd0\x00\x00\x124\x00"(Unsecured Remote Desktop) - Router Configs:
html:"def_wirelesspassword"(Routers exposing default WiFi passwords) - Database Servers:
"MongoDB Server Information" port:27017 -authentication(Auth-free MongoDB)
Effective Dork Crafting Techniques
- Geo-Filtering:
country:"TR" city:"Istanbul"(Narrows devices to target regions) - Port/Protocol Combo:
product:"Modbus" port:502(Scans industrial protocols) - Org Filter:
org:"Türkiye Elektrik İletim A.Ş"(Org-specific discovery) - Time-Based:
before:"2025-05-01"(Systems updated before a date)
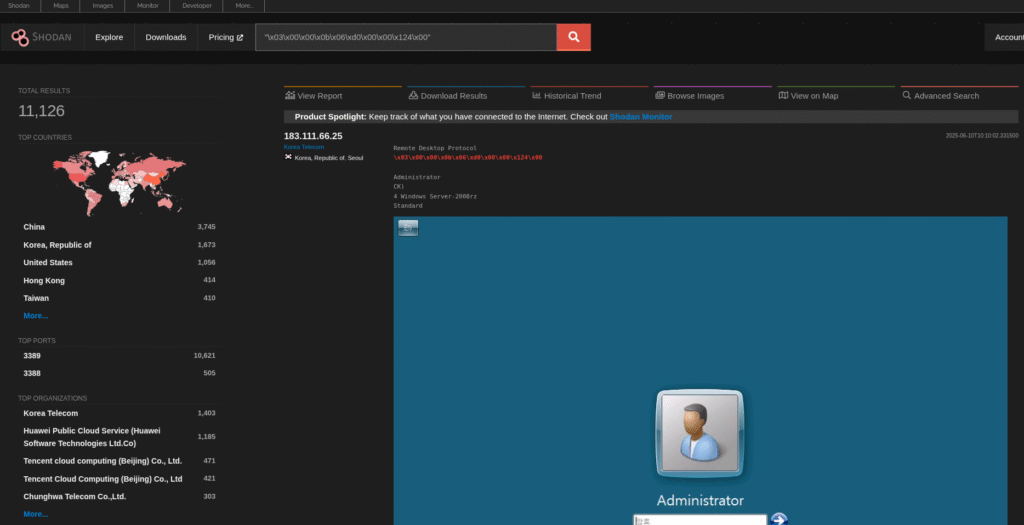
Essential Security Measures for Critical Infrastructure
Protecting critical infrastructure from cyber threats requires a comprehensive, multi-layered security strategy that addresses both technical and human factors. The following measures are essential for reducing risk and ensuring the resilience of vital systems:
- Access Controls: Strong authentication mechanisms must be enforced to ensure that only authorized personnel can access critical systems. This includes implementing multi-factor authentication (MFA), enforcing strong password policies, and regularly reviewing user privileges. Limiting access based on the principle of least privilege reduces the attack surface and helps prevent unauthorized actions within sensitive environments.
- Patch and Update Management: Keeping all devices, operating systems, and applications up to date is vital for mitigating known vulnerabilities. Organizations should establish a structured patch management process to promptly apply security updates and firmware patches. Automated solutions can help monitor for new vulnerabilities and streamline the update process, minimizing the window of exposure.
- Network Segmentation: Segregating critical infrastructure networks from public or less secure networks is a fundamental defense strategy. By isolating sensitive systems—such as SCADA, ICS, or medical devices—from the broader corporate or public internet, organizations can contain potential breaches and limit lateral movement by attackers. Virtual LANs (VLANs), firewalls, and air-gapping are common techniques for effective segmentation.
- Firewalls and IDS/IPS: Deploying robust firewalls and intrusion detection/prevention systems (IDS/IPS) at network boundaries is crucial for monitoring, filtering, and blocking unauthorized or suspicious traffic. These technologies provide real-time alerts and can automatically respond to certain types of attacks, helping to identify and mitigate threats before they escalate.
- Regular Audits: Continuous security assessments are necessary to identify misconfigurations, vulnerabilities, and unauthorized exposures. Tools like Shodan can be used proactively to scan your own infrastructure, revealing devices or services that may be unintentionally exposed to the internet. Regular penetration testing and vulnerability scanning should be part of the security lifecycle.
- Awareness and Training: Human error remains a significant risk factor. Ongoing cybersecurity awareness programs help staff recognize phishing attempts, social engineering tactics, and emerging threats. Training should be tailored to different roles within the organization and updated regularly to reflect the evolving threat landscape.
- Automation and Monitoring: Integrating the Shodan API with programming languages like Python allows for automated and continuous monitoring of internet-facing assets. Automated scripts can alert administrators to new exposures or vulnerabilities as soon as they are detected, enabling rapid response and remediation.
- Additional Tools: Advanced cybersecurity tools such as Kali Linux, Gophish, and Termux provide powerful capabilities for penetration testing, phishing simulation, and network analysis. These tools are invaluable for simulating real-world attacks, identifying weaknesses, and validating the effectiveness of existing security controls.
By implementing these measures, organizations can significantly strengthen the security posture of their critical infrastructure. A proactive approach—combining technical defenses, regular assessments, and a culture of security awareness—ensures that vital systems remain resilient against both current and emerging cyber threats.
Conclusion
Shodan critical infrastructure dorks provide cybersecurity professionals with a unique and powerful means to assess the visibility and vulnerability of critical infrastructure on the internet. Their ability to quickly identify exposed systems, misconfigurations, and outdated technologies makes them invaluable in the hands of security teams tasked with protecting essential services such as energy grids, transportation networks, and public sector assets. However, this same power comes with significant ethical and legal responsibilities. The use of Shodan and similar tools must always be governed by a strong sense of professional ethics, respect for privacy, and adherence to all applicable laws and regulations. Infrastructure owners and operators should not view exposure as a one-time risk, but rather as an ongoing challenge that requires continuous attention. Regular security audits, vulnerability assessments, and penetration tests—using tools like Shodan, Kali Linux, and other advanced platforms—are essential for maintaining a strong security posture. Proactive discovery of potential weaknesses, combined with robust access controls, timely patch management, and comprehensive staff training, forms the foundation of effective cyber defense.
Ultimately, the security of critical infrastructure depends not only on technology, but also on a culture of vigilance and ongoing education. By fostering awareness, investing in continuous monitoring, and embracing a proactive approach to risk management, organizations can significantly reduce their exposure to cyber threats and ensure the resilience of the systems that underpin modern society.
You May Be Interested In:
Professional Solutions: Contact Us

For organizations seeking advanced and tailored cybersecurity solutions for critical infrastructure, our expert team is ready to assist. Whether you need in-depth vulnerability assessments, penetration testing, or comprehensive security strategy development, we provide professional services designed to protect your most vital systems. Reach out to us today to discuss your needs and discover how we can help strengthen your infrastructure’s cyber resilience.
For detailed information about our services, to request a custom quote, or to get in touch directly, please visit our Contact Information page.
You can also reach us via email at:
halildeniz313@gmail.com
More detail with:
Cyber Security Services


Can I find a target and attack like this with shodan?
Of course, an unauthorized attack may cause serious legal problems, the information shared here should only be used within the legal framework and with appropriate permissions.