Introduction
In today’s interconnected digital environment, the security of our online communications is more crucial than ever. Every day, individuals and organizations exchange sensitive information—such as passwords, financial data, and private messages—across various digital platforms. As dependence on these technologies grows, so does the risk of cyber threats targeting the privacy and integrity of our data. One of the most significant and stealthy threats to secure communication is the Man-in-the-Middle (MITM) attack. In this type of cyberattack, an attacker covertly intercepts and can even alter the communication between two parties who believe they are communicating directly and securely. The attacker may eavesdrop on the conversation, steal confidential information, or inject malicious content, all without the knowledge of the victims.
MITM attacks can lead to serious consequences, including identity theft, financial loss, unauthorized access to accounts, and large-scale data breaches. As attackers continue to develop more sophisticated methods, understanding how MITM attacks operate and how to defend against them has become a fundamental part of cybersecurity for both individuals and organizations.
Learning Objectives
- Understand the definition and basic principles of a MITM attack
- Recognize the different types of MITM attacks
- Learn how MITM attacks are executed
- Identify effective prevention methods against MITM attacks
What is MITM (Man in the Middle) Attack
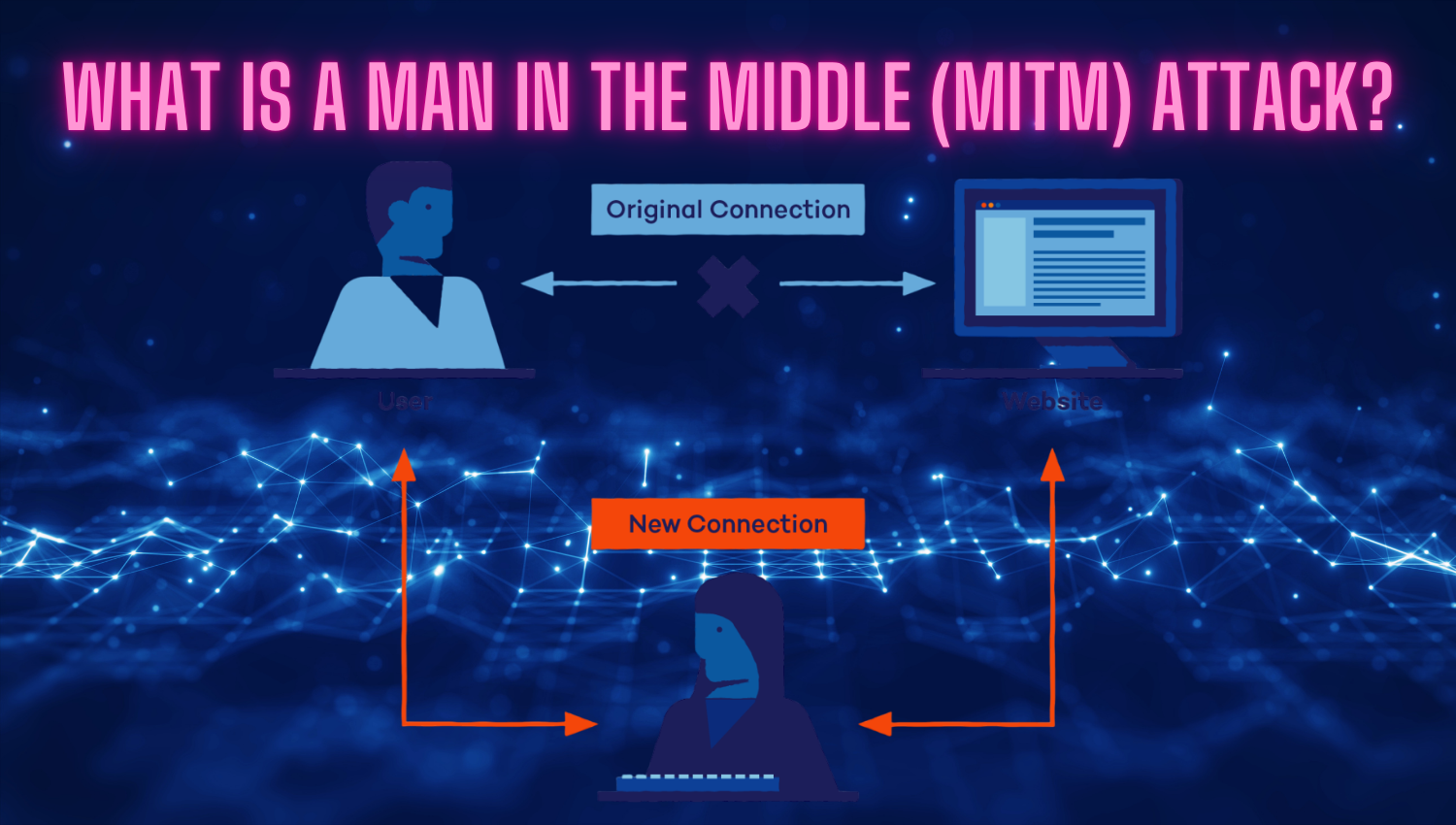
A Man-in-the-Middle (MITM) attack is a sophisticated cyberattack in which an attacker secretly places themselves between two parties who believe they are communicating directly with each other. In this scenario, the attacker intercepts the data being exchanged, allowing them to monitor, capture, and even manipulate the information in real time. Both parties remain unaware of the attacker’s presence, as the communication appears normal from their perspectives. MITM attacks are particularly dangerous because they enable attackers not only to eavesdrop on private conversations but also to alter the content of the messages or inject malicious data. This means an attacker could, for example, change banking details during a transaction or redirect login credentials to their own systems. The technique is commonly used to steal sensitive information such as usernames, passwords, credit card numbers, and confidential business data.
Attackers often exploit vulnerabilities in unsecured networks—like public Wi-Fi hotspots—or use methods such as DNS spoofing, ARP spoofing, or fake SSL certificates to position themselves as the “man in the middle.” As a result, MITM attacks can target anyone using digital communications, from individual users to large organizations, making awareness and prevention crucial components of cybersecurity.
How do MITM attacks work?
MITM attacks are multi-stage operations that allow attackers to covertly intercept, monitor, and manipulate communications between two unsuspecting parties. The process typically unfolds in four key phases:
- 1. Interception: The attacker first gains access to the communication channel between the victim and the intended recipient. This is often achieved by exploiting vulnerabilities in networks, such as unsecured or poorly protected Wi-Fi hotspots, or by using techniques like ARP spoofing, DNS spoofing, or setting up fake Wi-Fi access points. Attackers may also use phishing emails or malicious software to lure victims into connecting through compromised channels. During this phase, the attacker positions themselves so that all data transmitted between the two parties passes through their system, enabling them to observe and capture sensitive information in real time.
- 2. Eavesdropping and Data Capture: Once in position, the attacker begins to monitor the data flow between the parties. This can include intercepting emails, login credentials, credit card numbers, or any other sensitive information exchanged. Eavesdropping can be passive—where the attacker simply observes the communication without altering it—or active, where they may inject malicious code or requests into the data stream to gather more information or escalate the attack.
- 3. Decryption and Manipulation: Many communications are encrypted to protect against interception. In this phase, the attacker attempts to decrypt the captured data using various methods, such as SSL stripping (downgrading HTTPS to HTTP), creating fake SSL certificates, or exploiting vulnerabilities in encryption protocols. Once decrypted, the attacker can read, modify, or inject new data into the communication. This allows them to steal login credentials, change transaction details, or redirect victims to malicious websites without detection.
- 4. Relay and Impersonation: The attacker relays the (potentially altered) messages between the two parties, ensuring that neither side realizes their communication has been compromised. By impersonating each party to the other, the attacker maintains the illusion of a secure, direct connection. This enables further exploitation, such as hijacking sessions, conducting fraudulent transactions, or spreading malware. In some cases, attackers use the information gained to launch broader attacks against organizations or individuals, leading to more severe breaches or long-term infiltration.
Through these four phases—interception, eavesdropping and data capture, decryption and manipulation, and relay and impersonation—MITM attacks can be highly effective and difficult to detect, posing significant risks to both individuals and organizations.
Mastering Linux Networking and Security
As you progress through this book, you’ll gain the skills necessary to not only manage networks but also protect them from the ever-evolving threats that exist in today’s digital landscape.
-35% 22 on buymeacoffeeWhat are the types of MITM?
Man-in-the-Middle (MITM) attacks come in many forms, each leveraging different techniques and vulnerabilities to intercept or manipulate communications between two parties. Understanding these attack types is crucial for effective cybersecurity defense. Below is a detailed exploration of the most common and impactful MITM attack types:
- HTTPS Spoofing: Attackers present a fake SSL/TLS certificate to users, tricking them into believing their connection is secure. The fake certificate is often obtained through compromised Certificate Authorities (CAs) or by exploiting browser vulnerabilities. Users unwittingly trust the attacker’s server, allowing the attacker to intercept and potentially alter all transmitted data.
- SSL/TLS Stripping: This technique involves downgrading a secure HTTPS connection to an unsecured HTTP connection. The attacker intercepts the initial request, prevents the upgrade to HTTPS, and keeps the session unencrypted. As a result, sensitive information such as login credentials and credit card numbers is transmitted in plain text, making it easy for the attacker to harvest.
- ARP Spoofing: In local area networks (LANs), attackers manipulate the Address Resolution Protocol (ARP) to associate their own MAC address with the IP address of a legitimate device. This allows them to intercept or redirect traffic intended for that device, enabling eavesdropping and data theft without the victim’s knowledge.
- DNS Spoofing/Poisoning: Attackers corrupt the Domain Name System (DNS) cache, causing legitimate DNS queries to be redirected to malicious servers. Victims are sent to fake websites that look identical to the real ones, where their sensitive information is captured. This technique is especially dangerous because it can affect multiple users on a network.
- Session Hijacking: Attackers steal session cookies or authentication tokens from a user’s web browser. With these tokens, the attacker can impersonate the user and gain unauthorized access to accounts, perform transactions, or extract confidential data. Session hijacking often targets online banking, e-commerce, and enterprise applications.
- Man-in-the-Browser (MITB): Malware infects a user’s web browser, allowing the attacker to intercept or manipulate browser activity in real time. The malware can modify web pages, inject malicious scripts, or redirect users to phishing sites, all while remaining hidden from the user and security software.
- Evil Twin Attack: Attackers create a fake Wi-Fi hotspot that mimics a legitimate one, often using a similar or identical name. Unsuspecting users connect to the fake hotspot, allowing the attacker to monitor all internet traffic, capture login credentials, and inject malware into connected devices.
- Email Hijacking: Attackers gain control over email accounts, often through phishing or credential theft. They monitor incoming and outgoing emails, intercept sensitive communications, and may impersonate legitimate contacts to trick others into revealing information or transferring funds.
- Replay Attack: Attackers capture valid data transmissions (such as authentication tokens or payment requests) and resend them to the server. This allows the attacker to repeat actions, gain unauthorized access, or disrupt operations. Replay attacks are particularly effective when encryption or session management is weak.
Beyond these, other notable MITM attack types include IP spoofing (where attackers impersonate legitimate IP addresses to redirect traffic), packet injection (inserting malicious packets into data streams), and rogue access point attacks (using unauthorized wireless access points to intercept traffic). Each of these techniques exploits different aspects of network and application security, making MITM attacks a persistent and evolving threat in the cybersecurity landscape. Organizations and individuals must remain vigilant, employing strong encryption, authentication, and monitoring to defend against these multifaceted attacks.
Man in the middle attack prevention
Preventing Man-in-the-Middle (MITM) attacks requires a multi-layered approach that combines technical controls, secure user behavior, and ongoing vigilance. Here are comprehensive strategies and best practices to help protect individuals and organizations from MITM threats:
- Use Strong Encryption Protocols: Always ensure that sensitive communications are encrypted using robust protocols such as HTTPS, TLS, or SSL. Enforcing HTTPS on websites and using browser settings or plugins to force secure connections helps protect data in transit from interception and tampering.
- Secure Wi-Fi Networks and Router Credentials: Use Wi-Fi networks with strong encryption (WPA2 or WPA3) and avoid connecting to open or unsecured public Wi-Fi whenever possible. Always change default router login credentials to strong, unique passwords to prevent attackers from gaining administrative access and altering network settings.
- Virtual Private Network (VPN): Utilize VPNs to encrypt all data transmitted between your device and the internet, especially when accessing sensitive information over public or untrusted networks. A properly configured VPN can make intercepted data unreadable to attackers.
- Multi-Factor Authentication (MFA): Enable MFA on all critical accounts and systems. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they intercept credentials.
- Network Segmentation and Access Controls: Segment your network to isolate sensitive systems and data. Implement strict access controls and least privilege principles to limit the movement of attackers within your network if they gain initial access.
- Regularly Update Software and Devices: Keep all operating systems, applications, firmware, and security tools up to date with the latest patches. Attackers often exploit known vulnerabilities in outdated software to launch MITM attacks.
- Monitor Network Traffic: Continuously monitor your network for unusual activity or suspicious traffic patterns that could indicate a MITM attack. Deploy intrusion detection and prevention systems (IDPS) and maintain detailed logs for forensic analysis.
- Implement DNS Security Measures: Use DNS Security Extensions (DNSSEC) to authenticate DNS responses and prevent DNS spoofing or poisoning attacks. DNSSEC helps ensure that users are directed to legitimate websites rather than malicious lookalikes.
- Educate Users: Train users to recognize phishing attempts, suspicious links, and the risks of connecting to unknown networks. Awareness is a critical defense against social engineering tactics that often precede MITM attacks.
- Public Key Authentication: Use public key pair-based authentication (such as RSA) for sensitive communications and services. This helps verify the identity of communicating parties and prevents impersonation by attackers.
By implementing these layered defenses—ranging from encryption and authentication to user awareness and network monitoring—you can significantly reduce the risk of falling victim to MITM attacks and better protect your digital communications and sensitive data.
Conclusion
Man-in-the-Middle (MITM) attacks continue to be among the most persistent and covert threats in the field of cybersecurity. By silently inserting themselves into communication channels, attackers are able to intercept, manipulate, and exploit sensitive information—often without the knowledge of the victims. The consequences can range from stolen credentials and financial losses to large-scale data breaches that compromise organizational integrity. To effectively defend against MITM attacks, both individuals and organizations must adopt a layered security approach. This includes implementing strong encryption protocols, enforcing multi-factor authentication, maintaining up-to-date systems, and fostering user awareness about the risks of insecure networks and social engineering tactics. Ongoing vigilance and proactive monitoring are essential, as attackers continually develop more sophisticated techniques to bypass traditional defenses.
Ultimately, the responsibility for secure digital communication lies with every participant in the network. By prioritizing cybersecurity best practices and staying informed about evolving threats, it is possible to significantly reduce the risk of MITM attacks and protect valuable data in an increasingly connected world.