Introduction
In today’s digital landscape, securing sensitive information is paramount. One of the most common methods for protecting passwords is through hashing, a technique that transforms plain text into a fixed-size string of characters. However, even the most secure hashes can be vulnerable to brute-force attacks, where an attacker systematically attempts every possible combination to find the original input. This article will guide you through creating a simple brute-force hash cracker using the SHA-256 hashing algorithm in Python. By the end of this tutorial, you will have a comprehensive understanding of hashing, its applications, and how to implement a brute-force attack effectively.
Learning Objectives
By the end of this article, you will be able to:
- Understand Hashing: Gain insights into what hashing is and why it is essential in data security.
- Implement a Brute-Force Hash Cracker: Write a Python script that can crack SHA-256 hashes using a wordlist.
- Utilize
hashlib: Learn how to use Python’shashliblibrary for hashing operations. - Enhance User Experience: Improve the user interface with real-time feedback and colored output using the
coloramalibrary. - Explore Ethical Considerations: Understand the ethical implications of using brute-force techniques in cybersecurity.
What is Hashing?
Hashing is a fundamental process in computer science and cryptography that involves transforming any given input—be it text, numbers, or files—into a fixed-length string of characters, often referred to as a hash value or digest. This transformation is achieved through a specialized mathematical function known as a hash function. One of the most widely used hash functions is SHA-256 (Secure Hash Algorithm 256-bit), which outputs a 256-bit hash value. The resulting hash serves as a unique identifier for the original input data, allowing for efficient data retrieval and integrity verification. The significance of hashing extends beyond mere data representation; it plays a crucial role in securing sensitive information. For instance, when passwords are stored in databases, they are typically hashed rather than kept in plain text. This means that even if an attacker gains access to the database, they encounter only the hash values, making it computationally infeasible to retrieve the original passwords. Thus, hashing provides an essential layer of security in various applications.
Hash functions exhibit several critical properties that make them suitable for security-related applications:
- Deterministic: A hash function is deterministic, meaning that it consistently produces the same output for a given input. This property ensures that if the same data is hashed multiple times, the resulting hash will always be identical.
- Fast Computation: Hash functions are designed to be efficient, allowing for quick computation of the hash value from any input data. This efficiency is vital in applications where speed is critical, such as database indexing and data integrity checks.
- Pre-image Resistance: A robust hash function exhibits pre-image resistance, meaning it should be computationally infeasible to reverse-engineer the original input from its hash value. This property safeguards sensitive information by ensuring that even if an attacker obtains the hash, they cannot easily deduce the original data.
- Collision Resistance: Collision resistance refers to the difficulty of finding two different inputs that produce the same hash output. A good cryptographic hash function minimizes the likelihood of collisions, thus maintaining the integrity of the data.
- Avalanche Effect: The avalanche effect is a phenomenon where a small change in the input (even just one bit) results in a significantly different hash output. This property enhances security by ensuring that similar inputs do not yield similar hashes, making it difficult for attackers to predict outputs based on known inputs.
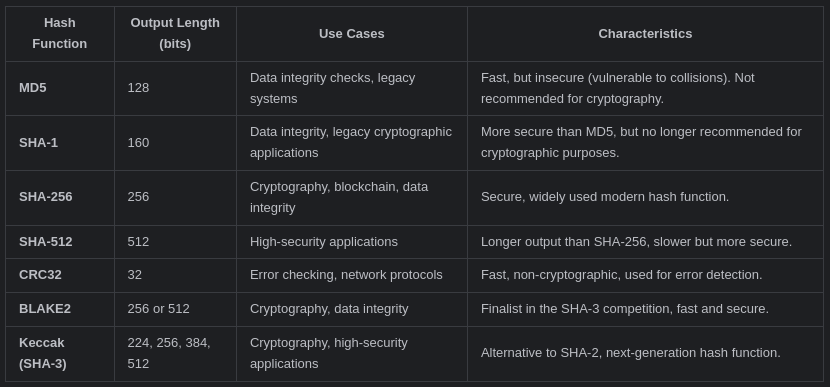
Hashing is widely utilized across various domains, including password storage, digital signatures, data integrity verification, and blockchain technology. Its ability to provide unique and irreversible representations of data makes it an indispensable tool in modern computing and cybersecurity practices.
Project Purpose
The purpose of this project is to create a simple brute-force hash cracker that attempts to guess a password by generating all possible combinations of characters until it finds one that matches a given SHA-256 hash. This exercise will not only enhance your programming skills but also deepen your understanding of how hashes can be exploited if not properly secured.
The project will involve:
- Reading a target SHA-256 hash from user input.
- Accepting a wordlist file containing potential passwords.
- Iterating through each password in the wordlist, hashing it, and comparing it against the target hash.
- Providing real-time feedback on attempts and displaying results once the password is found or all attempts are exhausted.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffeeLet’s Start Writing Our Code
Now that we have a solid understanding of hashing and its implications, let’s break down the implementation of our brute-force hash cracker step by step. This Python script will take a SHA-256 hash and a wordlist file as inputs and attempt to find the corresponding password using brute-force techniques.
1. Importing Required Libraries:
import hashlib
import time
from colorama import Fore, Style, inithashlib: This library provides the hashing functions we need, including SHA-256.time: We use this to simulate a delay in our attempts, which can help in visualizing the progress.colorama: This library allows us to add colored text to our terminal output, enhancing user experience.
2. Defining the HashCracker Class:
class HashCracker:
def __init__(self, target_hash, wordlist_file):
self.target_hash = target_hash
self.wordlist_file = wordlist_file- We define a class called
HashCracker. - The
__init__method initializes two attributes:target_hash: The SHA-256 hash we want to crack.wordlist_file: The path to the file containing potential passwords.
3. Cracking Method:
def crack(self):
"""Attempt to crack the hash using the provided wordlist."""
try:
with open(self.wordlist_file, 'r', encoding='latin-1') as file:
total_attempts = 0
for line in file:
password = line.strip()
hashed_guess = hashlib.sha256(password.encode('latin-1')).hexdigest()
total_attempts += 1
print(f'\r{Fore.YELLOW}Trying: {password} -> {hashed_guess} {Style.RESET_ALL}', end='') # Print on the same line
if hashed_guess == self.target_hash:
return password, total_attempts
time.sleep(0.1) # Simulate some delay for demonstration purposes
except FileNotFoundError:
print(f"{Fore.RED}Wordlist file '{self.wordlist_file}' not found.{Style.RESET_ALL}")
return None, total_attempts
return None, total_attempts- The
crackmethod attempts to find the original password by iterating through each line in the wordlist file. - File Handling:
- We use a
try-exceptblock to handle potential errors, such as the wordlist file not being found. - The file is opened in read mode with
latin-1encoding to handle various characters.
- We use a
- Password Iteration:
- We initialize a counter
total_attemptsto keep track of how many passwords we have tried. - For each line in the file, we strip any whitespace and store it as
password. - We then hash this password using SHA-256 and compare it with the target hash.
- If a match is found, we return the password along with the total number of attempts made.
- We initialize a counter
- Real-time Feedback:
- We print each attempt on the same line using
\r, along with colored output for better visibility. Theend=''parameter prevents adding a new line after each print statement. - A small delay (
time.sleep(0.1)) is included to simulate processing time and make it easier to follow along with attempts.
- We print each attempt on the same line using
4. Error Handling:
except FileNotFoundError:
print(f"{Fore.RED}Wordlist file '{self.wordlist_file}' not found.{Style.RESET_ALL}")
return None, total_attempts- If the specified wordlist file does not exist, an error message is printed in red.
5. Returning Results:
return None, total_attempts- If no match is found after exhausting all passwords in the wordlist, we return
Nonefor the password and the total number of attempts made.
6. Main Execution Block:
if __name__ == "__main__":
init(autoreset=True) # Initialize Colorama with autoreset enabled
target_hash = input("Enter the SHA-256 hash to crack: ")
wordlist_file = input("Enter the path to the wordlist file: ")
cracker = HashCracker(target_hash, wordlist_file)
result, attempts = cracker.crack()
if result:
print(f'\n{Fore.GREEN}Password found: {result} after {attempts} attempts.{Style.RESET_ALL}')
else:
print(f'\n{Fore.RED}Password not found in the wordlist after {attempts} attempts.{Style.RESET_ALL}')- This block checks if the script is being run directly (not imported).
- It initializes
coloramawithautoreset=True, which automatically resets colors after each print statement. - It prompts users for input regarding the target hash and wordlist path.
- An instance of
HashCrackeris created with user inputs, and the cracking process is initiated. - Finally, it prints whether the password was found along with how many attempts were made.
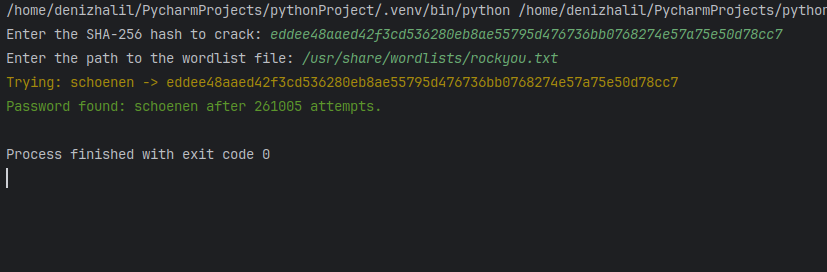
Conclusion
In this article, we explored the concept of hashing and created a simple brute-force hash cracker using Python’s hashlib library. We learned how to implement basic error handling and improve user interaction through colored output and real-time progress updates. Understanding these concepts is crucial for anyone interested in cybersecurity and ethical hacking. As you experiment with this code, consider exploring various enhancements such as optimizing performance or implementing more sophisticated cracking techniques like dictionary attacks or rule-based attacks.
Always remember that while learning about these techniques can be valuable for improving security practices, they should be used responsibly and ethically. Engaging in unauthorized access or attempting to crack hashes without permission is illegal and unethical. Use your skills to enhance security measures rather than exploit vulnerabilities!



Marvelous! Thank you for your content and effort
thank you so much
This is really interesting, You’re a very skilled blogger. I’ve joined your feed and look forward to seeking more of your magnificent post
thank you so much
So, can I get a faster result using the processor and graphics card?
Yes, you can do this by importing specific libraries into this program