Introduction
In today’s digital landscape, cybersecurity has become one of the top priorities for organizations. The increasing complexity of information technology systems and the evolving nature of cyber threats necessitate the identification and remediation of security vulnerabilities. Cyberattacks can lead not only to financial losses but also to reputational damage and a loss of customer trust. In this context, penetration testing (pentesting) emerges as an effective method for assessing an organization’s security posture. This article will provide detailed information on what penetration testing is, the importance of its report template, and an example of such a template.
Learning Objectives
By the end of this article, readers will:
- Understand the fundamental concepts of penetration testing.
- Learn why a penetration testing report is important.
- See how a penetration testing report is structured.
- Examine an example of a report template.
- Evaluate the impact of penetration testing on organizations.
What is Penetration Testing?
Penetration testing is a security assessment method that simulates potential cyberattacks on an organization’s information systems. These tests aim to identify system vulnerabilities and understand how these weaknesses could be exploited by malicious actors. Penetration tests typically involve the following phases:
- Planning: The scope and objectives of the test are defined. This includes determining which systems will be tested, what methods will be used, and what types of data need protection.
- Reconnaissance: Information is gathered about the target systems. Techniques such as network mapping, service discovery, and social engineering are employed to obtain detailed information about the target.
- Exploitation: Identified vulnerabilities are exploited to attempt unauthorized access to the systems. This phase simulates the methods that a real attacker might use.
- Reporting: Findings are documented in detail. The report includes identified vulnerabilities, how they can be exploited, and recommended remediation measures.
This process helps organizations close security gaps and become more resilient against cyberattacks.
Importance of Penetration Testing Reports
A penetration testing report systematically presents the results and findings of the test. The importance of this report stems from several reasons:
- Identification of Security Vulnerabilities: The report details identified security weaknesses, prioritizing each based on its risk level.
- Recommendations: It provides concrete suggestions for remediating vulnerabilities, ranging from technical fixes to policy changes.
- Management Briefing: The report offers summarized information for upper management, facilitating informed strategic decision-making. The executive summary section highlights critical findings along with proposed action plans.
- Compliance: It contributes to meeting regulatory requirements, as many industries mandate regular security assessments by regulatory bodies.
Thus, a penetration testing report is not just a document; it serves as a vital tool for security management.
Example Report Template
A penetration testing report typically consists of the following sections:
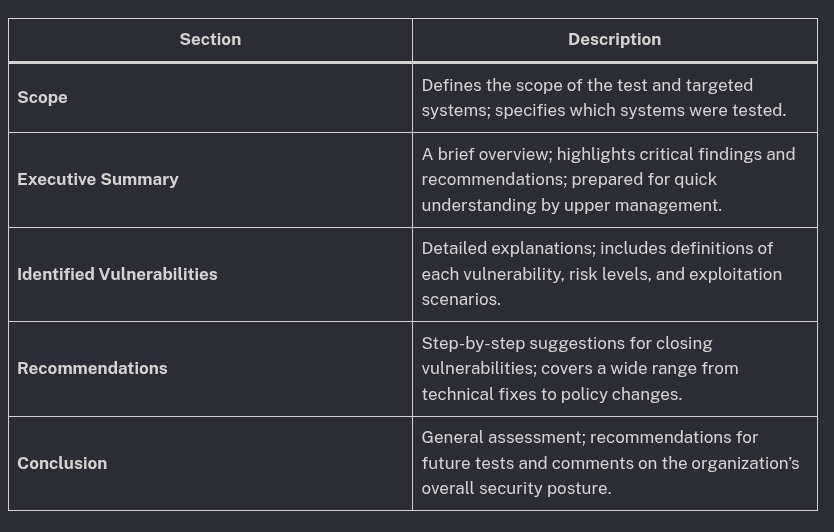
This template facilitates the structuring of the report and ensures that all stakeholders can easily access necessary information.
Conclusion
Penetration testing is crucial for organizations looking to enhance their cybersecurity strategies. These tests help identify security vulnerabilities, implement corrective measures, and prepare for future attacks. Penetration testing reports are essential documents in this process; therefore, creating and utilizing an effective report template is vital for successful cybersecurity management.
In summary, penetration testing is not merely a technical application but also an organizational strategy. Every step taken in identifying and closing security gaps enhances an organization’s overall security and resilience against cyber threats. Organizations should conduct these processes regularly and continuously improve based on the findings obtained from penetration tests to stay ahead in an ever-evolving threat landscape Follow me on Linkedin .


How often should penetration testing be conducted?
Penetration tests should generally be conducted at least once a year, but they may need to be performed more frequently after significant system changes or when new threats emerge.
hey Deniz, your article provides an excellent explanation of the encapsulation concept, supported by relevant examples. The use of both simple and complex examples makes it easier to understand the topic
Hey admin, I think your sources are very good, but are there any other sources you can recommend?
Sure, for example:
Penetration testing reports: A powerful template and guide – hackthebox.com
Free template and guide for writing effective penetration testing reports – underdefense.com
What information should be included in a penetration testing report?
A report should include sections such as scope, findings, recommendations, and an executive summary.