Introduction
In today’s digital landscape, the importance of network security and monitoring cannot be overstated. As organizations increasingly rely on digital communication and data exchange, the volume of sensitive information transmitted over networks has surged. This trend has created a pressing need for effective tools that can analyze network traffic for specific patterns or keywords that may indicate security risks or unauthorized data transmission. In this article, we will explore the development of a Python-based Network Keyword Detection Tool that utilizes the Scapy library to detect keywords in network traffic. This tool is particularly useful for network administrators, security professionals, and anyone interested in monitoring sensitive information flowing through their networks.
Learning Objectives
By the end of this article, readers will:
- Understand the significance of network traffic analysis in maintaining security.
- Learn how to use the Scapy library in Python for packet sniffing and manipulation.
- Gain insights into implementing keyword detection within network packets.
- Familiarize themselves with using command-line arguments for flexible tool configuration.
- Explore how to log detected keywords and relevant packet information for further analysis.
Project Purpose
The primary purpose of this project is to create a keyword detection tool that monitors network traffic and identifies specific keywords within data packets. This tool aims to help users:
- Monitor sensitive information such as passwords, personal identifiers, or confidential data that may be transmitted over the network.
- Analyze network traffic for potential security breaches or unauthorized data transmission attempts.
- Gain insights into the types of data being transmitted over their networks, which can inform security policies and practices.
This tool can serve as an essential component in a broader security strategy, enabling proactive measures to safeguard sensitive information and respond effectively to potential threats.
Let’s Start Writing Our Code
Below is the complete Python code for our network keyword detection tool using Scapy, divided into sections for clarity.
1. Importing Necessary Libraries
First, we need to import the required libraries:
import argparse
import re
import datetime
from scapy.all import sniff, IP, TCP, UDP
from colorama import Fore, Style- argparse: This library is used for parsing command-line arguments, allowing users to specify parameters such as the network interface and keywords directly from the command line.
- re: The regular expression library provides support for pattern matching, which is essential for detecting keywords within packet payloads.
- datetime: This library is used to timestamp log entries, providing context about when specific keywords were detected.
- scapy.all: This module imports essential functions and classes from the Scapy library, which is a powerful tool for packet manipulation and analysis.
- colorama: This library enables colored output in the terminal, enhancing the visibility of important messages such as detected keywords or errors.
2. Defining the KeywordDetector Class
Next, we define a class that encapsulates all functionalities related to keyword detection:
class KeywordDetector:
def __init__(self, interface, keywords):
self.interface = interface
self.keywords = keywords
self.log_file = "keyword_log.txt"- The
__init__method initializes the class with two key attributes:interface, which specifies the network interface to monitor (e.g., ‘wlan0’), andkeywords, which is a list of keywords that we want to detect in the traffic. Additionally, it sets up a log file name where detected keywords will be recorded.
3. Logging Detected Keywords
We create a method to log information whenever a keyword is found:
def log_keyword_found(self, keyword, payload, packet):
"""Create a log entry when a keyword is found."""
with open(self.log_file, "a") as f:
timestamp = datetime.datetime.now().strftime("%Y-%m-%d %H:%M:%S")
f.write(f"{timestamp} - Keyword found: {keyword}\n")
f.write(f"Packet: {payload}\n")
f.write(f"Source IP: {packet[IP].src}, Destination IP: {packet[IP].dst}\n")
f.write(f"Protocol: {packet[IP].proto}\n\n")- This method appends a new entry to the log file whenever a keyword is detected. The log entry includes several important pieces of information:
- Timestamp: Indicates when the keyword was found.
- Keyword Found: Displays the actual keyword that triggered the logging.
- Packet Data: Shows the content of the packet where the keyword was found.
- Source and Destination IP Addresses: Provides context about where the packet originated and where it was headed.
- Protocol Used: Identifies whether the packet used TCP or UDP.
This logging functionality is crucial for post-analysis and auditing purposes.
4. Processing Incoming Packets
The next method processes each packet received:
def packet_callback(self, packet):
"""Callback function called for each packet received."""
if packet.haslayer("Raw") and packet.haslayer(IP):
try:
payload = packet["Raw"].load.decode(errors='ignore')
src_ip = packet[IP].src
dst_ip = packet[IP].dst
protocol = self.get_protocol(packet)
for keyword in self.keywords:
if re.search(re.escape(keyword), payload, re.IGNORECASE):
print(f"{Fore.GREEN}Keyword found: {keyword}{Style.RESET_ALL} - Packet: {payload}")
print(f"{Fore.CYAN}Source IP: {src_ip}, Destination IP: {dst_ip}, Protocol: {protocol}{Style.RESET_ALL}")
self.log_keyword_found(keyword, payload, packet)
except Exception as e:
print(f"{Fore.RED}Error: {e}{Style.RESET_ALL}")- The
packet_callbackmethod checks if an incoming packet has both a raw layer (which contains data) and an IP layer (which provides routing information). If both conditions are met:- It decodes the payload (the actual data contained in the packet) while handling any decoding errors gracefully.
- Retrieves source and destination IP addresses from the IP layer.
- Calls
get_protocolto determine whether TCP or UDP was used.
For each keyword specified by the user:
- If it matches any part of the payload (case-insensitively), relevant information is printed to the console using colored output for better visibility.
- The method also logs this information using
log_keyword_found.
This real-time feedback allows users to monitor their networks actively.
5. Determining Packet Protocol
We define a method to identify the protocol of each packet:
def get_protocol(self, packet):
"""Determine the protocol of the packet."""
if packet.haslayer(TCP):
return "TCP"
elif packet.haslayer(UDP):
if packet.haslayer(DNS):
return "DNS"
return "UDP"
elif packet.haslayer(ICMP):
return "ICMP"
else:
return "Other"- This method checks whether a TCP or UDP layer exists within the packet. If neither layer is present, it returns “Other,” indicating that some other protocol is being used.
Understanding which protocol is being used can provide insights into how data flows through your network.
6. Starting Packet Sniffing
Now we implement the method that starts sniffing packets:
def start_sniffing(self):
"""Start sniffing packets."""
print(f"{Fore.BLUE}Starting sniffing on: {self.interface}{Style.RESET_ALL}")
sniff(iface=self.interface, prn=self.packet_callback, store=0)- The
start_sniffingmethod begins monitoring traffic on the specified network interface. It uses Scapy’ssnifffunction to capture packets continuously:- The
ifaceparameter specifies which network interface to listen on. - The
prnparameter indicates that each captured packet should be passed to ourpacket_callbackfunction for processing. - Setting
store=0ensures that packets are not stored in memory after processing them.
- The
This method effectively puts our tool into action.
7. Main Function
Finally, we define our main function that sets up command-line argument parsing:
def main():
"""Main function."""
parser = argparse.ArgumentParser(description="A tool to detect keywords in network traffic.")
parser.add_argument("-i", "--interface", required=True, help="Network interface to listen on (e.g., 'wlan0').")
parser.add_argument("-k", "--keywords", nargs='+', required=True, help="Keywords to detect (space-separated).")
args = parser.parse_args()
detector = KeywordDetector(args.interface, args.keywords)
detector.start_sniffing()- The
mainfunction usesargparseto allow users to specify input parameters directly from the command line:- The
-ior--interfaceargument specifies which network interface should be monitored. - The
-kor--keywordsargument allows users to input multiple keywords they wish to detect within packets.
- The
After parsing these arguments:
- An instance of
KeywordDetectoris created with user-defined parameters. - Finally, it calls
start_sniffing()on this instance to initiate monitoring.
8. Entry Point
Lastly, we ensure that our script runs only when executed directly:
if __name__ == "__main__":
main()This conditional statement checks if this script is being run as a standalone program rather than being imported as a module in another script.
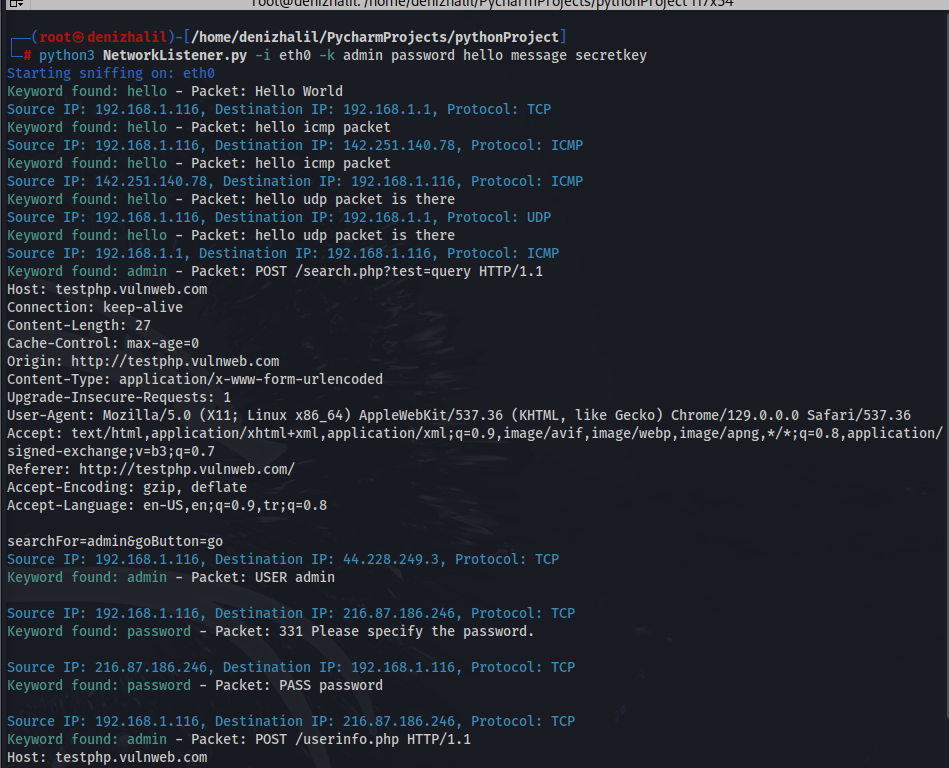
Conclusion
In this article, we developed a Python-based tool that detects specific keywords in network traffic using Scapy. By leveraging this tool effectively, network administrators can monitor sensitive information such as passwords or personal identifiers while enhancing their overall security practices. The implementation of command-line arguments allows users to customize their monitoring experience easily by specifying different interfaces and keywords as needed.
As cyber threats continue to evolve and become more sophisticated, tools like this will play an increasingly critical role in maintaining secure networks. By proactively monitoring traffic for sensitive data patterns and potential breaches, organizations can better protect their assets and respond swiftly to emerging threats. This project not only serves as an educational exercise but also provides practical utility in real-world scenarios where data privacy and security are paramount concerns.
Mastering Scapy: A Comprehensive Guide to Network Analysis
Mastering Network Analysis with Scapy” is not just about learning a tool; it’s about unlocking a deeper understanding of the digital world that surrounds us
-5% $20 on buymeacoffeeArticles That May Interest You



This network keyword detection tool is incredibly useful for monitoring sensitive information in real-time. Great job on the implementation!
The article provides clear and concise instructions on how to use Scapy for packet sniffing. I appreciate the detailed code examples!
Since I am a student, can I buy your book at a slightly cheaper price?
Sure, here you go, 50% discount code limited to 15 people: EFKPI4P9
What types of keywords can be detected using this tool?
In fact, the tool is designed to include any text string specified by the user as a keyword, including sensitive information such as passwords, personal identifiers or other confidential data. But if you are new to this, I recommend you to get Denizhalil’s 0 to Advanced Python and Mastering Scapy books.
Thank you so much, Here yougo 50% discount code: EFKPI4P9 😀
How can I modify the code to filter packets based on specific IP addresses?
This modification checks if the source IP address of incoming packets is within an allowed list before processing them further.