Introduction
Network security and analysis have become more critical than ever in today’s information technology landscape. Network administrators and security experts rely on various tools to effectively monitor and understand the traffic on their networks. In this article, we will explore how to sniff and analyze ARP (Address Resolution Protocol) traffic using Scapy, a Python-based network packet manipulation library.
Learning Objectives
By the end of this article, you will:
- Learn how to use the Scapy library.
- Understand the basic functions of the ARP protocol.
- Be able to create a Python class to sniff and analyze ARP traffic by specifying a network interface.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $13 on buymeacoffeeWhat is the ARP Protocol?
ARP is a fundamental protocol that resolves IP addresses to physical MAC (Media Access Control) addresses. It enables devices on a local network to find and communicate with each other. ARP packets are typically classified into two types: ARP requests and ARP replies. The ARP protocol plays a crucial role in facilitating communication between devices on the network.
Purpose of the Project
The goal of this project is to develop a Python class that uses Scapy to sniff and analyze ARP traffic. This class will display ARP requests and replies in color on the screen. Additionally, it will allow you to select the interface for sniffing via command-line arguments using the argparse library and will use the colorama library to color the output.
Let’s Start Coding
Step 1: Installing Required Libraries First, ensure that you have the Scapy, argparse, and colorama libraries installed:
$ pip3 install scapy coloramaStep 2: ARP Sniffing with Python Class
In this step, we will break down the class structure developed for sniffing and analyzing network traffic.
1. Importing Required Libraries We start by importing the argparse, scapy, and colorama libraries. These libraries will be used for processing command-line arguments, sniffing network packets, and coloring terminal output, respectively.
import argparse
from scapy.all import ARP, sniff
from colorama import init, Fore, Style2. Initializing the Colorama Library We initialize the Colorama library for Windows compatibility. This ensures that colored output is displayed correctly
# Colorama initialization for Windows compatibility
init(autoreset=True)3. Defining the ARPSniffer Class This class will be used to specify the network interface and to sniff ARP packets
Mastering Advanced Python from Scratch to Advanced
Unlock the full potential of Python with this comprehensive guide, spanning 227 pages and 50 chapters. From advanced techniques like metaprogramming.
-5% 25 on buymeacoffeeclass ARPSniffer:
def __init__(self, interface):
self.interface = interface4. Defining the arp_sniffer Function This function checks ARP packets and displays ARP requests and replies in color on the screen.
def arp_sniffer(self, packet):
if packet.haslayer(ARP):
if packet[ARP].op == 1: # ARP Request
print(Fore.YELLOW + f"[ARP Request] {packet[ARP].psrc} is asking about {packet[ARP].pdst}")
elif packet[ARP].op == 2: # ARP Reply
print(Fore.GREEN + f"[ARP Reply] {packet[ARP].hwsrc} has address {packet[ARP].psrc}")5. Defining the start_sniffing Function This function starts sniffing ARP packets on the specified network interface and processes them using the arp_sniffer function.
def start_sniffing(self):
print(Fore.CYAN + Style.BRIGHT + f"Starting ARP sniffing on interface {self.interface}...\n")
sniff(iface=self.interface, filter="arp", prn=self.arp_sniffer)6. Handling Command-Line Arguments with argparse Here, we process command-line arguments to determine the network interface on which to sniff.
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="ARP Sniffer using Scapy")
parser.add_argument("-i", "--interface", required=True, help="Network interface to sniff on")
args = parser.parse_args()7. Running the ARPSniffer Class Finally, we instantiate the ARPSniffer class with the provided network interface argument and start sniffing for ARP traffic.
sniffer = ARPSniffer(args.interface)
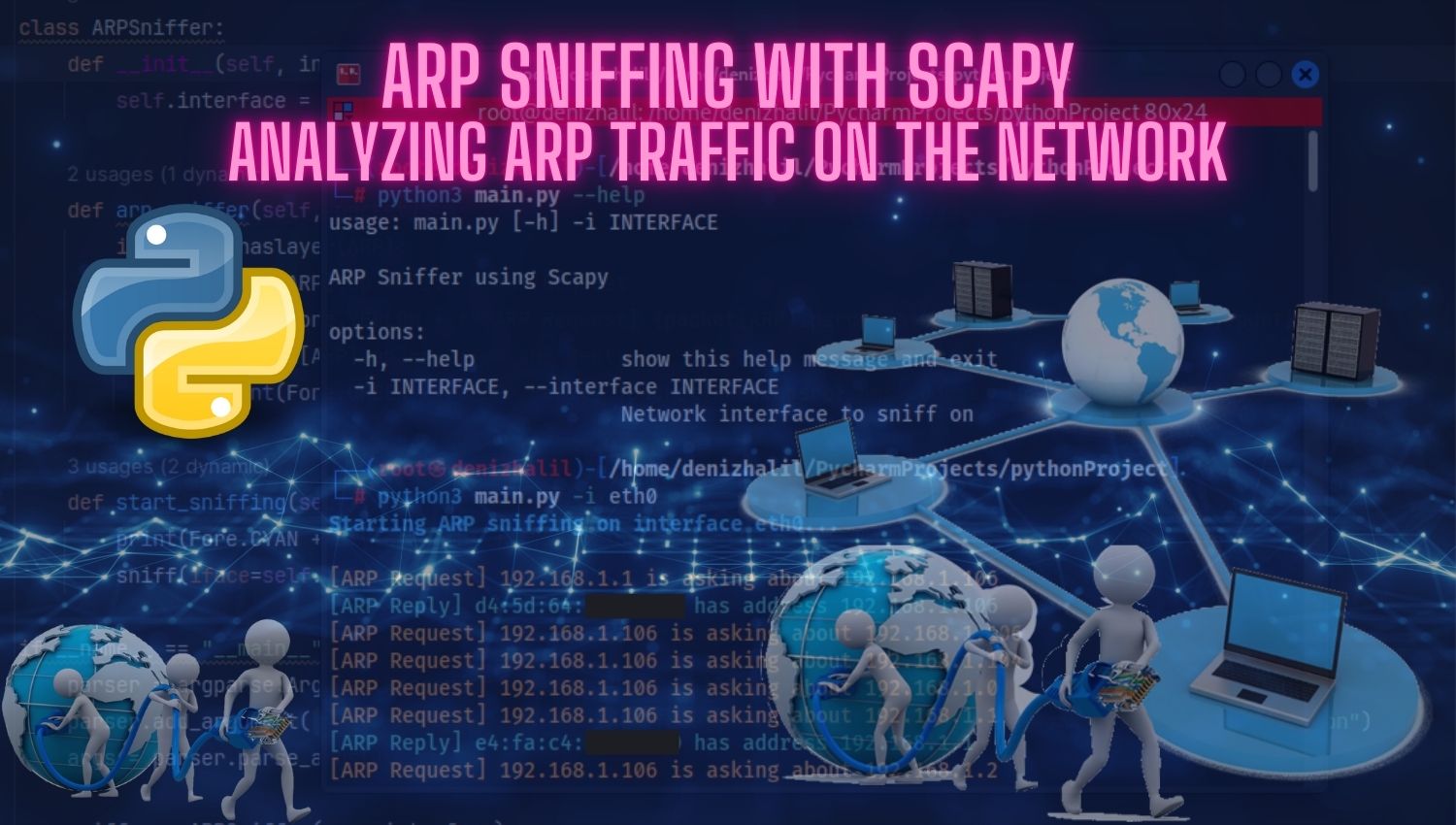
sniffer.start_sniffing()The above Python code creates a class named ARPSniffer that listens on the specified network interface and displays ARP traffic in color on the screen.
Step 3: Running the Code To run your code, use the following command in your terminal:

Conclusion
In this article, we learned how to sniff and analyze ARP traffic using Scapy. Monitoring network traffic helps network administrators and security experts gain a better understanding of their networks and enhance their security. However, it’s important to adhere to legal and ethical guidelines when using such tools. One should be cautious and prepared for potential security risks when performing such analyses.
Mastering Scapy: A Comprehensive Guide to Network Analysis
Mastering Network Analysis with Scapy” is not just about learning a tool; it’s about unlocking a deeper understanding of the digital world that surrounds us
-5% $20 on buymeacoffeeContinuous learning and practice in network security provide a significant advantage for those looking to deepen their knowledge in this field. Tools like Scapy are excellent starting points for those interested in gaining insights into network security



Hey man, great project as always, I saw your article before but I think I updated the old version, it’s very nice
this is really a great article you should definitely create a course on udemy, i am also one of the buymeacoffee members, the projects are great
Your networking work is really incredible, could you do a little cryptology work as well?
In item 7, move the sniffer variable forward by 1 tab if you get an error.
Hey admin,
the code you wrote looks really cool. Can you write similar codes for other protocols?
This article is an excellent resource for anyone looking to analyze ARP traffic using Scapy. The detailed explanations of code snippets and step-by-step instructions make it a clear guide for both beginners and experienced users. The insights on how to use colorama for colored output are particularly useful. Thank you for the great work
While the article is informative, it lacks information on some common issues encountered during ARP traffic analysis or possible improvements. For instance, insights on detecting ARP spoofing attacks or preventive measures would enhance the content. Adding a section on these aspects could address this gap