Introduction
In today’s interconnected world, computer networks form the backbone of data transmission across the globe. Within these networks, vast amounts of data are constantly being exchanged. Understanding network traffic is crucial for various applications, including network security, troubleshooting, and monitoring network performance. Scapy, an open-source Python library, provides a powerful toolset for manipulating network protocols. In this article, we will introduce you to the basics of monitoring network traffic using Scapy and guide you through an enhanced code example.
Learning Objectives
- Understand the basics of network traffic monitoring with Scapy.
- Implement a network traffic monitoring tool using Python.
- Use
argparseto handle user inputs for dynamic configurations. - Enhance the output with
coloramafor better readability.
Purpose of This Project
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffeeThe primary goal of this project is to develop a Python-based tool for monitoring network traffic using the Scapy library. This tool is designed to achieve several objectives:
- Real-Time Network Monitoring: The tool captures and analyzes network packets in real-time, providing immediate insights into network traffic. This is crucial for identifying and troubleshooting network issues as they occur.
- Packet Filtering: By allowing users to specify a particular network interface and port number, the tool enables targeted monitoring. This means users can focus on specific types of traffic or network segments that are of particular interest, reducing the volume of data to analyze and increasing the relevance of the results, DNS Security Tool: Monitoring and Detecting DDoS/DoS Attacks with Python.
- Enhanced Output Readability: Using the
coloramalibrary, the tool improves the readability of the output by color-coding different types of network packets. This visual enhancement helps users quickly identify and differentiate between TCP and UDP packets, as well as their source and destination details. - Educational Value: The project serves as an educational example for those interested in network security and traffic analysis. It demonstrates how to utilize Scapy for practical purposes, and how to integrate additional Python libraries to enhance functionality and user experience.
- Flexible Configuration: Incorporating
argparseallows users to customize the tool’s behavior through command-line arguments. This flexibility enables users to adapt the tool to different network environments and monitoring requirements without modifying the code. - Foundation for Advanced Projects: The tool provides a solid foundation for more complex network monitoring and analysis projects. Users can extend the code to include additional features, such as more detailed packet analysis, logging capabilities, or integration with other network security tools.
By addressing these objectives, the project not only provides a practical solution for real-time network traffic monitoring but also contributes to the broader understanding of network analysis techniques and tool development.
Let’s Start Coding
We will develop a Python tool using Scapy for network traffic monitoring. This tool will allow users to specify the network interface and optionally filter traffic by port. We will also use colorama to enhance the output with color for better readability. Let’s break down the code into manageable parts, Network Traffic Monitoring and SSH Detection with Python:
1. Importing Libraries
import argparse
from scapy.all import sniff, IP, TCP, UDP
from colorama import Fore, Style, initargparse: A library for parsing command-line arguments.scapy.all: Imports Scapy functions and classes for network packet manipulation.colorama: Provides color and style options for terminal text.
2. Define the TrafficMonitor Class
init()
class TrafficMonitor:
def __init__(self, interface, port):
self.interface = interface
self.port = port__init__: Initializes theTrafficMonitorclass with the network interface and port number. These will be used to capture and filter packets. Initializescoloramato enable colored output in the terminal.
Mastering Scapy: A Comprehensive Guide to Network Analysis
Mastering Network Analysis with Scapy” is not just about learning a tool; it’s about unlocking a deeper understanding of the digital world that surrounds us
-5% $20 on buymeacoffee3. Define the packet_handler Method
def packet_handler(self, packet):
if packet.haslayer(IP):
ip_layer = packet[IP]
src_ip = ip_layer.src
dst_ip = ip_layer.dst
# Check for TCP or UDP layer and filter by port
if packet.haslayer(TCP):
if self.port is None or packet[TCP].sport == self.port or packet[TCP].dport == self.port:
print(
f"{Fore.CYAN}TCP Packet - Source IP: {src_ip}, Source Port: {packet[TCP].sport}, Destination IP: {dst_ip}, Destination Port: {packet[TCP].dport}{Style.RESET_ALL}")
elif packet.haslayer(UDP):
if self.port is None or packet[UDP].sport == self.port or packet[UDP].dport == self.port:
print(
f"{Fore.BLUE}UDP Packet - Source IP: {src_ip}, Source Port: {packet[UDP].sport}, Destination IP: {dst_ip}, Destination Port: {packet[UDP].dport}{Style.RESET_ALL}")packet_handler: This method processes each captured packet.if packet.haslayer(IP): Checks if the packet contains an IP layer.ip_layer = packet[IP]: Extracts the IP layer.src_ipanddst_ip: Extracts source and destination IP addresses.- Checks for TCP and UDP layers: Filters packets based on whether they are TCP or UDP and compares their ports if specified.
4. Define the start_monitoring Method
def start_monitoring(self):
print(f"{Fore.YELLOW}Starting packet capture on interface: {self.interface}, monitoring port: {self.port if self.port else 'All ports'}...{Style.RESET_ALL}")
sniff(iface=self.interface, prn=self.packet_handler)start_monitoring: Starts the packet capture process.print: Outputs a message indicating the start of monitoring.sniff: Begins capturing packets on the specified network interface and usespacket_handlerto process each packet, Port Scanning Techniques with Scapy.
5. Main Execution Block
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="Network Traffic Monitoring Tool")
parser.add_argument("-i", "--interface", type=str, required=True, help="Network interface to listen on")
parser.add_argument("-p", "--port", type=int, help="Port number to filter traffic")
args = parser.parse_args()
monitor = TrafficMonitor(interface=args.interface, port=args.port)
monitor.start_monitoring()if __name__ == "__main__": Ensures the code runs only if the script is executed directly.argparse.ArgumentParser: Creates a command-line argument parser.parser.add_argument: Defines arguments for specifying the network interface and port.args: Parses the command-line arguments.monitor: Creates an instance ofTrafficMonitorwith the provided arguments.monitor.start_monitoring(): Starts the network traffic monitoring.
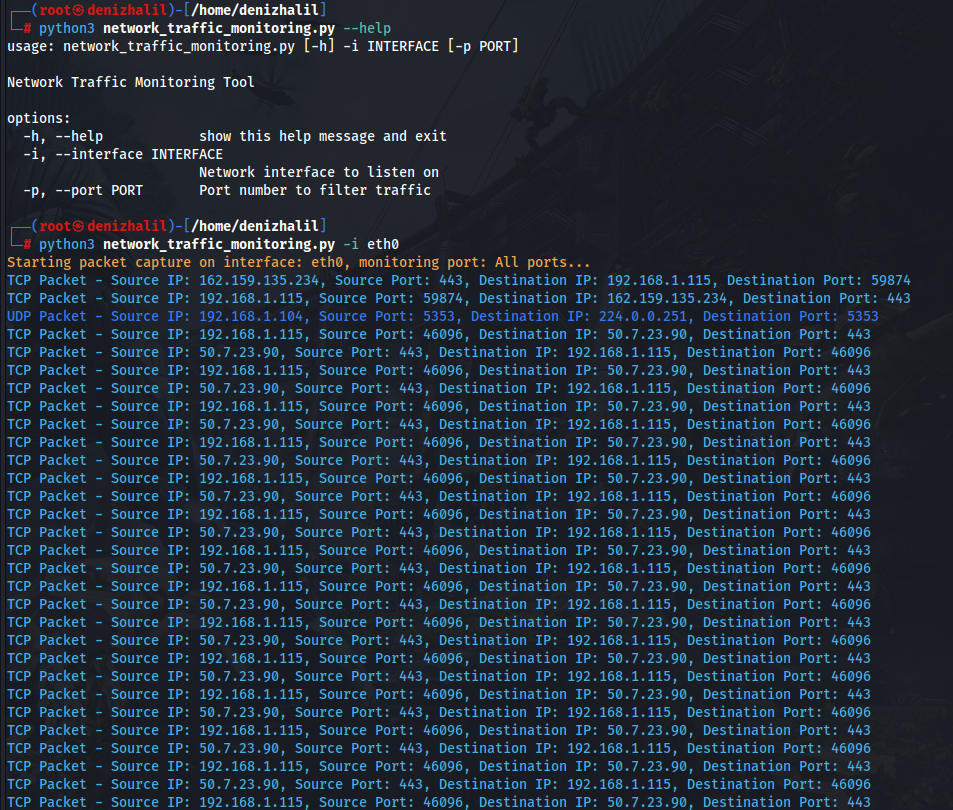
Conclusion
Mastering Advanced Python from Scratch to Advanced
Unlock the full potential of Python with this comprehensive guide, spanning 227 pages and 50 chapters. From advanced techniques like metaprogramming.
-5% 30 on buymeacoffeeIn this article, we expanded on monitoring network traffic using Scapy by enhancing the tool with user input capabilities and colored output. The updated code demonstrates how to incorporate argparse for dynamic configuration and colorama for improved readability. This tool serves as a foundational step for more advanced network monitoring and analysis projects. Network traffic monitoring remains a critical component of network management, and Scapy provides a versatile platform for these tasks. Explore and build upon this tool to suit your needs in network security and performance monitoring.




thank you for sharing
Excellent article! The insights on monitoring network traffic with Scapy and the provided code example were very helpful. The use of colorama to add color to the output is a great touch. I tested the code and got successful results. Thanks for the informative guide
It would be great if you could publish a new article listening to the package content in your next article.
color output is great
This module is really great, a module that every hacker and network expert should know.
Your article provided a solid foundation for Scapy-based network traffic monitoring. The concise explanations made it easy to understand each part of the code. The option to filter by a specific port was particularly valuable. Looking forward to more content from you
This article is a perfect resource for those wanting to learn about network security. The details on using argparse were particularly insightful. I have some ideas on how to extend the code with more complex features. This article was truly educational for me
The example code provided in the article performs basic packet monitoring, but it could benefit from adding more complex analysis and reporting features, such as detailed packet content analysis or traffic volume reporting.
The purpose of keeping the code at a basic level is to appeal to a broad audience and provide fundamental functionality. Advanced analysis and reporting features can be addressed in a more extensive project or future articles.
How can we differentiate more between TCP and UDP packets? Is it possible to perform more detailed analyses for specific protocols?
To make more distinctions between TCP and UDP packets, you can add additional filtering criteria. For example, you can check specific flags or data lengths to perform more detailed analyses.
The use of argparse is good, but the interface could be simplified for some users. For instance, adding a GUI-based tool or a more user-friendly configuration interface might be helpful.