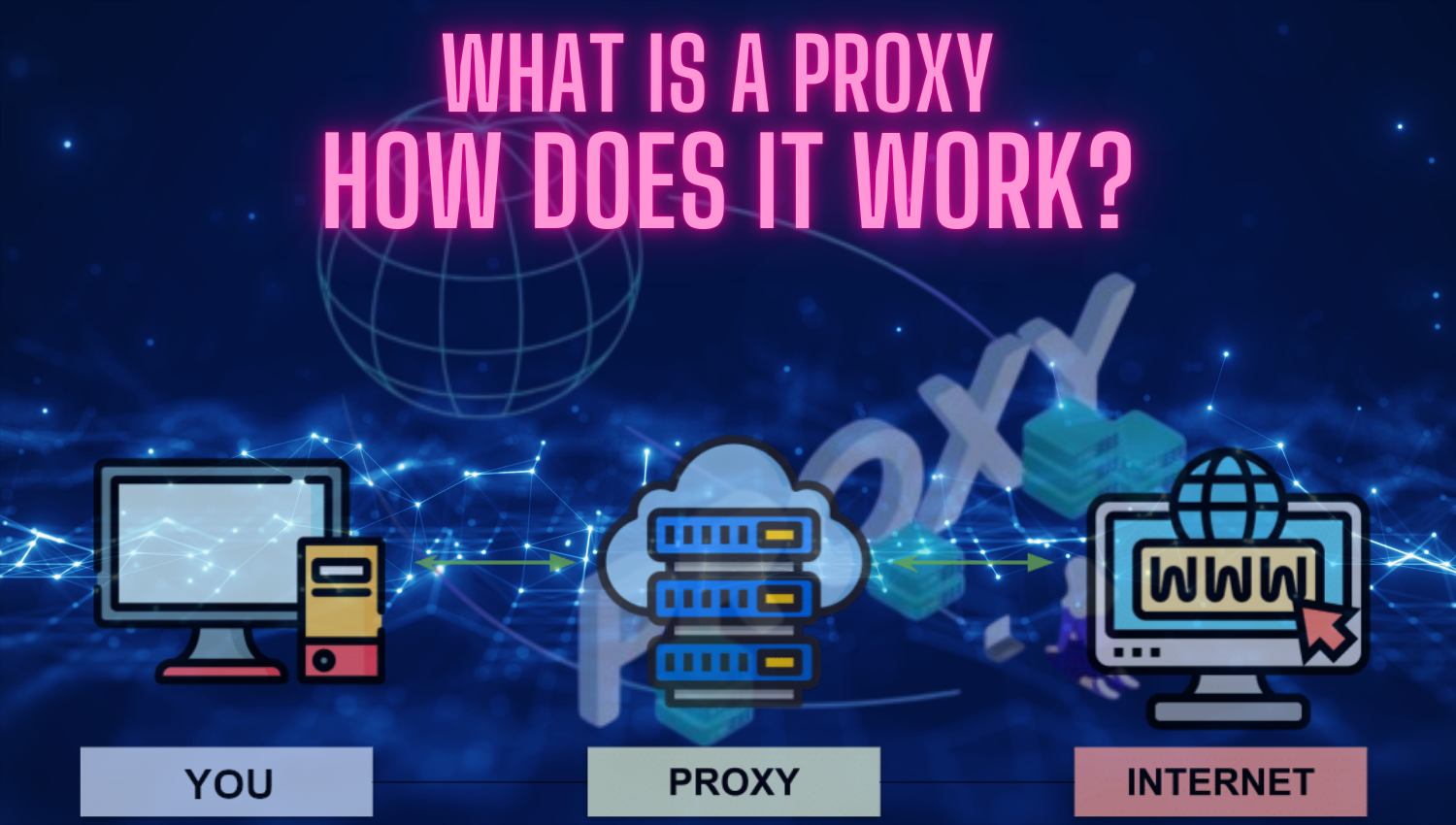
SSH Tunneling and Port Forwarding Techniques: A Comprehensive Guide
Introduction SSH (Secure Shell) tunneling and port forwarding have become indispensable tools for system administrators, cybersecurity professionals, and developers worldwide. In an era where network security threats continuously evolve and data breaches occur with alarming frequency, the ability to create secure encrypted channels for data transmission has never been more critical. SSH tunneling transforms the ubiquitous SSH protocol from a simple remote